Introduction:
For every company’s success stands on the ethical behavior of the company towards their customers. Harry Markham a pension investment advisor. Once in early 2012, he was in a dilemma about the state of pension fund while he was involved into preparation for the meeting along the board of trustees. Harry Markham completed his master of finance in the year 2004 from the B- school of USA, and he was found to be working for investment consulting associates (ICA) which had been involved into giving advice for funds related to pension. Markham could closely remain connected with the way the liabilities of pension funds were valued since Markham’s joining in the company. If Markham follows the principles which are guided in the MOF and CFA programmer, he got those numeric which were twice increased value compared to those reported for the funds. But he was not given permission to make any adjustment to the official numbers, inspire of the client members and the firm itself being least bothered in questioning them to make the board of trustees, the firm was unable to make any objection for the board who did not want the complain that the liabilities of the funds were much greater than number considered as per the government accounting standard rules (GASR) rules. Markham’s concern was with the loyalties with the firm, with the board of trustee, investors, investment expertise etc. Markham was in a dilemma whether or not to raise the issue of liability in the conference room to the board of the state pension fund. He knew that there was risk in the either side. But as he was bound with the ethical code of conduct, he was finding it difficult to hide the whole thing (Swanson & Frederick, 2016).
Discussion:
Harry Markham often said that ‘My role isn’t for deciding the liability value. As an investment advisor his role is to offer different ethical views. He was challenged both by ethically and practically. The central problem is an ethical issue for Harry Markham’s, CFA. His loyalty related to his firm, the board of trustees as well as the pension holders is at odds with his personal and professional standards.
As an investment advisor Markham need to identify the circumstances of the investors, like their background, their ability to take risk, the annual income, the budget for investment etc. to make the best investment advice. The CFA professionals said that one should not give advice without identifying the client’s circumstances. And the next is they got those funds which are grossly being shortage of money, but the accounting could not consider them to be as shortage of money. Before giving advice Markham let the firms know where they are starting. Therefore, the client will be knowing that got to start from a multi- billion dollar. On the other hand Markham was concerned about not getting what he could believe were in accurate figures, he also know that his clients are afraid of getting bad news. He was bothered about the fact that if he was to reflect issue related to liability then surely he and his business company would be fired.
Investment committees and staffs believe that their main motto is to earn, at least at the discounted rate given by the government. A sponsor told Markham that it could not be as per planning members’ interest to decrease the rate of discount as the liability increase would bring about shock to the taxpayers as well as to the state legislature that it would determine the support related to political for the plan’. The sponsors of the plan are least interested to know that they were low funded compared to the numbers those are showing and the messengers are blamed. On the other hand if it was officially elected they don’t desire a crisis as per their knowledge (Swanson & Frederick, 2016).
An advisor for investment is responsible to make good investment decisions, and have a knowledge in client’s financial condition to make sound investment decision. This sometimes involve those information which the clients are afraid of.
Generally, as a Chartered Financial Analyst, Markham need to attest the compliance with respect to the ethical code of conduct. He need to air those information which is ethical to do and are relevant to the firm and the client too. As an employee of the company, Markham need to be loyal, need to know all the code of conducts, need to be ethical.
Ethics mostly concern on that is right as well as that is wrong in behavior related to business judged as per the basis of the future standard of practice as per approval of the society. Business ethics is a code of conduct consisting of regulation of the business activities towards society as well as other business units. As well as business ethics defines the social, legal, cultural and economic limits within which business organization are expected to plan their activities. According to Markham’s dilemma relating to conflicting loyalties of a firm explained as the loyalty of boards of trustees including such peoples engaged in making investments decisions relating to public pension. Such person are hired by the firm as an investment expertise the code of ethics needs to maintain by such individual persons to conduct their performances effectively. The board of trustees will remain unaware for its dangers and will be happy related to the pension plan of state and will still have its own support with respect to political. His self as well as professional views related to ethics are violated. Moreover, the liabilities will deal as per the plan and the employees will not get benefits or taxpayers will require to pay more (Swanson & Frederick, 2016).
Conclusion:
It can be concluded from the above discussion that the ethical issue arises from Harry Markham is related to loyalty of firm, board of trustees as well as pensioners with personal standards. It can also be concluded that funds are shortage of money but accounting does fail to show them shortage of money. Further discussion reveals about responsibility of investment advisor to take good investment decisions. It can also be concluded that business ethics is a social, legal as well as cultural limits for which organization plan their activities accordingly. Hence, it can be concluded that as per Markham people engaged in making investments should be hired by firm as investment expertise being code of performance efficiently.
References:
Swanson, D. L., & Frederick, W. C. (2016). Denial and leadership in business ethics education. Business ethics: New challenges for business schools and corporate leaders, 222-240.
