Institution
Student Name
Student ID
Instructor
Date of submission
Table of contents
1.6 Functional and Non-Functional Requirements for the Job Portal
1.0 Introductions
The Job Portal of Elevate Workforce Solutions is a unique web application that efficiently matches job seekers with prospective employers. It addresses the challenge of a scattered job market by providing a secure, centralized platform for users to sign up, view job listings, and apply for positions. It enables companies to post and manage jobs. The portal, developed with the Model-View-Controller (MVC) architecture and object-oriented practices, offers a comprehensive range of functionalities, including authentication, job management, and application tracking.
1.2 Problem statement
Employers and job seekers face significant challenges in today’s fiercely competitive job market. Employers struggle to find qualified candidates, while job seekers often miss out on good opportunities. This urgency is underscored by past and current LinkedIn surveys, which revealed that 70% of job seekers Are frustrated with slow or outdated portals, and 61% of hiring managers find it inefficient to manage applications through traditional channels like email or paper resumes(Abrahams et al.,2023).
Elevate Workforce Solutions has no customized online facility that makes hiring and application procedures easier. This lapse prevents them from swiftly aligning people with vacant positions and slows operations. Indeed.com revealed that organizations that applied centralized job portals saved 30% of the time it took to fill a job and increased applicant satisfaction by 45%( Zarour et al.,2021).
An up-to-date, safe, and easy-to-use job portal is not a luxury anymore, as more than 90% of the job search has started online(Rani et al.,2022). The requirement of features, such as role-based dashboards, real-time applications tracking, and responsive design, is essential to the fulfillment of the expectations and goals that candidates place on the organizations in which they apply to work (Jones, K.I. and Suchithra R., 2023). Therefore, the creation of a bespoke job portal for Elevate is a solution that is well timely and strategic enough to fill this digital recruitment gap.
1.3 Risk Analysis Matrix
| Risk ID | Risk Description | Likelihood | Impact | Risk Level | Mitigation Strategy |
| R1 | Unauthorized access or data breach | Medium | High | High | Implement HTTPS, strong authentication (bcrypt hashing), and role-based access control. |
| R2 | Feature creep (adding too many features) | High | Medium | High | Strict scope definition, agile sprints, client sign-offs after each phase |
| R3 | Delayed development due to time constraints | Medium | High | High | Create sprint-based task tracking, prioritize features, and regular team standups. |
| R4 | Lack of user engagement or adoption | Medium | Medium | Medium | Conduct UX testing, ensure responsive/mobile-friendly UI, and gather user feedback. |
| R5 | Server or hosting failure | Low | High | Medium | Use reliable cloud hosting (e.g., Heroku, AWS), enable daily backups |
| R6 | Poor performance under load (many users) | Low | Medium | Low | Optimize database queries, use pagination, test with load simulation |
| R7 | Miscommunication within the development team | Medium | Medium | Medium | Weekly meetings, shared documentation, use of project management tools (e.g., Trello, GitHub Issues) |
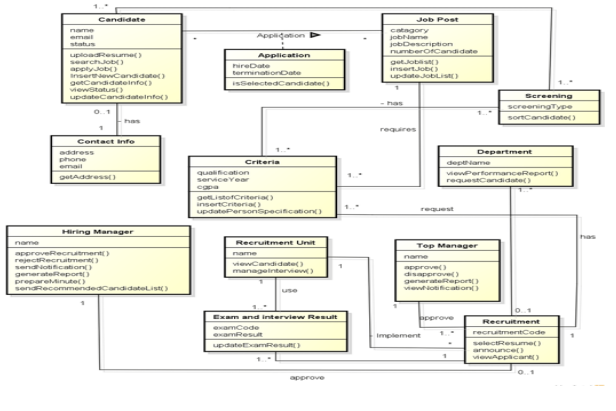
1.4.1 Class diagram
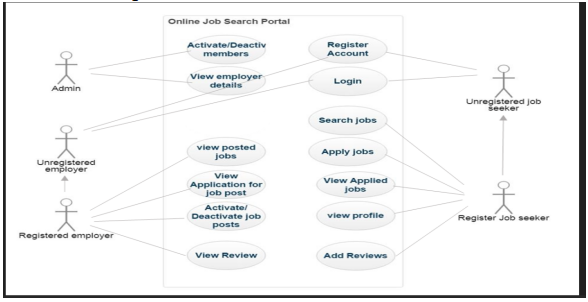
1.4.2 Use case diagrams
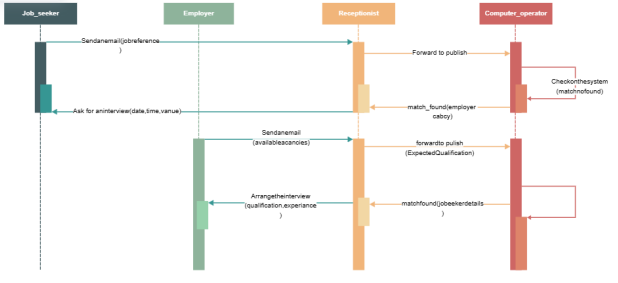
1.4.3 Sequence diagram
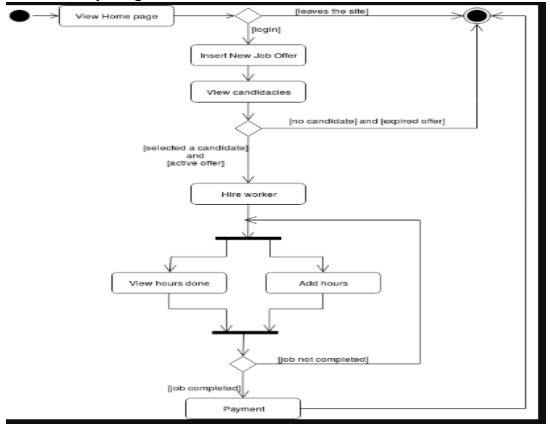
1.4.4 Activity Diagrams
1.5 Technology stack
The technology stack around which the Job Portal of Elevate Workforce Solutions will be formed will include PHP as the server-side scripting language and MySQL as the relational database management system(Amine,2021). The open-source nature readily allows PHP to be a widely used language in developing dynamic and data-based web applications because it is easily integrated with HTML and databases and has great community backing. MySQL is the best complement to PHP since it offers reliable, fast, stable data storage that works perfectly on hosting job postings, user profiles, and application records.
