1. Introduction
This report below sees us deliberate ANUC cybersecurity deficiencies, following the particular 2018 data breach at ANU. Through executing a comprehensive vulnerability analysis and a robust mitigation framework, that is designed to enhance the security posture and abhor any potential risks, would shield the organization, ANUC, from threats to its sensitive data. The report functions as the case overview, underscoring the major security risks in the digital world of today with a perspective of proactive cybersecurity measures being the way forward (Nouveau, 2022).
Initially, the ANU example gives a clear picture of the urgency and importance of cybersecurity in the ANUD concept, in which cybersecurity is one of the key elements that needs to be addressed. With the expanding corporate digitalization trend and data storage, the cyber threat risks is also raising. Thus, being proactive and increasing its security infrastructure learning options while taking preventive measures becomes essential for ANUC.ANUC analysis of the report enables a comprehensive evaluation of the cybersecurity positioning, detecting loopholes, and making mutually exclusive practices to solve them. One can find the lessons learned from the ANU breach containing the areas which need improvement, asked the organization to undertake the effective security measures in order to avoid similar events in future.
In essence, this paper presents a partial structure for ANUC cybersecurity evaluation and details the necessary strategic measures to enact resilience and preserve information assets. Appropriate proactive measures and the constant vigilance will serve for creating strong defenses of cybersecurity and ultimately guarantee the security of information ANUC handles (Schram, 2023).
2. Main Discussion
2.1. Risk Matrix and its application
ANUC uses the risk matrix method to estimate the complexity measured together with the potential negative impacts of the threats. With such risk-based approach, threat is recognized, and proper risk mitigation steps applied. Since risk matrix assays the probability and effects of both threats, ANUC can employ it as a logical method of cybersecurity risk management process. This part describes the application of such a technique by ANUC in order to render its cyber security strategy more effective.
2.1.1 Data Collection Process
Stakeholder interviews, historical data review, and literature review of cybersecurity form the data collection methodology of the ANUC group using the knowledge. Via engagement with involved parties and the review of previous cases, ANUC gain knowledge on how such incidents occurred and what potential risks might exist. Nonetheless, a comprehensive analysis of cybersecurity literature often puts me at an advantage of being up to date with the latest trends and industry standards. The multi variety nature of this information gathering method guarantees that the probability of each threat identified is clearly understood by ANUC, in reference to which they can make informed decisions for these cyber threat risks (Bojilov, 2023).
2.1.2 Classification of Threats
On completion of the process of the data collection, the ANUC uses the data to grade the threats depending on how serious they are. The categorization helps the organization to undertake mitigation strategies in ways that resources are allocated in line with the magnitude of risk posed by a hazard producing such threats. ANUC agency can have a picture of both likelihood and damage range, which make it possible to design the cybersecurity scenario comprehensively and respond the situation respectively (Fisher, Porod, & Peterson, 2021).
This instrument will allow ANUC to distinguish these priorities and enable it to allocate resources commensurate with the thereat they pose. By giving more effort to mitigation measures that reduce the severity of these high-margin risks, ANUC can implement a proactive cybersecurity strategy and create a stronger enterprise in terms of cyber resiliency. This purposeful strategy guarantees that the ANUC’s cyber-attacks prevention measures are used in the places that are the most vulnerable to security breaches and compromise of sensitive data as far as the operations are concerned.
2.1.3 Prioritization Strategy
ANUC deploys a prioritization tactic in which high risk processes like data leaks and others will face its cybersecurity efforts. By focusing the resources and the attention principally to the most significant threats ANUC is striving for a posture and resilience which will be less vulnerable to cyber-attacks. It should be noted that risk-based triaging is a strategy that allows ANUC to effectively allocate its limited resources, which in turn permits it to aim its mitigation efforts at the most critical spots (Vegesna, 2023).
This prudent step would allow ANUC to identify optimal places for improvement and accordingly put in high priority actions that will exceedingly contribute to reducing risk of cyber-attacks. By devoting greater resources to the most formidable challenges above ANUC can significantly boost its proficiency while dealing with attacks, preventing them, and repelling them. Furthermore, adopting this is the most effective strategy because it supports efficient resource utilization, ensuring that cybersecurity efforts are in line with organization’s risk management goals (Gourisetti, Mylrea, & Patangia, 2020).