Inferential Statistics Analysis and Writeup
Introduction:
I am a 35-year-old married individual living in Austin, Texas. I have a Bachelor’s Degree in Nursing and work as a surgical nurse. My husband and I own a house and we have one child. We are planning to have another child and we want to know what changes to expect in terms of expenses with an addition to our family.
Variables Selected:
Table 1: Variables Selected for Analysis
| Variable Name in the Data Set | Variable Type | Description | Qualitative or Quantitative |
| SE-Marital Status | Socioeconomic | Annual household income | Qualitative |
| USD-Annual Expenditures | Expenditure | The total amount of annual expenditures within a household | Quantitative |
| USD-Housing | Expenditure | The total amount of expenditure on Housing | Quantitative |
Data Analysis:
1. Confidence Interval Analysis: For one expenditure variable, select and run the appropriate method for estimating a parameter, based on a statistic (i.e., confidence interval method) and complete the following table (Note: Format follows Kozak outline):
Table 2: Confidence Interval Information and Results
| Name of Variable: USD-Annual Expenditures |
| State the Random Variable and Parameter in Words: The amount (in US dollars) spend annually within a household. An arithmetic mean will be used to summarize the annual expenditure in US dollars. |
| Confidence interval method including confidence level and rationale for using it: The confidence interval is calculated for the mean with 95% confidence interval. The annual expenditure variable is continuous and the estimate parameter is mean. |
| State and check the assumptions for confidence interval:Confidence intervals construction assume that the random variable meets central limit theorem conditions. The assumptions are – randomization and independence of the observations. The observations are assumed to be randomly selected from the population and were randomly selected from the population. |
| Method Used to Analyze Data:The data is analyzed using data analysis tool in MS Excel to calculated the mean and 95% confidence interval. |
| Find the sample statistic and the confidence interval:The average annual expenditure is 66,165.53 USD with a 95% confidence interval of 4,068.92 USD (62,096.62 – 70,234.45 USD) |
| Statistical Interpretation: The average amount of annual expenditure for a household in USD will be between 62,096.62 – 70,234.45 USD at 95% confidence level, assuming that the observation is selected from the same population. |
2. Hypothesis Testing: Using the second expenditure variable (with socioeconomic variable as the grouping variable for making two groups), select and run the appropriate method for making decisions about two parameters relative to observed statistics (i.e., two sample hypothesis testing method) and complete the following table (Note: Format follows Kozak outline):
Table 3: Two Sample Hypothesis Test Analysis
| Research Question:Is there a statistically significant difference in the total amount of expenditure on housing between married and not-married individuals. |
| Two Sample Hypothesis Test that Will Be Used and Rationale for Using It: Two sample independent t-test assuming unequal variances will be used because the sample sizes are less than 30 for both groups – married and not-married. The unequal variances are assumed because the variance statistics are different. |
| State the Random Variable and Parameters in Words:For the independent sample t-test, two variables are used – amount of expenditure on housing and the marital status. The average amount spend on housing in USD is compared between the married and not-married respondents. |
| State Null and Alternative Hypotheses and Level of Significance:Null hypothesis: There is no significant difference in average amount spend in housing in USD between married and not-married respondent. Alternative hypothesis: There is a significant difference in average amount spend in housing in USD between married and not-married respondent.Level of significance: A 5% level of significance is used for the independent samples t-test. |
| Method Used to Analyze Data:Data analysis tool in MS excel is used to conduct the independent t-test. The data is spread to create two variables of the amount of expenditure on housing for married and not married. |
| Find the sample statistic, test statistic, and p-value:The average amount spent in housing for the married individuals is approximately 76,421 USD compared with 55,910.07 USD for those who are not married. The calculated t-statistic is 17.51 with a p-value equal to 6.47×10-11. |
| Conclusion Regarding Whether or Not to Reject the Null Hypothesis:According to the t-statistic and the p-value, the null hypothesis is rejected, hence concluding that there is a significance difference in the amount of expenditure on housing between married and not-married respondents. |
Part B: Results Write Up
Introduction
In the second assignment, the scenario assumed a 35-year-old married individual living in Austin – with a bachelor’s degree in Nursing and working as a surgical nurse. Her and her husband own a house and they have one child. The woman wanted to have a glimpse of the expected changes in expenditure, given that their family will increase, based on their anticipated child.
Table 1 for assignment 2: Variables selected for the assignment
| Variable Name in the Data Set | Description(See the data dictionary for describing the variables.) | Type of Variable (Qualitative or Quantitative) |
| Income | Annual household income in USD. | Quantitative |
| Marital Status | Marital Status of Head of the Household | Qualitative |
| Family Size | Total Number of People in the Family (both Adults and Children) | Quantitative |
| Annual Expenditures | Total Amount of Annual Expenditures | Quantitative |
| Housing | Total Amount of Annual Expenditures on Housing | Quantitative |
Data description and Method Used for Analysis
Data used in assignment 2 included income, marital status, family size, annual expenditures and Housing. MS excel was used for the numerical and graphical analysis.
