1. Introduction
Blockchain technology has a huge potential with various applications as well as provides numerous opportunities for different infrastructure. The technology promotes management of resources besides making communication secure as well as efficient. Trust, reliance and privacy are enhanced when carrying out financial transactions among different parties with the use of blockchain. This is because the technology lowers the likelihood of fraud and automatically generates a record of activities, including creating an automated background check of a member using the system (Aitzhan & Svetinovic 2016). As a result of the decentralized features, blockchain results in increased reliability besides lowering the risks that are experienced when looking to enter into a business agreement with an unfamiliar person or party.
At the moment, almost everyone is using advanced technology for the purposes of communication via the internet. Voice calls, messages, video calls, pictures are currently able to directly travel from the sender to the receiver over the internet regardless of their geographical location. For the case of such a transaction, a trusted third party must be maintained between the receiver and the sender (Bach, Mihaljevic & Zagar 2018). When it comes to the case of transfer of money, a third party has to be trusted to allow completion of the transaction. But with the use of blockchain, a perfect security would be availed for the transaction.
2. Literature Review
2.1. Analysis of Blockchain Security
With the advent of blockchain technology being widely adopted, numerous and different kinds of attacks have been established. Such cases include theft or loss of billions of digital currencies and attack of various exchanges, among other events. Based on the data released by BCSEC (a blockchain security company based in China), 2018 recorded an increased number of blockchain security incidents that resulted to economic losses of approximately 2.1 billion dollars. The number of blockchain security events increased from 15 in 2017 to 138 in 2018. These are just part of the exposed incidents as the number of attacks are projected to be on the increase with the increasing worth and application of blockchain (Banerjee, Lee & Choo 2018).
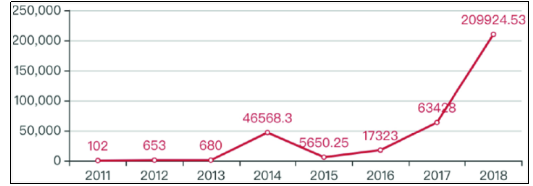
Figure 1: Economic losses as a result of blockchain security issues (’10,000) (Wang et al. 2019)
Notwithstanding the fact that blockchain technology remains in the early stages of rapid expansion and the various security accidents experienced so far have made security features to be very essential requirements in the development of blockchain systems. The security risk could be from external attackers or even internal parties. The acceptance, popularity and potential of blockchain renders fresh demands on the security as well as protection of privacy on the storage, application as well as transmission of data alongside putting forth new challenges to the prevailing solutions of security, mechanisms of authentication, protection of privacy, and protection of data alongside information regulation (Dorri et al. 2017).
2.2. Security Analysis of Individual Blockchain Layers
The present structure of blockchain may be separated into the following layers: application, incentive, smart contract, network, consensus, as well as data layers (not in their systematic order). The analysis of security aspect of each of the aforementioned layers is done
2.2.1. Application layer
The main function of this layer is to cover matters of security of centralized nodes, which includes exchanges involving transactions of digital currencies as well as management of huge volumes of funds. Such nodes are present at most of the failure points of the full blockchain system and the vulnerability of attacks is often high whereas the cost is relatively low. A combination of these characteristics usually make the layer a preferred target of many attackers.
Exchange DDoS: as a result of the network bandwidth demand being high especially in the trading arena, occurrence of a DDoS attack makes it a very serious issue not only for the arena but also for the whole industry. Should the trading arena attack be by DDoS, the arena will not only incur losses but also a great reduction in the volume of the transactions involving blockchain currency which would in turn have an indirect impact on the increase and decrease of the value of blockchain currency (Eyal et al. 2016).
Illegal access to exchange severs: exchanges are where lump sum amount of money are normally deposited thus making them an easy target for attackers. As soon as the attackers get the server authority (access the exchange server illegally), they immediately modify its main information. Thereafter, the attackers can be able to abscond with the funds key, interfere with the amounts being transacted or even leak very confidential and information, resulting in huge economic as well as reputational devastating effects to exchange.