2.1.4 Structured Decision Making
Using the risk matrix technique, it becomes possible for ANUC to have a tool that employs a structured methodology for cybersecurity management. This way of thinking helps to develop sound strategy selecting the threats on priority list and on which threats to direct the resources for mitigation procedures. Through applying system risk assessment that help in measuring the probability of intrusion and consequences, ANUC can improve its cybersecurity risk management policies. The structured approach of ANUC in this way raises the barrier even higher to the real threats since it evaluates the reported risks and prioritizes mitigation accordingly — which is based on the severity (Araujo & Taylor, 2020).
2.1.5 Strategic Orientation
The risk matrix framework with which ANUC analyzes the cyber threat landscape orient it towards future readiness. The risk matrix hinges on two factors risk and likelihood. Therefore, the risk matrix methodology is foundational to ANUC’s cybersecurity program By carefully assessing penetration of threat, and assessment of risk, and thinks wisely how to lower cybersecurity risks, ANUC turn to be more resilient to cybersecurity risks. Cybersecurity poses a multidimensional risk for organizations especially with the increasing cyber-attacks. Thus, for the ANUC to be up-to-date in addressing the various cyber threats, it needs to strategically allocate the resources with a focus on addressing the most critical threats. These strategic tenets also ensure the ANUC is proactive in its cybersecurity activities maintaining perpetual responsiveness to emerging cyber threats and keeping robust defenses in place to protect its operations and data (Bokan & Santos, 2021).
| Threat | Likelihood | Consequence | Severity |
| Phishing Attack | Medium | High | High |
| Insider Threat | Low | High | Medium |
| Data Leak | High | High | High |
| DoS/DDoS Attacks | Medium | High | High |
| Failure of Policy or Management Commitment | Low | High | Medium |
2.2. Threats and Controls
Herein, we proceed to assemble the catalogue of cybersecurity threats, and then assign the corresponding controls with which to effectively implement the risk mitigation measures into the framework of ANUC’s cybersecurity system.
2.2.1 Matching Threats with Controls
At this point, ANUC does a thorough evaluation of each of the threats investigated in Assessment 2 to select the particular vulnerabilities that are within its infrastructure. Through this way, controls must be identified correctly and then placed in the areas where the gaps are. In this case, it is aspired to produce the particular method of remediation for each hazard in order to eliminate them successfully. Through performing an accurate risk assessment, ANUC can adjust for the corresponding risks, which further raise the organization’s ability of security against unwanted cyberattacks. This will be a vital element in not only disrupting the attacker’s efforts, but also ensuring the organization gets a robust cyber security posture.
2.2.2 Tailored Controls
The measures taken by the ANUC can either curb potential threats due to an open space or even eliminate the threats on the whole. These activities comprise an extensive array of undertakings such as the technical upgrading, the gear system renovation as well as administrative measures. With the deployment of all these controls, the situation regarding ANUC information security is strengthened while a comprehensive mechanism against critical cyber challenges has been further developed. These tools also stand among many aspects that enable cyber security professionals to monitor and defend against cybercrimes as well as reduce the damage that occurs due to cyber security breaches. Revolving around critical weaknesses, the attacks can pry open up any liability of the organization and cause a significant damage to data and operations (Safitra, Lubis, & Fakhrurroja, 2023).
2.2.3 Budgeting/projections -Forecasting and supervisory function
ANUC entails a cost estimation for all the preventive measures, including development of policies, implementations of training programs, and equipment suitable for tech solutions. This comprehensive budgetary playoff provides the requiring that the ANUC’s financial means are taken into account while at the same time ensuring the seriousness of cybersecurity problems. ANUC can ensure resource allocation related to the financial implications of control options, by documenting them, and as a result, it can make reasonable decisions regarding them. The methodology is aiming for the highest level of efficiency within the behavior of organizational budget frame work and proper cybersecurity resources are allocated in order to make mitigation of cybersecurity risks possible (Wong, Lee, Tan, Ooi, & Sohal, 2022).
