- Introduction
Penetration testing is a practice that involves a simulated attack against a computer system meant to exploit the vulnerabilities in the system. The attempt to breach the security of an application with the intent of gaining access to the system and bypassing the administrative privileges is the main aim of attackers. In the context of web applications, penetration testing is the act that is used to augment and the firewalls and intrusion detection systems[1].
The necessary information which is used to gain access to the system is collected using network mapping and reconnaissance tools. The main objective of this project is to identify the security weaknesses in an active system with the intent of exploiting the systems. Security threats and weaknesses are used to provide managers and the administrators of the system to upgrade security policies to enhance the detection and prevention of the attacks in real-time. The time taken to perform the penetration testing and collection of usage information depends on the size of the organization and the number of users connected to the network at a given instance.
- Vulnerability Assessment
The process used in the identification and ranking of the threats and the vulnerabilities which are found in a system. Assessment involving the identification of the threats are performed based on the following steps:
- Collecting information and accessing system vulnerabilities.
- Ranking the threats and the vulnerabilities based on risk.
- Identifying the potential threats of the vulnerabilities to the existing system.
- Prevention and mitigation against the attacks.
The project is based on the assessment of the following challenges:
- Remote System discovery.
- Administrative privilege escalation.
Vulnerability analysis is involved with the detection and assessment of the consequences and the risk of the threats to the system. The factors which affect the performance of the system and the organization’s resources are based on an automated system that is used to monitor the logs.
Privilege escalation is a technique that is used to elevate the normal functions and the permissions granted to a normal user accessing the system. Privilege escalation enables the attackers to gain unauthorized access to the system resources[2].
Network mapping is used to identify the infrastructure based resources and the services which are executing in the instance of the installed applications. This process is used to enhance the process of system discovery which enables attackers to gain access to the system by bypassing the normal functioning of the system.
- Attach Methodology
The phases involved in the attack procedure can be identified as follows:
- Reconnaissance- Collection of information used during the enumeration of the user’s group.
- Scanning – The data which is obtained from scanning the networks is used to map the network resources to ease accessibility by the attackers.
- Gaining access – Successful exploitation of the system using known vulnerabilities enables the attackers to gain access that is used to steal data.
- Maintaining access – After gaining access to the system, post-exploitation modules and exploits are executed to ensure the attackers can be able to gain later access and elevate to administrative privileges.
- Covering – This is the phase that is involved in deleting logs and reports generated due to authorized access to the system. Tracks and Logs are used to detect the origin of the attacks and the intent of the attackers.
Tools used to perform analysis and scanning of the network issues and threats include:
- Nikto.
- Wireshark.
- OpenVas.
- Nessus.
Remote system discovery.
Figure 1:Gain access to network information.
Figure 2:Zone transfer information.
Figure 3:Internal network information and data.
Figure 4:Gaining a meterpreter session.
A meterpreter session is used for the execution of commands to a remote target.
Figure 5: Encryption and decryption of keys.
Figure 6:msfconsole
Metasploit is the framework that is used to perform penetration testing against the target network due to its abundance in exploits[3].
Figure 7: meterpreter command session.
- Implication
In the case that an attacker gains access to a real website or an application based architecture, the intent of the exploitation depends on the resources in the organization[4]. Some of the impacts of the attack on the organization include :
- Data theft – Information and data is the core reason for the increased attack on the organization.
- Loss of confidential information – most attackers would breach the network security of a premise to gain access to data and perform data manipulation.
- Malicious intent – The data accessed can be used for illegal activities.
- Denial of service – These attacks are used to deny access to privileged users the right to get access to the systems they use.
Financial and banking institutions are mainly the target of most of the attacks whose intent is to gain access to data and information sources. The methodology used to initiate the attacks depends on the security and the protocols used in sharing and access to information. The risk in data loss is evaluated based on amounts of data targeted in the attacks.
- Conclusion
Information security is an interdisciplinary field that involves securing the integrity of the data owned by the organization. The main objective of this project was the identification and implementation techniques that can be used to enhance the performance of the systems and patch updates made. Encryption is a technique that can be used to ensure that the data shared between the users is not known to the attackers[5].
The attackers can be able to intercept the data in the form of plaintexts, this therefore means that the data must be encrypted and only cipher contents are transmitted to the clients. Different security features can be used as mitigation procedures that prevent malicious users the access to such information.
Tools used to test the vulnerabilities present in the target system are configured depending on the security features that need to be implemented to leverage on the threats. Mapping utilities are network programs used for scanning into both internal and external networks to check for security threats[6].
- References
[1] “VULNERABILITY ASSESSMENT & PENETRATION TESTING (VAPT)”,International Journal of Recent Trends in Engineering and Research, vol. 4, no. 3, pp. 326-330, 2018. Available: 10.23883/ijrter.2018.4135.tru9k.
[2]”Vulnerability Assessment and Penetration Testing through Artificial Intelligence”,International Journal of Recent Trends in Engineering and Research, vol. 4, no. 1, pp. 217-224, 2018. Available: 10.23883/ijrter.2018.4028.rdd10.
[3] “CONE PENETRATION TESTING — CURRENT DEVELOPMENT TRENDS”,Геотехника, vol., no. 42019, pp. 56-67, 2019. Available: 10.25296/2221-5514-2019-11-4-56-67.