Infection by malicious program: as soon as a malicious program has been planted into an exchange system, it is most likely to result in large volumes of leakage of sensitive information among them key as well as wallet files. The key tends to be everything, and once the sensitive information is leaked, it normally means that the exchange company loses control over all the assets (Heilman, Baldimtsi & Goldberg 2016). In 2014, the Mt. Gox exchange experienced an attack. The institution’s key file had been kept locally in clear manuscript and there was leakage of key file wallet.dat as a result of infection by Trojan leading to loss of large volumes of assets that rendered Mt. Gox bankrupt. It is of importance to acknowledge that the attacker used two years in slowly transferring asset in a bid to avoid recovery of the loss by the community through hard forks in the attack.
2.2.2. Smart Contract layer
This is not merely a computer program which may be automatically executed, instead it is a participant of the system. This layer is responsive to received messages and may receive as well as store value besides sending out value and information. The smart contracts have numerous security attacks, including the following:
Re-entrancy Attack: this attack is based on the concept of hijacking the control flow of the contract and destruction of the atomicity of transaction that may be comprehended as a logical race condition challenge (Kakavand, Kost De Sevres & Chilton 2017). DAO was for instance attacked in which the attacker adopted vulnerability in the contract in launching a re-entrancy attack and ended up gaining $60 million. In a bid to recover the funds lost, a decision was made by Ethereum community to conduct a hard fork, reversing all transaction records from the beginning of the attack as well as fixing the susceptibilities in new contract branch. Below is the description of the susceptibility and a basic variety of the DAO contract.
Solidity development security: there are several possible bugs that can arise when smart contracts are being written. Some of these include the following:
Race condition – one of the major risks that may result when a peripheral function gets called is that the behaviour of calling may result to the control flow being hijacked, thus creating chances for the unintended alteration of the contract data. This kind of bug can come in different forms including re-entrant as well as cross-function race conditions (Karame 2016).
Integer underflow and overflow: during programing, one should think of the possibilities of occurrence of an overflow, how transfer of the state of unit variables will be done as well as who bears the authority of modifying such variables.
Transaction-ordering dependence: this is where an attacker creates his own transaction by using information in the incomplete transactions and attempt to get the transaction that he has created to be completed ahead of others.
2.2.3. Incentive layer
This layer’s role is to provide particular incentives that are aimed at encouraging nodes to take part in security verification process of the blockchain technology. The safety of the blockchain is a factor of the participation of the numerous nodes. For instance, the bitcoin blockchain security is dependent on great harsh power that is created through participation of numerous nodes that are involved in various security checks and proofs, rendering it not possible for an attacker to offer a greater volume of totalling (Khan & Salah 2018). The process of verification done by any node often consumes electric power as well as computing resources. Encouraging node participation is attained through reward of participants by the blockchain in the nature of cryptocurrency (virtual currency).
It is required of blockchain projects to acclimate to the market so that they adjust the rewards automatically as opposed to just reducing them. When the working cost of the node is proximate or higher than the income in the reward mechanism of blockchain project, they normally decide to stop working for such blockchain that may easily result in centralization issues.
2.2.4. Consensus Layer
The mechanisms of consensus is the core element that makes blockchain different from other P2P (peer-to-peer) technologies. The consensus mechanisms that are widely adopted include: Proof of Work (PoW), Delegated Proof of Stake (DPoS) and Proof of Stake (PoS). On the other hand, some of the likely attacks include Long-Rang Attack, Bribe Attack, Bribe Attack, Accumulation Attack, Sybil Attack as well as Precompiling Attack. The attack methods and their respective consensus mechanisms are presented in Table 1 below
Table 1: Attack methods and consensus mechanism
2.2.5. Network layer
The transmission of blockchain information majorly relies on the P2P network which depends on adjacent nodes for transmitting information where it has to be exposing the IP of each other. In case of an attacker in the network, bringing security threats to the other nodes tends to be quite simple (Li et al. 2017). The public blockchain network node could be a conventional home personal computer or even a cloud server among others and the security has to be irregular. A node must be there having poor security and when it gets attacked, the other nodes will be directly threatened. Among the major attacks include: eclipse attack and BGP hijacking.
2.2.6. Data layer
The main elements of data layer are block data and signature & encryption system.