| Threat | Control | Cost Estimate (USD) | Justification |
| Phishing Attack | User Awareness Training | $10,000 | Educating users to identify and report phishing attempts. |
| Insider Threat | Role-based Access Control | $15,000 | Restricting access based on job roles to minimize insider risks. |
| Data Leak | Encryption of Sensitive Data | $20,000 | Protecting sensitive data at rest and in transit to prevent unauthorized access. |
| DoS/DDoS Attacks | Network Intrusion Prevention System | $25,000 | Detecting and mitigating DoS/DDoS attacks to ensure network availability. |
| Failure of Policy or Management Commitment | Cybersecurity Policy Development | $12,000 | Establishing clear policies and management commitment to cybersecurity best practices. |
2.2.4 Justification for Controls
Every aspect is documented with thorough reasoning showcasing its viability and effectiveness in already existing alternative to reduce the threat. Firstly, ANUC argues that particular controls should be put in place by presenting them with a basis. This is meant to smooth the way for the deployment of cybersecurity measures, their endorsement and the achievement of consensus.
However, this methodology outcomes from the identification of cyber threats, which are aimed at immediate targeting with the costs and justification of the security measures developed would be a comprehensive approach to secure ANUC. Such alignment is necessary that ANUC’s cybersecurity structure remains strong and vigorous when facing soaring and developing cyber dangers.
2.3. Mitigation Scheme: Incorporating future proof ANUC’s cybersecurity measures
The proposed mitigation scheme that is outlined in this section, serves as a strategic roadmap for leveraging identified controls into ANUC’s cybersecurity parameters. Through a comprehensive, detailed project plan, comprising of the dates, assignments and the expenses given on ANUC, the organization hopes to enhance the security of its system and reduce cybersecurity risks in general.
2.3.1 Integration of Controls
ANUC will implement canned along with both software and hardware tools that will be accompanied by administrative, technical and procedural controls. This will lead to a comprehensive effort of addressing vulnerabilities. These in-depth measures, which methods are very precise to address differently instructions in cyber security such as network security, data protection and access management , are employed very wisely.
2.3.2 Structured Project Plan
A process project plan will be designed to make sure the l plan runs smoothly and gives a room for further improvements. This project entails in details the assignments, deadlines and responsible persons who will be answerable for the projects progress.
2.3.3 Timelines and Milestones
Schedules for the enactment of each component control are set, facilitating timely project management, as well as resource planning and distribution. The milestones answer the question of where the project is currently located and how far it has come from the start. They help the stakeholders track the project and see its enterprising course.
2.3.1 Integration of Controls
ANUC will rely on a comprehensive cybersecurity strategy that will merge the existing policy frameworks, and will include purchase of canned solutions, use of software and hardware tools (you might mention the specific types), and administrative, technical and procedural methods. This all-encompassing strategy reflects in identification of gaps whereby a holistic solution is applied to several fronts including networking, data security, as well as access management. Every control method is profoundly selected, in concert with distinct cybersecurity instructions, to ensure the proper and efficacious counter-operation (Kaur, Gabrijelčič, & Klobučar, 2023).
Utilizing the advanced support of different security mechanisms, ANUC aims at having defense layers that cumulatively contribute to the best possible cybersecurity situation. This almost eliminates the most effective ways one can defend themselves from their critical infrastructure and since evolving threat is continuous, we can only be able to anticipate the threats and not deal with them, we can enhance their awareness of these threats (Wong, Lee, Tan, Ooi, & Sohal, 2022).
2.3.2 Structured Project Plan
ANUC shall plan a sturdy plan that comprises maintenance of the smooth performance of the cybersecurity tasks. This plan will spell out the functional description of man-years detailing deadlines and responsibilities which have been assigned. Of the utmost importance is the provision of a structured project plan with a detailed tasks list and progress tracking, which helps to ensure that required activities are being implemented in right proportion and delivery is transparent at all times.
Additionally, the project plan will create an environment for flexibility and adaptation. Thanks to that, ANUC will be able to react to feedback, maybe on the necessities of some changing, while embarking on cybersecurity initiatives. The continuous activity approach allows the company to maintain a position where it is able to address quickly emerging risks and diverse cybersecurity concerns.