The stack is compatible with the Model-View-Controller (MVC) design and focuses on clean code layout (separation of concerns). To extend development further, one can use PHP frameworks, such as Laravel or CodeIgniter, which also offer pre-packaged libraries that handle authentication, route calls, and ORM (Object-Relational Mapping)( Mohammad El-Basioni et al.,2024). On the front end, an automatic responsive interface and ease of use will be achieved with the help of HTML5, CSS3, JavaScript, and Bootstrap, which ensure its possible accessibility in case of any devices.
The PHP-MySQL stack is inexpensive, simple to implement in most hosting systems, and expandable as growth is possible(Al-Badri et al.,2023). It also meshes fine with systems like phpMyAdmin to manage the databases and Composer to manage dependencies. Such a combination provides a secure, efficient, and extensible base that fits Elevate’s hiring and job management needs.
1.5.1 Reason of choices
The decision to use PHP and MySQL as the technology to develop the job portal is due to their use, reliability, and ease of implementation. PHP is a powerful, server-based scripting language that only caters to web programming(Wu,2022). It is fast to create dynamic websites and has good integration with HTML; thus, it would be best to create responsive job listings and user dashboards. MySQL is a relational database that is robust and scalable for managing structured data, including user profiles, jobs, postings, and applications.
MySQL and PHP can make a low-cost, open-source alternative with active community backing and much coverage documentation. Most hosting services support these technologies, so deploying them is not difficult(Amini et al.,2021). Moreover, frameworks like Laravel or CodeIgniter support elements of clean code such as MVC and MySQL, guaranteeing the speed of performing the queries and the safety of data processing. This stack will give a secure, scalable, and maintainable application that fits the needs of recruitment activities at Elevate Workforce Solutions.
1.6 Functional and Non-Functional Requirements for the Job Portal
| ID | Requirement | Description |
| FR1 | User Registration | Users (job seekers and employers) can create new accounts. |
| FR2 | User Login/Logout | Registered users can log in and securely log out of the system. |
| FR3 | Password Recovery | Users can reset forgotten passwords via email verification. |
| FR4 | Role-Based Access | Different roles (Job Seeker, Employer, Admin) have different permissions. |
| FR5 | Job Listing Display | Users can view available job listings with pagination. |
| FR6 | Job Search and Filter | Users can search for jobs by title, company, location, or keywords. |
| FR7 | Job Application | Job seekers can apply for jobs by submitting a form and uploading a CV. |
| FR8 | Application Tracking | Users can view the status of their submitted applications. |
| FR9 | Company Dashboard | Employers can access a dashboard to manage their posted jobs. |
| FR10 | Post a Job | Employers can create and post new job opportunities. |
| FR11 | Edit/Delete Job Postings | Employers can update or remove their posted jobs. |
| FR12 | View Applicants | Employers can view the list of applicants for each job posting. |
| FR13 | Admin Dashboard (Optional) | Admin can manage users and jobs and monitor site activity. |
| FR14 | Email Notifications | The system sends confirmation and notification emails for registration and jobs. |
| FR15 | Session Management | Maintain user sessions across pages by auto-logging out after inactivity. |
| FR16 | Responsive UI | The interface adapts to desktop, tablet, and mobile views. |
| FR17 | Profile Management | Users can update their profile, resume, and contact details. |