Bloc data: this is mainly attacked by malicious information, for instance, subjects that are deemed to be politically sensitive and virus signatures present in the blockchain. Deleting any information from the blockchain after it has been written is very challenging due to the presence of data undelete feature. This means that users need to ensure that they write accurate information in the blockchain. In case the blockchain contains malicious information, the blockchain will be exposed to numerous hitches.
It was pointed out by a group of researchers from the RTWH Aachen University as well as the Goethe University Frankfurt that out of the 1,600 documents that are included in the Bitcoin blockchain, about 59 files were associated with illegal pictures of children as well as privacy violations and content deemed to be politically sensitive (Lin & Liao 2017). Approximately 1.4 per cent of the about 251 million transaction of the bitcoin blockchain is composed of other data. This means that only a small percentage of these transactions composed of unwanted or unlawful content. However, it is worth noting that even such a small percentage of unwanted or unlawful content can still put expose blockchain partakers to security risks.
Signature & encryption system: cryptography is the main element for ascertaining security and interfering with blockchain resistance, and blockchain technology depends mainly on research outcomes of crystography that offers a main assurance for the blockchain’s integrity of the information, verification as well as non-repudiation. The encryption technology is of specific importance as a backbone of blockchain. For instance, the hash algorithms of SHA1 and MD5 were very popular in the preceding years but failed to prove that they were insufficiently secure. Currently, the widely used algorithm in bitcoin is that of SHA256. Pass, Seeman & Shelat 2017). Up to date, this algorithm has proved to be secure but with the ongoing technological development and advancement research, the future safety of this algorithm cannot be accurately predicted or guaranteed. Hence, when blockchain applications are being designed, it is important to select the encryption system more carefully because of its safety and security implications on blockchain. Current methods of mainstream signature are inclusive of group signature, aggregate signature, proxy signature, blind signature, ring signature, blinded verifiable encrypted signature as well as interactive incontestable signature, among others.
2.3. Blockchain security features
Use ledger: ledger ought to record every blockchain transaction. The ledger is not mutable. It may not be possible to edit or even delete the available data. In blockchain technology, this kind of ledger is decentralized application. As a result, no one is able to access the transaction details or any other data that is deemed to be sensitive from the ledger (Tosh et al. 2017). People are only able to read the information contained in the leger but cannot change it.
Chain of block is yet another security feature where every block has to contain a hash value. Such blocks are linked by the previous hash and in case an attacker gets access to the transaction and tries to change the data, the hash will be altered thus affecting the entire chain. As a result, the sensitive data or information will be protected even more (Zyskind, Nathan & Pentland 2015).
Blockchain technology is one of the decentralized applications (Zheng et al. 2016). In most cases, it will support P2P communication hence in a blockchain network, the node is treated as computers. Such a large number of nodes (running into thousands) needs to contain the copy of distributed ledger which should be used to authenticate the transaction. Suppose any of the nodes is not in agreement with the transaction, the transaction will not proceed and would thus be cancelled. This would offer transaction protection against fraud because attackers will be automatically stopped.
3. Evaluation
The paper discusses security of blockchain technology. From the various papers reviewed, it has been established that there are some security problems still facing blockchain technology. Such security issues have an impact on the transaction. There are various types of attacks that can affect blockchain technology transactions but some solutions to these attacks are also available. There are also different classes of blockchain networks, including private blockchain, public blockchain, as well as consortium blockchain. The review paper has only given focus on the private as well as public blockchain. In general, blockchain is an enhanced trending technology with great potential to revolutionize and improve global transactions. Numerous applications of blockchain have been developed while others are still undergoing development based on this technology. Some of the solutions for the most recent issues touching on blockchain security have been provided and addressed.
4. Conclusion
Blockchain security is and has been an interesting topic in the past decade due to the increasing popularity of blockchain technology across the world. The technology is applicable in various industries and it has the capability of providing better security during transactions involving any value. As a bourgeoning technology, some of the reasons why blockchain is widely used is because of its integral data security as well as effective protection of private or sensitive data/information. The technology comprises of several layers that are designed to enhance safety and security of transactions and users. Nevertheless, it is important to note that as the application of blockchain technology increases rapidly, more new kinds of and advanced security threats are coming up targeting blockchain. Economic losses of billions of dollars have already been experienced in the blockchain industry but several security solutions have also been developed and some are still under development. There is need to conduct more studies and research aimed at developing strategies to strengthen the security protection of blockchain. So far, a significant number of studies about blockchain technology have already been carried out and their findings documented despite the less attention as well as researches regarding security of blockchain.