2.3.3 Timelines and Milestones
To this end, ANUC planning will encompass deadlines for the application of each prescribed component that will ensure the overall timely, the efficient project management as well as the resource allocation. Furthermore, landmarks will be designated important the ultimate aim which will be to motivate successful completion. These milestones respectively comes in handy as a gatekeeper that monitors the progress of the project and also gives the stakeholders, a glance into, the project’s possible direction.
ANUC’s observance of set deadlines and milestones will help in recording advancement of its cybersecurity ideals and allows to make sure that they are on time. Such a proactive approach allows us to better judge if the organization is going according to its cybersecurity goals as well as successfully handle and eliminate risks (Argaw et al., 2020).
2.3.4 Cost Management
ANUC is financial oriented operationally to cybersecurity controls, decision making processes involve, including acquisition of costly same the technical upgrades, initiating training programs, and enacting policy amendments, are carefully budgeted for. ANUC can protect itself from financial threats as well as strengthen cybersecurity initiatives by including the funding timeline in the organization’s priorities. With this precautionary strategy, however, financial capabilities are managed in a way that ensures that they are deployed wisely and productively for the purposes of decreasing the risks of cybersecurity.
2.3.5 Displaying productivity with the help of Gantt chart
The use of a Gantt chart makes it possible to show the outlined timeline for adding these controls graphically, and workers can follow the markers of advancement and milestones with ease. Through creating a visual representation of the project plan, you assure the avoidance of inevitable communications obstacles, and you allow the stakeholders to have complete grasp of the project’s progress. This form of image improves the communication and collaboration among the team members and hence the informed decisions are made based on comprehensive fundamental knowledge about the project development. Further to that, Gantt chart also acts as a times management tool to monitor deadlines as well as deliver cybersecurity initiatives within scheduled time frames. In summary, the Gantt chart, with the help of its graphically, makes project’s progress visible and gives the management an advantage to have effective project control (Trim & Lee, 2021).
| Task | Start Date | End Date | Number of Days | Responsible Personnel | Cost (USD) |
| User Awareness Training | 2024-05-01 | 2024-05-15 | 14 | IT Security Team | $10,000 |
| Role-based Access Control | 2024-05-15 | 2024-06-01 | 17 | IT Department | $15,000 |
| Encryption of Sensitive Data | 2024-06-01 | 2024-06-30 | 29 | Data Security Team | $20,000 |
| Network Intrusion Prevention | 2024-07-01 | 2024-08-01 | 31 | Network Security Team | $25,000 |
| Cybersecurity Policy Development | 2024-08-01 | 2024-08-15 | 14 | Management Team | $12,000 |
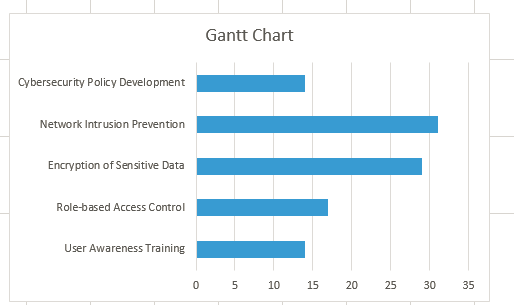
Indeed, this emphasizes the ANUC’s dedication to build its cyber resilience level through the reactive and, overall, strategic approach. The ANUC administrators intend to consolidate the controls into a formalized project framework to stand guard against cyberattacks while strengthening the organizations defensive position and securing its virtual assets via visualization tools like Gantt chart.
3. Conclusion
Finally, the report my point out that an unambiguous cybersecurity approach is of vital importance to ANUC. Based on ANU’s data breach exemplification and doing extensive risk analysis, ANUT would be capable to properly detect vulnerabilities and to implement specific measures to limit the risks that were identified. The specified security plan that is discussed in the current report is aimed at serving as a primary area in which ANUC will improve its security posture. ANUC can have a strong cyber defense by creating a control system with technical, operant, and administrative controls as part of the control system (Trim & Lee, 2021).