Confidence Interval Analysis:
The 95% confidence interval for the annual household expenditure was calculated to provide a statistical evidence for the range of possible annual expenditure. Since the variance is an integral of the confidence intervals, calculating the CI provides a statistical evidence of the expected average of annual expenditure. The confidence interval means that the average household expenditure is between 62,096.62 USD and 70,234.45 USD with 95% confidence. Therefore, a household selected at random from US is expected to have an annual expenditure between 62,096.62 USD and 70,234.45 USD with a chance of 95 in a hundred.
Two Sample Hypothesis Test Analysis:
Marital status can possibly influence expenditure because the family size increases, hence, personal needs. In specific to housing expenditure, married people require more house space compared to single individuals because their families are anticipated to increase after getting children. The Two sample hypothesis t-test aimed at understanding whether there was a statistical difference in the amount spend in housing between married and not-married respondents. The hypothesis assessed for this two-sample test was a shown below.
Null hypothesis: There is no significant difference in average amount spend in housing in USD between married and not-married respondent.
Alternative hypothesis: There is a significant difference in average amount spend in housing in USD between married and not-married respondent.
The two-sample independent t-test assumes that the two variables are independent, respondents are randomly selected and the observations are normally distributed and the sample is of small size – which were met. In conclusion, the amount spend in housing was found to be statistically different between married and not-married respondents at 95% confidence level; hence, rejecting the null hypothesis because the p-value was less than the significance level. At 95% confidence level, household for married individuals spends statistically significantly higher amounts in housing compared to household for not-married individuals. Therefore, there is a 5% chance of failing to reject the null hypothesis while it is not true (type II error).
Discussion:
A household in the US spends approximately 66,165.53 USD annually with a 95% confidence interval of 4,068.92 USD (62,096.62 – 70,234.45 USD). Individual who are married spend more for their housing compared to their unmarried counterparts. Therefore, individuals who are married in the US should expect to spend more for their housing compared to those who are not married. The person described in the scenario should prepare for an average of 66,165.53 USD annually for household expenditure and she is lucky because they own a house – they would have spent an average of 76,421 USD for their housing per year.
Smartphone NFC Technology Security and Issues
ABSTRACT
The technology of internet adoption of things and its applications is changing every day. Near Field Communication for instance is internet of things technology that is vastly adopted because of its range frequencies since they are short hence making it good candidate to be applied in systems such as door and attendance system based to its access control. However, as a result of miniature size of Near Field Communication tags; since the text contents is much clear and insecure channel communication between tag reader database; the middle man that is Denial of Services among others are prone to security attacks in Near Field Communications technology. Any organization adopting the applications and technologies of NFC are impacted by the critical data that are leak by the users in these attacks. In this article, Near Field Communication vulnerability that are caused by privacy and security attacks are deeply studied. By focusing on data corruptions and Denial of Service (DOS) instance of attacks, the approach of Analytical Hierarchy (AHP) is used to evaluate the risk assessment that are existing. Also the best practice is presented that are used in mitigating these attacks
INTRODUCTION
The Near Field Communication is the technology of wireless communication that is simply an extension from RFID technology operating in short range communication. The RFID mainly is used in transmitting, identifying and tracking of the radio waves [8]. Near Field Communication can operates on a frequency that has a range is low as 13.56 MHz covering a that is between 4cm to 10 cm with a maximum data rate of about 424 kbps. Near Field Communication applications can be groups such as touch and explore, touch and connect, touch and confirm, and touch and go. The application of NFC in real life usage doesn’t really ensures application security. Therefore, the technology of NFC has its challenges to face for instances, the security treats of RFID can be applicable to Near Field Communications, since NFC is a colleague of RFID and all Near Field Communication devices act as writers or readers that can create threats that different [7].
Due to lack of a Near Field Communication that covers all the countermeasures of x.800 security services for example access control and authentication is another leading factor security vulnerability in Near Field Communication. The current specification guideline of NFC developers. The current specification that are provided are guideline for Near Field Communications developers for applications that secure data as well as communications within Near Field Communication devices. The next of privacy issues arises while using Near Field Communication likes users’ personal information stored in the devices of NFC then could be disclosed to malicious attacks [12]. For example, user using Near Field communication like a digital wallet for storing there information about their bank account then are prone to attack of data privacy while information in that wallet can be captured at anywhere and anytime by attackers without any user concept since Near Field Communication technology faces security challenges as concern in rising of an environment that is secure. There are a number of Near Field Communication applications that are developed with payment application that is contactless and works in two ways that is touch and go, and touch and confirm application. Google Wallet as well as Pairwave are examples of payment application that are contactless [12].