| FR18 | Resume Upload | Job seekers can upload and update their resume files. |
| FR19 | Contact/Support Form | Users can send queries or feedback via a contact form. |
Non-Functional Requirements Table
| ID | Category | Requirement |
| NFR1 | Performance | The system must load pages within 2 seconds under normal network conditions. |
| NFR2 | Scalability | The portal should support growth in users, job listings, and companies. |
| NFR3 | Security | Passwords must be hashed (e.g., bcrypt); data transmitted via HTTPS. |
| NFR4 | Usability | The interface must be intuitive, easy to navigate, and require minimal training. |
| NFR5 | Reliability | The system should maintain at least 99% uptime and handle failures gracefully. |
| NFR6 | Maintainability | The codebase must follow OOP and MVC principles for easy maintenance and upgrades. |
| NFR7 | Portability | The application should be compatible with standard web servers (Apache, Nginx). |
| NFR8 | Availability | The portal should be accessible 24/7 except during planned maintenance. |
| NFR9 | Accessibility | The system should comply with WCAG standards to support users with disabilities. |
| NFR10 | Backup and Recovery | Daily backups should be automated and restorable in case of data loss. |
1.7 Methodology Adopted
The incremental development methodology is perfect for creating the Job Portal for Elevate Workforce Solutions, as it is flexible, allows management of conflicts, reduces risk, and constantly integrates feedback(Omachi & Ajewumi,2024). Rather than finishing the whole project, this method is divided into smaller manageable modules, with every iteration providing a functioning part of the system e.,g. us, er authentication, job listing, or employer dashboards. Those increments are conceived, tried, and implemented gradually. Thus, a problem can be noticed early, and improvements can be achieved gradually(Carreno,2024).
Among the key advantages is an opportunity to provide initial functions early on, allowing stakeholders to communicate with the system and leave feedback. This brings them closer to their users’ expectations and helps them rapidly adapt to a changing need. Incremental development also enhances the monitoring and management of resources in the project when specific achievable milestones are targeted(Nazarova & Rudenko,2023). The long-term advantage of the methodology is that it improves the quality, maintainability, and user satisfaction of the final product. It also dips the risk in development by validating early and practicing continuous integration.
Home page
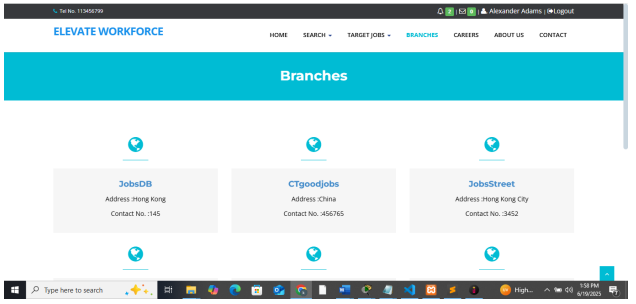
Branches pages
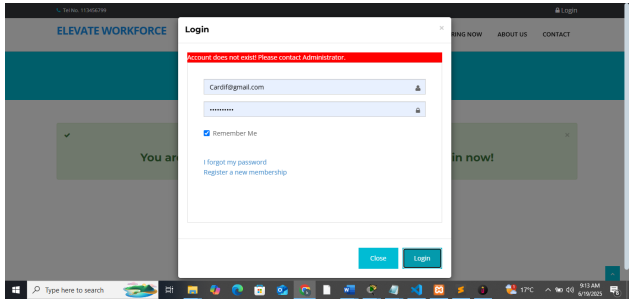
Log in
Successfully log in
1.8 Conclusion
The project is built on a sound technology stack that includes PHP and MySQL and meets the MVC architecture and object-oriented programming standards, which makes it scalable, easy to maintain, and fast(Rustagi and Kumar,2022). Incremental methodology ensures the development in phases and maintaining testing and feedback by the stakeholders, resulting in the increased quality of the outcomes and minimized project risks.
Having well-managed functional and non-functional requirements, the system is supposed to be secure, responsive, and accessible, with features that include registration, job listing, applications, and role-based dashboards. As an online portal, this is not merely a more efficient way of recruiting more people but is also aligned with the mission of Elevate, to empower the workforce digitally. With effective planning, risk management, and fast implementation, the Job Portal establishes an excellent base to add to future changes and future organizational utility(Ricárdez et al.,2024).
References
Abrahams, T.O., Ewuga, S.K., Kaggwa, S., Uwaoma, P.U., Hassan, A.O. and Dawodu, S.O., (2023). Review of strategic alignment: Accounting and cybersecurity for data confidentiality and financial security. World Journal of Advanced Research and Reviews, 20(3), pp.1743-1756.