Also, the stress on non-stop monitoring and the ability to adapt accordingly to evolving threats give rise to a cyber-security technology that is robust and resilient potentially to the emerging security challenges in the cyber-space. Thru placing cybersecurity activities before other initiatives, and relation to all the key-stakeholders, ANUC can proactively mitigate risks and prevent the exchange of sensitive data.
Finally, the mitigation scheme may be considered as a standard of security within the system of ANUC which in the end would serve to build the trust of stakeholders. When, by showing a firm in security of its data and system health, ANUC proves itself to the academic society as a credible organization, then its reputation indeed deserves it.
Timely and active cybersecurity procedures is an important thing for ANUC to go through the complication of digital universe and to keep its interests safe in the emerging interconnected world. By having a proactive approach against cyber security, ANUC can protect its assets from untoward incidents and long term he engagement (Pollini et al., 2022).
4. References
Araujo, F., & Taylor, T. (2020, November). Improving cybersecurity hygiene through JIT patching. In Proceedings of the 28th ACM Joint Meeting on European Software Engineering Conference and Symposium on the Foundations of Software Engineering (pp. 1421-1432).
Argaw, S. T., Troncoso-Pastoriza, J. R., Lacey, D., Florin, M. V., Calcavecchia, F., Anderson, D., … & Flahault, A. (2020). Cybersecurity of Hospitals: discussing the challenges and working towards mitigating the risks. BMC medical informatics and decision making, 20, 1-10.
Bojilov, M. (2023). Methods for assisting in detection of synthetic identity fraud in credit applications in financial institutions (Doctoral dissertation, CQUniversity).
Bokan, B., & Santos, J. (2021, April). Managing cybersecurity risk using threat based methodology for evaluation of cybersecurity architectures. In 2021 Systems and Information Engineering Design Symposium (SIEDS) (pp. 1-6). IEEE.
Fisher, R., Porod, C., & Peterson, S. (2021). Motivating employees and organizations to adopt a cybersecurity-focused culture. Journal of Organizational Psychology, 21(1), 114-131.
Gourisetti, S. N. G., Mylrea, M., & Patangia, H. (2020). Cybersecurity vulnerability mitigation framework through empirical paradigm: Enhanced prioritized gap analysis. Future Generation Computer Systems, 105, 410-431.
Kaur, R., Gabrijelčič, D., & Klobučar, T. (2023). Artificial intelligence for cybersecurity: Literature review and future research directions. Information Fusion, 101804.
Nouveau, P. (2022). Falling behind and in between the United States and China: can the European Union drive its digital transformation away from industrial path dependency?. In EU Industrial Policy in the Multipolar Economy (pp. 332-381). Edward Elgar Publishing.
Pollini, A., Callari, T. C., Tedeschi, A., Ruscio, D., Save, L., Chiarugi, F., & Guerri, D. (2022). Leveraging human factors in cybersecurity: an integrated methodological approach. Cognition, Technology & Work, 24(2), 371-390.
Safitra, M. F., Lubis, M., & Fakhrurroja, H. (2023). Counterattacking cyber threats: A framework for the future of cybersecurity. Sustainability, 15(18), 13369.
Schram, B. (2023). Surveilling Queerness and Queering Surveillance: The Techno-Social Making of Queer Identity in the US and Canada, 1939-Present.
Shah, V. (2021). Machine Learning Algorithms for Cybersecurity: Detecting and Preventing Threats. Revista Espanola de Documentacion Cientifica, 15(4), 42-66.
Trim, P. R., & Lee, Y. I. (2021). The global cyber security model: counteracting cyber attacks through a resilient partnership arrangement. Big Data and Cognitive Computing, 5(3), 32.
Vegesna, V. V. (2023). Enhancing cyber resilience by integrating AI-Driven threat detection and mitigation strategies. Transactions on Latest Trends in Artificial Intelligence, 4(4).
Wong, L. W., Lee, V. H., Tan, G. W. H., Ooi, K. B., & Sohal, A. (2022). The role of cybersecurity and policy awareness in shifting employee compliance attitudes: Building supply chain capabilities. International Journal of Information Management, 66, 102520.