Introduction
Web security is the procedure to protect the information and the data that are stored in the system. Nowadays, all type of organizations is impacted by cyber threats. The risk analysis is the fundamental methodology for helping to manage this type of issues (Velásquez et al., 2018). With this risk analysis, the organizations can assess all the risks that are affected by the belongings of them. Also, the security controls that they need to execute for decreasing the probability of this type of cyber threats and the probable impacts should occur by the help of this risk analysis. In this discussion, the literature review of web security is discussed. With the risk analysis also the algorithms are described which are used to mitigate the cyber threats and secure the web. The comparison of these algorithms using table and figures are mentioned in this discussion.
Discussion
Literature Review
The cybersecurity is an activity to protect the information and also the information systems such as the networks, databases, computers, applications and data centres with proper measures of procedural also technological security.
According to Rekik et al., (2018), to safeguard the personal data and computer networks, the antivirus software, firewalls and any other technical solutions are so much important nut it is not enough to confirm the security of the web. Primarily, the issues of Cyber-Safety, Cyber-Ethics and also the Cyber-Security are required to integrate. The measures of the security counter are helped to confirm confidentiality, availability, and also the integrity of the information systems by mitigating the asset losses from the attacks of cybersecurity (Iskandar et al., 2018). In recent times the cybersecurity has developed as the recognized correction for the computer systems and the infrastructures with the focus on the security of the valued information that is stored on these systems from challengers who is wished for obtaining, corrupting, damaging, destroying or prohibiting the access to it. There are several system presents which can help to analyse what happens in the time of the execution also tries for finding the indications of misusing the computer, for example, the Intrusion Detection System (IDS). There is a huge variation of probable approaches to improve cybersecurity in upcoming years. All these methods were measured as the Heterogeneity, Encouraging the Secure Behaviour also the Wellness of Cyber.
Risk Analysis
The risk analysis is the important methodology for the cybersecurity as this is permitted the organizations for dealing with the cyber threats that are possibly affected them, prioritize defenced of the assets and decided that what the security controls should implement. Several methods of risk analysis are available in the model of cybersecurity, compliance the frameworks and the international standards (Schatz & Bashroush, 2017).
In the risk analysis procedure, four steps are present which are as follows:
i) Recognizes the threats, assets and the vulnerabilities of the selected organization and evaluate them
| Asset | Threat | Vulnerability |
| 1. Information/Data 2. Human Resource 3. Hardware 4. Software 5. Documents6. Circumstances | 1. Network/Physical 2. Human/Non-human3.Technical/Environment 4. Accidental/Deliberate5. Inside/Outside | 1.Administering Documents, Regulation 2. Physical Facilities 3. Technical Hardware, Software. |
ii) The identified outputs of the previous step are applied to the risk analysis.
iii) The appropriate methods of risk mitigation are used to reduce the possible threats for assets.
iv) In this step, the primary risks, types and the cost of the methods of risk mitigation, remaining risks and the Return-On-Investment (ROI).
These four steps of the risk analysis procedure are helped decision-makers to optimize the resources for minimizing the risks of web security.
Different Algorithms
There are several algorithms available such as the DES algorithm, AES algorithm, RSA algorithm in web security.
i) DES algorithm
It is the block cipher with the block size of 64 bit also the key of 56 bit. It is contained of the series of 16 round of the substitution also the permutation (Van Den Berghe et al., 2017). In each of the round, the data also the key bits are permutated, shifted also sent via 8s boxes, the set of the tables of lookup which are important to this algorithm.
ii) AES algorithm
This is used the rounds of 10, 12 and 14. The key size which can be the 128, 192 or 256 bits and also depended on the several numbers of the rounds. This algorithm is applied to various rounds where every round is created by many phases. For providing security, the AES is applied to many types of transformation.
iii) RSA algorithm
This is mainly adopted by the algorithm of public-key cryptography. This algorithm is widely used nowadays in several software products and also applied for the exchange of key, digital signatures and many more (Singhal & Ou, 2017). It is used the block of variable size encryption and the key to the size of the variable. Key-pair is described from the very enormous number, n, that is the product of the two prime numbers selected as stated by the superior rules.