5. References
Aitzhan, N.Z. & Svetinovic, D. 2016, ‘Security and privacy in decentralized energy trading
through multi-signatures, blockchain and anonymous messaging streams’, IEEE Transactions on Dependable and Secure Computing, vol. 15, no. 3, pp. 840-852.
Bach, L.M., Mihaljevic, B. & Zagar, M. 2018, ‘Comparative analysis of blockchain consensus
algorithms’, 41st International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), IEEE, Opatija, Croatia, pp. 1545-1550.
Banerjee, M., Lee, J. & Choo, K.K.R. 2018, ‘A blockchain future for internet of things security:
A position paper’, Digital Communications and Networks, vol. 4, no. 3, pp. 149-160.
Dorri, A., Kanhere, S.S., Jurdak, R. & Gauravaram, P. 2017, ‘Blockchain for IoT security and
privacy: The case study of a smart home’, 2017 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), IEEE, Kona, HI, USA, pp. 618-623.
Eyal, I., Gencer, A.E., Sirer, E.G. & van Renesse, R. 2016, ‘Bitcoin-NG: A scalable blockchain
protocol’, 13th USENIX Symposium on Networked Systems Design and Implementation (NSDI 16), USENIX, Santa Clara, CA, USA, pp. 45-59.
Heilman, E., Baldimtsi, F. & Goldberg, S. 2016, ‘Blindly signed contracts: Anonymous on-
blockchain and off-blockchain bitcoin transactions’, International Conference on Financial Cryptography and Data Security, Springer, Heidelberg, Germany, pp. 43-60.
Kakavand, H., Kost De Sevres, N. & Chilton, B. 2017, ‘The blockchain revolution: An analysis
of regulation and technology related to distributed ledger technologies’, SSRN Electronic Journal, vol. 1, no. 1, pp. 1-27.
Karame, G. 2016, ‘On the security and scalability of bitcoin’s blockchain’, 2016 ACM SIGSAC
Conference on Computer and Communications Security, Association for Computing Machinery (ACM), New York, NY, pp. 1861-1862.
Khan, M.A. & Salah, K. 2018, ‘IoT security: Review, blockchain solutions, and open
challenges’, Future Generation Computer Systems, vol. 82, pp. 395-411.
Li, Z., Kang, J., Yu, R., Ye, D., Deng, Q. & Zhang, Y. 2017, ‘Consortium blockchain for secure
energy trading in industrial internet of things’, IEEE Transactions on Industrial Informatics, vol. 14, no. 8, pp. 3690-3700.
Lin, I.C. & Liao, T.C. 2017, ‘A survey of blockchain security issues and challenges’,
International Journal of Network Security, vol. 19, no. 5, pp. 653-659.
Pass, R., Seeman, L. & Shelat, A. 2017, ‘Analysis of the blockchain protocol in asynchronous
networks’, Annual International Conference on the Theory and Applications of Cryptographic Techniques, Springer, Cham, pp. 643-673.
Tosh, D.K., Shetty, S., Liang, X., Kamhoua, C.A., Kwiat, K.A. & Njilla, L. 2017, ‘Security
implications of blockchain cloud with analysis of block withholding attack’, 17th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing, IEEE, Madrid, Spain, pp. 458-467.
Wang, H., Wang, Y., Cao, Z., Li, Z. & Xiong, G. 2019, ‘An overview of blockchain security’,
China Cyber Security Annual Conference, Springer, Singapore, pp. 55-72.
Zheng, Z., Xie, S., Dai, H.N., Chen, X. & Wang, H. 2018, ‘Blockchain challenges and
opportunities: A survey’, International Journal of Web and Grid Services, vol. 14, no. 4, pp. 352-375.
Zyskind, G., Nathan, O. & Pentland, S. 2015, ‘Decentralizing privacy: Using blockchain to
protect personal data’, 2015 IEEE Security and Privacy Workshops, IEEE, San Jose, CA, USA, pp. 180-184.