A report on biometrics in e secure transaction
Biometrics is highly used in many processes and it provides better in results in terms of security and privacy. It is the next level of security. From the last two decades, most of the companies adopt biometric devices in many processes for identification of the person (Bobde & Satange, 2013).
In addition, mobile applications are used to identify the user and provide access to a system. It is the best way to identify a person. In the present time, transactions are possible through fingerprints through a mobile application, such as Google pay, phone pay, and many others. Those applications take a five sample of the figure of a person to authorize for a particular transaction from their mobile application.
Most of the smartphone is having a finger scanner and it is used to identify a person through biometrics. It provides two most important benefits, which are physically present for identification, and no need to remember a password or PIN number (Mahto & Yadav, 2017).
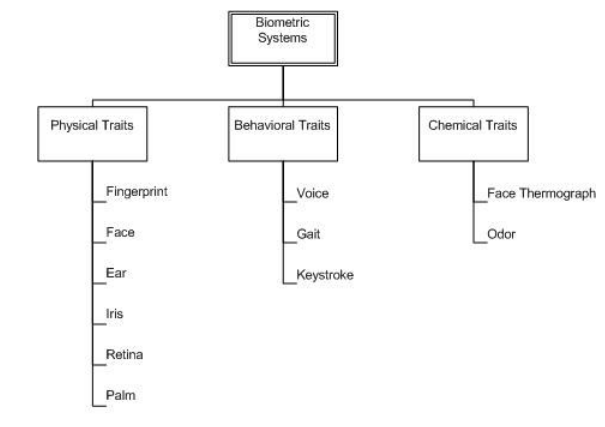
Source: (Bobde & Satange, 2013)
It is having three basic types, which are physical traits, behavioral traits, and chemical traits. In transactions, physical traits are mostly used, such as fingerprint, face, and others.
Sensor-level fusion can be distributed in three classes, which areas:
1. Single sensor-multiple instances,
2. Intra-class multiple sensors, and
3. Inter-class multiple sensors.
Source: (Bobde & Satange, 2013)
Biometric imaging software is installed in the smartphones and it takes samples of fingerprint and stores them into the database, which is used to the comparison between stored and present time samples for authentication.
Moreover, it is fast and suitable for customers to use biometrics in their transactions. The banking sector is also feeling better after this technology because of fewer issues in terms of security and frauds. In addition, it is better for both customers and banks. Third party software is helping into this feature, such as Google Pay (Gladis, 2018).
However, sometimes it faces a few issues in different conditions. As an example, the user got a mark on the figure and the sensor is not sense properly. In that case, it provides alternatives, which are PIN numbers or password, which has been generated by the user only at the time of the creation of biometrics. Biometrics is the best way for transitions and it will use in other things as well, such as attendance, and many others. It is a unique method to secure transactions. However, sometime hacker uses alternatives to hack their mobile phones. It has a few disadvantages as well (Ogbanufe & Kim, 2018).
References
Bobde, M., & Satange, D. (2013). Biometrics in Secure e-Transaction. International Journal of Emerging Trends & Technology in Computer Science, 2(2).
Gladis, R. (2018, December 20). How biometrics will shape the future of mobile authentication. Retrieved from atmmarketplace.com: https://www.atmmarketplace.com/blogs/how-biometrics-will-shape-the-future-of-mobile-authentication/
Mahto, D., & Yadav, D. K. (2017). Security improvement of one-time password using crypto-biometric model. In Proceedings of 3rd International Conference on Advanced Computing, Networking and Informatics (pp. 347-353). New Delhi: Springer.
Ogbanufe, O., & Kim, D. (2018). Comparing fingerprint-based biometrics authentication versus traditional authentication methods for e-payment. Decision Support Systems, 1-14.