The performance of these proposed algorithms is evaluated by considering the resultant parameters which are as follows:
- The computation time
- The usage of the memory
- The output bytes
Comparisons of the algorithms
The comparisons of these proposed algorithms such as the AES, DES and RSA of the time, output byte and memory are as follows:
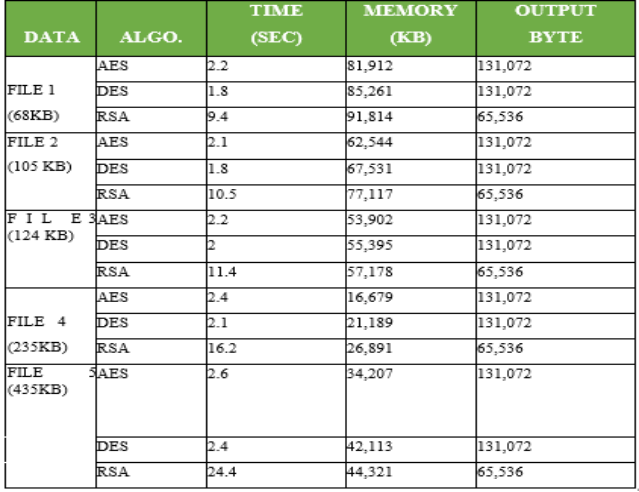
Table 1: Comparison of AES, DES and RSA of time, memory and output bytes
(Source: Van Den Berghe et al., 2017)
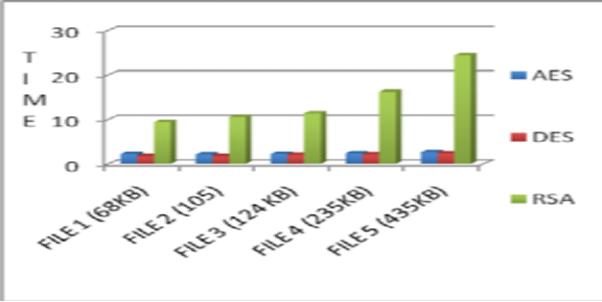
Figure 1: Comparison of the time of computation between the AES, DES and RSA
(Source: Singhal & Ou, 2017)
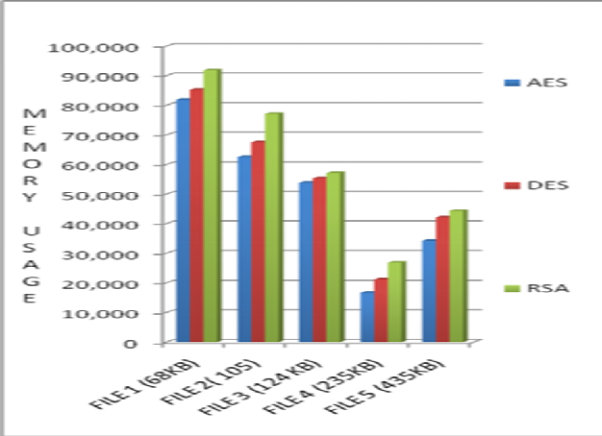
Figure 2: Comparison of the usage of the memory by the AES, DES and RSA
(Source: Abdo et al., 2018)
Figure 2: Comparison of the output byte by the AES, DES and RSA
(Source: Jillepalli et al., 2018)
Conclusion
From the above discussion, this can be concluded that web security is nowadays so much important for the organizations. For mitigating the cyber threat, some algorithms are required to implement such as the DES, RSA and the AES. The literature review and the risk analysis of web security are properly described in this discussion.
References
Abdo, H., Kaouk, M., Flaus, J. M., & Masse, F. (2018). A safety/security risk analysis approach of Industrial Control Systems: A cyber bowtie–combining new version of attack tree with bowtie analysis. Computers & Security, 72, 175-195.
Iskandar, A., Tuasamu, M.R.F., Syamsu, S., Mansyur, M., Listyorini, T., Sallu, S., Supriyono, S., Saddhono, K., Napitupulu, D. & Rahim, R., (2018, September). Web based testing application security system using semantic comparison method. In IOP Conference Series: Materials Science and Engineering (Vol. 420, No. 1, p. 012122). IOP Publishing.
Jillepalli, A. A., Conte de Leon, D., Steiner, S., & Alves-Foss, J. (2018). Analysis of Web Browser Security Configuration Options. KSII Transactions on Internet & Information Systems, 12(12).
Rekik, R., Kallel, I., Casillas, J., & Alimi, A. M. (2018). Assessing web sites quality: A systematic literature review by text and association rules mining. International Journal of Information Management, 38(1), 201-216.
Schatz, D., & Bashroush, R. (2017). Economic valuation for information security investment: a systematic literature review. Information Systems Frontiers, 19(5), 1205-1228.
Singhal, A., & Ou, X. (2017). Security risk analysis of enterprise networks using probabilistic attack graphs. In Network Security Metrics (pp. 53-73). Springer.
Van Den Berghe, A., Scandariato, R., Yskout, K., & Joosen, W. (2017). Design notations for secure software: a systematic literature review. Software & Systems Modeling, 16(3), 809-831.
Velásquez, I., Caro, A., & Rodríguez, A. (2018). Authentication schemes and methods: A systematic literature review. Information and Software Technology, 94, 30-37.