The Google Wallet is a touch and confirm application of NFC that need a PIN code confirmation to undertake any transaction. On the other hand, Visa paywave is a touch and go application type of NFC that allows the visa card holders to just wave their card or Near Field Communication allows smartphone with contactless payment terminal to process payment with no confirmation of that payment. The vulnerability have been identified on previous research that of contactless payment, in Visa card that is contactless, the card doesn’t recognize foreign currency that are from outside United Kingdom thus lead to fraudster in transaction of the contactless. Hence, security becomes a concern in payment that are contactless in particular touch and go application of NFC since they perform payment with no confirmation while process the transaction.
Research Questions
- Is there security concerns with the NFC technology of payment?
- If so, what are measures which can be put in place to overcome the security issues?
- Who is to be answerable to the attacks associated with electronic payment?
- Reason why the electronic payment is not majorly used around the world.
- Why is it that money is getting lost from peoples NFC accounts?
Literature review
The scholarly writing survey in any zone of research is fundamental work since it gives inquire about structures, commitments, scientific categorization, and open research zones meaning, and headings of future research. Such work of NFC inquire about territory was not performed so far in a thorough and control way. So as to have writing survey of NFC look into, related essential audits contemplates – electronic trade, data frameworks, RFID and versatile business must be inspected in detail. In understanding to Borchert and Günther [1] proposed the distinction of plan science inquire about and that of conduct science. Plan science is basically a procedure of tackling an issue that makes just as assesses Information Technology, expected in taking care of featured authoritative issues. They generally centers in the significance of science configuration in research territories of data frameworks just as makes look into system that keeps up the thorough and the pertinence of the examination. All together for the scientists accomplish a viable science configuration inquire about in the data frameworks, seven basic rules are given.
These days, accomplishing a viable and complete NFC science plan is a vital issue just as essential. Today a large portion of this NFC scholarly writing in some cases can be considered as a science plan rather than a social science. Another related just as an exploration region more extensive is online business (electronic trade) because of its oddity just as development increment. One can find a few audit investigations of electronic trade in points of view that are not the same as various occasions Kim [5]. These days, we see that electronic business has one of the extraordinary secured territory as a result of developing enthusiasm for it.
In understanding to Francis, Hancke, Mayes and Markantonakis [2] just as Geon Pak, Ram Lee and Suk Lee [7] who are some the online business writing audits analysts, they by and large express electronic trade look into scientific classification in various four measurements that is innovation, applications, support just as execution, and different issues, investigations similar has an extraordinary effect to the assurance of the issues just as research zones for future. The for the most part impressive recommendation have been made on the advancement of “thorough research strategies for articles and further observational examinations” That are additionally a rule for science configuration looks into [3]. Subsequently, thorough of Near Field Communication writing as a recently developing innovation just as are of research that needs to inspected. A similar case to M-business that is versatile trade, there writing surveys are great sources that can be utilized while making an appropriate Near Field Communication scientific classification.
The distinguishing proof of the holes among the hypothesis, practice just as heading of things to come examine for portable trade papers are plainly all around organized with grouping system just as examinations is according to [4].
In actuality, RFID explore zone’s additional examination which was likewise proposed in there carefully. At the point when the examination regions are limited Near Field Communication writing, Radio Frequency Identification look into territory has related innovation to that of NFC, which is a piece of electronic trade just as portable business world.
ANALYSIS
Risk Assessment & Multi-Criteria Decision Techniques
The multi – Criteria Decision Techniques as well as risk assessment are discussed under this section. The comparison of multi-criteria decision making to that of risk assessment are thoroughly done.
Risk Assessment Methods
The technological scientific process base that is consisting steps of risk analysis, identification of the risk as well as risk evaluation is refers to as Risk assessment.
Accordingly, CVSS stand as the best option for risk assessment due to the fact of its capability which is focused in calculating various different types of scores such as temporal, base and environment.
This is applicable to be adopted as a risk assessment for a technology based applications such as NFC. Meanwhile, OCTAVE only focuses on organizational risk as it is designed for organizations instead of technological risk and, it is hard to implement because there are many practices that need to implement. Although, CVSS does not reduce the number of attack, it evaluates the attacks with rating score [13].
Multi Criteria Decision Making (MCDM) Methods
This is a decision making algorithm which is utilized in making best decisions in the alternative decisions. Its main aim is to determine and rate the alternative decisions in terms of there priorities. This technique has been used for many assessments. From the study, MACBETH and the AHP are used in supporting the pairwise comparisons. TOPSIS is utilized when the ideal as well as the anti ideal options are needed. ELECTRE and VIKOR, all the two are based on the same principles on the concordance analysis like considering some global measures as well as other criteria which are [13]. SMAA makes determination if the information of the decision is correct and accurate which in-turn helps in preventing making of wrong decisions because of inadequate information. The MCDM method gives a description that those AHP applications, have powerful and highly flexible guidance method to the techniques used for decision making.