[4] “Kali Linux – Assuring Security by Penetration Testing”,Network Security, vol. 2014, no. 8, p. 4, 2014. Available: 10.1016/s1353-4858(14)70077-7.
[5]E. Schultz, “Hackers and penetration testing”,Network Security, vol. 1997, no. 10, p. 10, 2016. Available: 10.1016/s1353-4858(97)85736-4.
[6] “Metasploit Penetration Testing Cookbook”,Network Security, vol. 2013, no. 11, p. 4, 2013. Available: 10.1016/s1353-4858(13)70125-9.
Hack Challenges in CTF Penetration Testing
Penetration Testing
Penetration testing is the act of emulating a security breach on a given target network in attempt to establish the network susceptibilities.
It is usually an authorized kid of security breach. The top management authorizes the hired party to attack their network.
Penetration Testing
Depending on the Penetration testing framework, the first step in the testing process is to gather the network intelligence to be able to pin-point the likely vulnerabilities that could be exploited.
NIST framework for instance collects intelligence with an aim of establishing the vulnerabilities that the network may be possessing. The saves the ethical hacker the time of exploring the vast network identifying vulnerabilities in each network infrastructure.
Vulnerabilities and exploit
A vulnerability in network is a weakness that can be easily exploited by an attacker to gain access to a given network. In this the access is authorized by it is performed with the full knowledge of the target network’s top management team.
Most the network infrastructure depicts different vulnerabilities some arising from the manufacturer while some from the rogue configurations during the implementation of network after designing.
In the intelligence collection phase, it was identified that the CTF network was vulnerable to DNS zone transfer.
DNS zone transfer
This vulnerability can allow attackers to replicate the organization’s data and databases.
It is also referred to as DNS query AXFR, usually performed from the command prompt.
Below is a picture of the CTF’s website
This vulnerability can allow attackers to replicate the organization’s data and databases.
It is also referred to as DNS query AXFR, usually performed from the command prompt.
Below is a picture of the CTF’s website
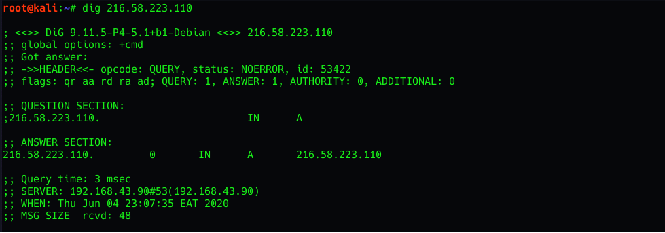
How the attack was performed
This attack followed as series of steps to be completed.
These include;
Reconnaissance- Collection of information used during the enumeration of the user’s group.
Scanning – The data which is obtained from scanning the networks is used to map the network resources to ease accessibility by the attackers.
Implications of Zone Transfer
The implications of zone transfer can be dire to any given organization. This will generally affect the confidentiality and the integrity of the CTF’s information.
Confidentiality and integrity are information properties that should never be compromised. Most of the Information System’s information is sensitive and a leak to the public may mean a lot of harm to the respective business processes of the organization.
Implications of Zone Transfer
In the case that an attacker gains access to a real website or an application based architecture, the intent of the exploitation depends on the resources in the organization[4]. Some of the impacts of the attack on the organization include :
Data theft – Information and data is the core reason for the increased attack on the organization.
Loss of confidential information – most attackers would breach the network security of a premise to gain access to data and perform data manipulation.
Malicious intent – The data accessed can be used for illegal activities.
Denial of service – These attacks are used to deny access to privileged users the right to get access to the systems they use.
Conclusion
In conclusion, the security of a given network is not a debatable subject. Every Information System must be secure to the best levels possible and be updated more often to keep up with the ever emerging security challenges. Company’s data may be safe with stringent security configurations that averts threats like zone transfer.
Reference List
[1] “VULNERABILITY ASSESSMENT & PENETRATION TESTING (VAPT)”,International Journal of Recent Trends in Engineering and Research, vol. 4, no. 3, pp. 326-330, 2018. Available: 10.23883/ijrter.2018.4135.tru9k.
[2]”Vulnerability Assessment and Penetration Testing through Artificial Intelligence”,International Journal of Recent Trends in Engineering and Research, vol. 4, no. 1, pp. 217-224, 2018. Available: 10.23883/ijrter.2018.4028.rdd10.
[3] “CONE PENETRATION TESTING — CURRENT DEVELOPMENT TRENDS”,Геотехника, vol., no. 42019, pp. 56-67, 2019. Available: 10.25296/2221-5514-2019-11-4-56-67.
[4] “Kali Linux – Assuring Security by Penetration Testing”,Network Security, vol. 2014, no. 8, p. 4, 2014. Available: 10.1016/s1353-4858(14)70077-7.
[5]E. Schultz, “Hackers and penetration testing”,Network Security, vol. 1997, no. 10, p. 10, 2016. Available: 10.1016/s1353-4858(97)85736-4.
[6] “Metasploit Penetration Testing Cookbook”,Network Security, vol. 2013, no. 11, p. 4, 2013. Available: 10.1016/s1353-4858(13)70125-9.