Possibility and Impact Estimation of Vulnerabilities using CVSS
Calculation of possibility is done by the use of metrics group as well as temporal group metrics of the CVSS. Calculation of Impact estimation is done by use of base group metrics as well as environment group metrics of the CVSS [9]. There results are taken from the survey data which needs respondents for evaluation. The survey data is categorized into discrete probability distribution which is used in assigning the probabilities for every outcome of each and every rating group as low, medium as well as high for the CVSS. The scores in this case segregated into a probability distribution because the participants had different values for each and every CVSS metric. The calculation of probability is given by the formula below;
SMAA-TRI method is used in calculation and production of category indices which are acceptable for each and every pairs of the categories and alternatives. The JSMAA is used for simulation of the SMAA-TRI [9].
FINDINGS
Dos Attack & Data Corruption Attack Countermeasures & Selection Using Mcdm
The Dos attacks takes place when the NFC devices gets in touch of the empty or rather NFC tags which are corrupted, error messages will take the NFC devices until such a time when the devices are suspended. This also takes place in smartphone which NFC enabled. Corruption od data involves the processes whereby the attackers manipulate data as a results the NFC transmission is disturbed by the NFC interfaces and the devices. Now that data has been corrupted, it will be unreadable to the devices which are operating under the NFC [10]. In order to prevent corruption of data, then NFC devices have to observe and check the radio frequencies when data is being transmitted. Detection of this particular data corruption attacks can be done due to the fact that higher power is required in the corruption of data as compared to sending of data, therefore, NFC is in a position of detecting sending data session which utilizes more power during transmission of data. This measures which are to be used in minimizing the risks of corruption of data as well as the Dos attacks is done by signing tags which encryption techniques by the use of cryptographic tag authentication protocols as well as establishment of a secure channel which has to exist between the NFC devices. It is the best option to secure the NFC communication as well as defending all types of data attacks when communication or data transfer is taking place [10].
MCDM Analysis is AHP Approach
This AHP method of approach utilizes the selection of the NFC risk countermeasures which have the highest priority. This method is utilized in creation of the priorities the alternatives and its criteria is utilized in decision making as well as judgmental for the alternative decisions made. The AHP method comprise of the following steps [11];
- Step 1
Development of criteria weights for the creation of single pairwise comparison matrix for that [articular criteria.
- Step 2
Development of the ratings for every decision alternative made for every criterion by development of the pairwise comparison matrix
- Step 3
Calculation of the average weighted rating for each and every decision alternative. The decision alternative which has the highest score is chosen.
In the AHP method, the pairwise comparisons are utilized in establishment of the relative priority for every criterion which is against another criteria or that is against the decision alternatives. The table below shows the AHP scale which utilizes the ratings from the equal importance to the extreme importance.
| Scale of Importance | Explanation |
| 1 | All with same importance |
| 3 | One is slightly important compared to another |
| 5 | One is just important to another |
| 7 | One is very important compared to another |
| 9 | One is completely important compared to another |
| 8,6,4,2 | When compromise is required |
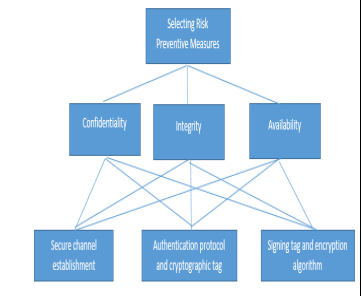
From the table above, a hierarchy of decision is designed for the purpose of making decision on the highest priority countermeasures of the NFC. On comparison in order to know give the confidentiality, establishment of the secure channels is considered as very crucial as compared to use of the authentication protocol or the cryptography. On the other hand, the use of the protocol is considered to be more important as compared to use of encryption. From the comparison above, the establishment of the secure channel as a priority of 0.7611, utilization of the protocol has a priority of 0.1663 and the use of the tags containing the encryption has a priority of around 0.0726 [11].
On the comparison for provision of integrity, it is seen that establishment of secure channel is regarded as more important as compared to the cryptography as well as the authentication protocol. As compared to the protocol, the establishment of the secure channels is also considered more important. However, utilization of the protocols is slightly important as compared to signing of the tag using the encryption. The establishment of a secure channel is prioritized at 0.7503, the utilization of the protocols is prioritized at 0.1714, as finally the use of the signing tags in encryption is prioritized at 0.0782 [11].
When comparing priorities in terms of availability provision, it is noted that the establishment of a secure channel is regarded as more important as compared to the use of authentication protocol as well s the cryptography. The establishment of a secure channel is also regarded as more important as compared to the use of protocol. However, the use of protocol is noted to be slightly important as compared to the use of signing tag with the use of encryption. The establishment of secure channel is prioritized at 0.7172, the utilization of the protocol is prioritized at 0.1947 and the utilization of signing tag by the use of encryption is prioritized at 0.0881 [11].
TABLE 6 HERE
| Alternatives | Integrity | Confidentiality | Availability | Priority |
| Priority 1 | 0.7503 | 0.7611 | 0.7172 | 0.7429 |
| Priority 2 | 0.1663 | 0.1714 | 0.1947 | 0.1775 |
| Priority 3 | 0.0726 | 0.0782 | 0.0881 | 0.0796 |
The overall priority of the AHP for every alternative as shown in the able above is calculated using all the pairwise comparison of alternatives in accordance to CIA.
The highest priority which is obtained by the calculations of the AHP is aimed to establish a secure channel which is having a priority of 0.7429 that when converted to percentage, it comes to 74.29%. Measures of prevention like the use of cryptography as well as the authentication protocol is also prioritized at 0.1775 which is equivalent to 17.75 %. The signing tag using the encryption algorithm is prioritized at 0.0796 which is equivalent to 7.96%. Therefore, it is worthy noting that the establishment of the secure channel is having an overall priority of 74.29% which in return makes the best risk countermeasure solution for the prevention of data corruption as well as Dos attacks in the NFC[11]. From the analysis therefore the best solution for the dos attacks and data corruption prevention is the establishment of the secure channels which according to the analysis, it has a priority of 74.29%. All type of attacks in the NFC communication such as the eavesdropping, and many others are able to be prevented by the solution. The protocol which could be utilized in the establishment of the secure channel in the NCF is the Diffie-Hellman which is based on the RSA or the Elliptic Curves Cryptography. As from the data which was collected from interviews, the participants made an overall suggestion that 3DES to be used for shorter transaction which requires shorter time of response and RSA to be used for longer response time for transactions.
CONCLUSION
From the analysis and evaluation, it is noted that, in this research, there are two contributions which have been made, using the MIDAS system, a guideline solution is proposed in order to put security to the NFC application. As from the analysis, the ECC as well as the AES are considered to be the best techniques for the establishment of the secure channel in the NFC and also in the prevention of the data corruption and the DOS attacks in the NFC [13]. It is found out that the results, findings as well as the cryptographic techniques are all similar and they correlate to each other as the standards for the mechanism of NFC. On the basis of the research significance, and methods, the possibility of the NFC security risk as been determined by evaluation of the risk by the use of risk assessment methods whereby the highest risk which are determined was data corruption and dos attacks. The impediment of this exploration includes the quantity of members that take an interest in online review and the quantity of NFC specialists. The result results from hazard evaluation procedure is associated to the quantity of testing size. Diverse examining size or gathering can have affected the result results. For further research, distinctive hazard appraisal technique can be utilized to assess the security chances in NFC. Other MCDM strategies can be considered to actualize in this examination as to choose the best answer for counteract security assaults. Other than sensitive use of NFC, other NFC application can be tried as to decide the probability of its security dangers.
References
[1]B. Borchert and M. Günther, “Indirect NFC-Login on a Non-NFC Device using an NFC-Smartphone”, International Journal of Intelligent Computing Research, vol. 4, no. 4, pp. 358-364, 2013. Available: 10.20533/ijicr.2042.4655.2013.0047.
[2]L. Francis, G. Hancke, K. Mayes and K. Markantonakis, “On the security issues of NFC enabled mobile phones”, International Journal of Internet Technology and Secured Transactions, vol. 2, no. 34, p. 336, 2010. Available: 10.1504/ijitst.2010.037408.
[3]K. Grassie, “Easy handling and security make NFC a success”, Card Technology Today, vol. 19, no. 10, pp. 12-13, 2015. Available: 10.1016/s0965-2590(08)70134-8.
[4]Y. Jang, S. Chang and Y. Tsai, “Smartphone security: understanding smartphone users’ trust in information security management”, Security and Communication Networks, vol. 7, no. 9, pp. 1313-1321, 2013. Available: 10.1002/sec.787.
[5]H. Kim, “Investigation on NFC-based Security System for Smart Work”, Journal of Security Engineering, vol. 11, no. 3, pp. 263-272, 2014. Available: 10.14257/jse.2014.06.06.
[6]A. Mylonas, A. Kastania and D. Gritzalis, “Delegate the smartphone user? Security awareness in smartphone platforms”, Computers & Security, vol. 34, pp. 47-66, 2013. Available: 10.1016/j.cose.2012.11.004.
[7]J. Geon Pak, B. Ram Lee and M. Suk Lee, “Implementation of Mobile Smart Key System using the NFC Function of the Smartphone”, International Journal of Engineering & Technology, vol. 7, no. 44, p. 1, 2018. Available: 10.14419/ijet.v7i4.4.19589.
[8]S. Poddar, “Central Locker System for shopping mall using NFC Based Smartphone”, Transactions on Networks and Communications, vol. 2, no. 5, 2014. Available: 10.14738/tnc.25.520.
[9]”NFC Phones Raise Opportunities, Privacy And Security Issues”. [Online]. Available: https://cdt.org/blog/nfc-phones-raise-opportunities-privacy-and-security-issues/. [Accessed: 2019].
[10]”Security Risks of Near Field Communication Technology”. [Online]. Available: http://nearfieldcommunication.org/nfc-security-risks.html. [Accessed: 2019].
[11]”Security Issues in Mobile NFC Devices | Request PDF”. [Online]. Available: https://www.researchgate.net/publication/266557612_Security_Issues_in_Mobile_NFC_Devices. [Accessed: 2019].
[12]”Concerns Related to NFC Technology for Payments [Updated 2019]”. [Online]. Available: https://resources.infosecinstitute.com/nfc-technology-payments-concerns/. [Accessed: 2019].
[13]”Mobile Payments: Risk, Security and Assurance Issues”. [Online]. Available: https://www.isaca.org/Groups/Professional-English/pci-compliance/GroupDocuments/MobilePaymentsWP.pdf. [Accessed: 2019].
Role of Campus Safety Partner in addressing a cultural mind shift
Agenda
The agenda is to address a cultural mind shift by partnering with faculty, staff members, student, and the local community.
This mind shift is relating to recent highly charged social and political activism on the campus of the University of Washington (UW) as a result of hate crimes and other activities relating to racism.
The mind shift will be achieved through collaborative engagement and policy development, which will be achieved through use of social media campaigns and diversity training programs.
Current Issues in Campus
One of a key challenge which is faced by students, staff, and faculties in UW is hate crimes and other issues that promote racism and biases.
As a director, it is important to understand the severity of these issues and address the change in the campus community to create a peaceful environment.
A new study by UW found that 40 percent of blacks face challenges in school and work as a result of hate crimes (EPI News, 2019).
The attack on a Muslim student in campus of UW is another example of current issues in the campus (Hyde, 2016).
Addressing change in campus community
The issue of hate crime is necessary to be addressed to make sure that it did not negatively affect students, staff, faculty and other members in the local community.
This can be achieved with a collaborative approach within the members of the community to make sure that they work together to fight these challenges (Linder, Myers, Riggle & Lacy, 2016).
Social and political activism and protests started by students of UW are good examples which show how they stand up against these issues.
Awareness regarding these issues should be spread to make sure that their numbers can be reduced and victims receive a platform to share their challenges.
Actions to address the issues
Collaborative engagement is required between community members to address these issues, which can be achieved if the University embraces student activism.
There are positive outcomes for students through embracing activism along with the community, as found in the study conducted on the University of Iowa and the University of Michigan.
Another good example of collaborative engagement is Ferguson protests that bring people together to take actions for the protection of black lives and universities stated providing diversity training to student (CBS News, 2019).
Actions to address the issues
The University should focus on policy development in order to positively respond to social and political activism.
Engagement between students, faculty, and staff is necessary to ensure that they positively engage in social and political activism.
Online collaboration should be given through social media sites and forums to ensure that people have their voices heard (Sandoval-Almazan & Gil-Garcia, 2014).
Resources available for addressing the issues
Social media sites such as Facebook, Instagram, and YouTube are great tools to spread awareness and bring spotlight on victims of hate crimes (Sandoval-Almazan & Gil-Garcia, 2014).
Diversity training is also crucial to prohibit hate crimes and similar practices from the campus.
The University should create a separate fund to support social and political activism practices by students and other members.
Opinion of other writers
Laurie Essig wrote a great piece for “the Chronicle” on cultural minded and political activism by arguing that hate crimes won’t end until “toxic ‘bro’ culture” is reformed (Essig , 2018).
In the article, she highlighted that campus students are more likely to engage in “bro” culture, and they write words such as “die dykes” and “feminazi” on women-center posters (Essig , 2018).
Campuses did not take strict actions against these actions, and they did not embrace social and political activism, which fuel these activities and increase the number of hate crimes.
Opinion of other writers
Dan Bauman analyzed the impact of cultural mindedness and political activism by comparing the data of hate crimes in campuses by posting an article in “the Chronicle”.
He argued that the issue of hate crimes had increased drastically, especially among campuses, which are mainly against blacks (Bauman, 2018).
These crimes promote biases and affect the personal, professional, physical and mental health of students.
Bauman provided that four hate crimes incidents were reported in Seattle campus of UW in 2017 and other universities have reported more incidents (Bauman, 2018).
Universities that did not support social and political activism have higher rate of hate crime cases.
Campus Climate Survey
The campus climate survey reported a number of hate crime incidents in UW.
A hate crime was reported after 2016 Presidential elections against a Muslim student when she suffered a concussion after someone threw a bottle (Dreid & Najmabadi, 2016).
In another incident, Muslim students were threatened because they were wearing a hijab in the campus (Dreid & Najmabadi, 2016).
These surveys highlighted key challenges that promote hate crime in the campus.
Campus Climate Survey
There is lack of strict policy development and no strict actions are taken against individuals that engage in similar practices.
Policy development can ensure that collaboration is achieved and the campus supports social and political activism among students.
There is no collaboration between students, faculty and staff members which highlight the importance of a diversity training program (Dreid & Najmabadi, 2016).
Communication should be improved through use of social media sites and online forums where people should share their ideas and views against hate crimes and how to address them.
Outreach programs and other engagement and collaboration to build community
A cultural mind shift is necessary in order to make sure that the issue of hate crimes and racism are addressed in the campus of UW.
This can be achieved through collaboration between students, faculty, and staff members through diversity programs (Laninga, Austin & McClure, 2019).
UW should launch an outreach program as well to promote diversity in the workplace and eliminate racist behavior.
International Peer to Peer mentor program can increase the number of diverse
Outreach programs and other engagement and collaboration to build community
Protests conducted by students should be supported by the University since it raises awareness regarding major social and political issues.
However, guidelines should be introduced through policies to make sure that protests did not harm individuals, and they assist in supporting the overall goals of the university.
Diversity training should become mandatory, and stricter policies should be introduced for punishing those that engage or promote hate crimes or other racist practices.
Training should be given across generations in which older as well as Generation Z students should be included (Laninga, Austin & McClure, 2019).
Outreach programs and other engagement and collaboration to build community
Effective communication is also crucial for achieving the agendas of social and political activism.
This can be achieved by the university by holding meetings and supporting online discussion through social media sites.
Victims should be given a platform to share their stories with the world which will raise awareness regarding these issues, and it will reduce the number of hate crimes in campuses (Laninga, Austin & McClure, 2019).
Partnership with student affairs, global study programs and equity and inclusion programs are significant for ensuring a cultural mind shift.
Conclusion
As a culture safety partner, it is recommended that universities should embrace social and political activism.
The issue of hate crime can be resolve through a cultural mind shift of students, faculty and staff members.
Diversity training, social media awareness and policy development is crucial to achieve a cultural mind shift that embrace social and political activism.
References
Bauman, D. (2018). Hate Crimes on Campuses Are Rising, New FBI Data Show. Retrieved from https://www.chronicle.com/article/Hate-Crimes-on-Campuses-Are/245093
Beekman, D. (2019). Reported hate crimes and incidents up nearly 400% in Seattle since 2012. Retrieved from https://www.seattletimes.com/seattle-news/crime/reported-hate-crimes-and-incidents-up-nearly-400-in-seattle-since-2012/
CBS News. (2019). We asked 155 police departments about their racial bias training. Here’s what they told us. Retrieved from https://www.cbsnews.com/news/racial-bias-training-de-escalation-training-policing-in-america/
Dreid, N. & Najmabadi, S. (2016). Here’s a Rundown of the Latest Campus-Climate Incidents Since Trump’s Election. Retrieved from https://www.chronicle.com/blogs/ticker/heres-a-rundown-of-the-latest-campus-climate-incidents-since-trumps-election/115553
EPI News. (2019). Blacks, Minorities Disproportionately Impacted By Hate Crimes. Retrieved from https://epi.washington.edu/news/blacks-minorities-disproportionately-impacted-hate-crimes
Essig, L. (2018). Hate Crimes Won’t End Until Toxic ‘Bro’ Culture Is Reformed. Retrieved from https://www.chronicle.com/article/Hate-Crimes-Won-t-End-Until/243046
Hyde, D. (2016). Hate crime? Muslim student attacked at University of Washington. Retrieved from https://www.kuow.org/stories/hate-crime-muslim-student-attacked-university-washington
Laninga, T., Austin, G., & McClure, W. (2019). University-community partnerships in small-town Idaho: Addressing diverse community needs through interdisciplinary outreach and engagement. Journal of Community Engagement and Scholarship, 4(2), 2.
Linder, C., Myers, J. S., Riggle, C., & Lacy, M. (2016). From margins to mainstream: Social media as a tool for campus sexual violence activism. Journal of Diversity in Higher Education, 9(3), 231.
Sandoval-Almazan, R., & Gil-Garcia, J. R. (2014). Towards cyberactivism 2.0? Understanding the use of social media and other information technologies for political activism and social movements. Government Information Quarterly, 31(3), 365-378.