Zarour, M., Alenezi, M., Ansari, M.T.J., Pandey, A.K., Ahmad, M., Agrawal, A., Kumar, R. and Khan, R.A., (2021). Ensuring data integrity of healthcare information in the era of digital health. Healthcare technology letters, 8(3), pp.66–77.
Rani, S., Kataria, A. & Chauhan, M. (2022). Cyber security techniques, architectures, and design. In Holistic approach to quantum cryptography in cyber security (pp. 41–66). CRC Press.
Jones, K.I. and Suchithra, R., (2023). Information security: A coordinated strategy to guarantee data security in cloud computing. International Journal of Data Informatics and Intelligent Computing, 2(1), pp.11–31.
Carreno, A., (2024). Building a Continuous Feedback Loop for Real-Time Change Adaptation: Best Practices and Tools.
Nazarova, G. and Rudenko, V., (2023). Digital maturity and digital transformation in human resources management: Stability vs development.
Rustagi, P. and Kumar, Y., (2022). MVC architecture and its application.
Wu, D., (2022). The application and management system of scientific research projects based on PHP and MySQL. Journal of Interconnection Networks, 22(Supp02), p.2143043.
Amini, M., Rahmani, A., Abedi, M., Hosseini, M., Amini, M. and Amini, M., (2021). Mahamgostar. Com is a case study for adopting the LaravelLaravel framework as the best programming tool for small and medium enterprises using PHP-based web development. Journal of Innovation & Knowledge, ISSN, pp.100–110.
Wibowo, M.C. and Putra, T.W.A., (2024). Utilizing phpMyAdmin for System Design in Enterprise Administration. Journal of Technology Informatics and Engineering, 3(2), pp.217–234.
Ricárdez, J.J.U., Vasconcelos, M.P., Domínguez, R.G. and Romero, F.C., 2024. Integration of Generative AI with ChatGPT in Software Development.
Omachi, V.O. and Ajewumi, O.E., (2024). The influence of agile organizational design on employee engagement and performance in the digital age. International Journal of Research Publication and Reviews, 5(10), pp.25–39.
Amine, S.M.T., (2021). Developing a web platform for managing wholesalers and their customers.
Al-Badri, I.M.H., Aouragh, A. and AlDelfi, K., (2023). Implementing Vue. Js course on Moodle Platform.
Mohammad El-Basioni, B.M. and Abd El-Kader, S.M., (2024). Designing and modeling an IoT-based software system for land suitability assessment use case. Environmental Monitoring and Assessment, 196(4), p.380.
INTERNATIONAL SCHOOL OF MANAGEMENT AND TECHNOLOGY
NEPAL
FACULTY OF COMPUTING
| UNIT TITLE | Unit 29: Network Security | ||
| UNIT CODE | M/618/7443 | LEVEL | 5 |
| STUDENT NAME | CREDIT VALUE | 15 | |
| ASSESSMENT TITLE | Nobel College Security | WORD COUNT | |
| ASSESSOR | Ankit Shekhar Adhikari | I.V. | |
| ASSIGNMENT ISSUE DATE | April 13, 2025 | ASSIGNMENT SUBMISSION DATE | June 17, 2025 |
| ORIGINAL SUBMISSION | ASSIGNMENT NO. | 1/1 | |
ASSESSMENT CRITERIA TO BE ASSESSED IN THIS ASSIGNMENT
(Identify all criteria to be assessed in this assignment)
| Assignment Criteria | P1 | P2 | P3 | P4 | P5 | P6 | ||||
| Achieved | ||||||||||
| Merit Criteria | Distinction Criteria | |||||||||
| Assignment Criteria | M1 | M2 | M3 | M3 | M4 | D1 | D2 | |||
| Achieved | ||||||||||
Important:
- Read the plagiarism notice and requirements at Page 8
- Word-limit- 8000 words (excludes cover page, table of content, figures, graphs, reference list, appendix and logbook)
- Accepted Sources: Research Papers (Journal Articles, Conference Proceedings, Thesis), Text Books, Governmental Data, Websites (only a registered organization, an educational institution, government agency)
- Information taken from unreliable sources will not be accepted
- Must follow Harvard Reference Style
- Assignment must be submitted through the Plagiarism Detection Tool
| Assignment submission format |
| Each student has to submit their assignment as guided in the assignment brief. The students are guided on what sort of information is to produce to meet the criteria targeted. You are required to make use of headings, paragraphs, and subsections as appropriate, and all work must be supported with research and referenced using the Harvard referencing system. |
| Learning outcomes covered |
| LO1 Examine Network Security principles, protocols and standards LO2 Design a secure network for a corporate environment LO3 Configure Network Security measures for the corporate environment. LO4 Undertake the testing of a network using the test plans. |
| Scenario |
| You have been contracted by a prominent educational institution called “The Nobel College” which serves thousands of students and staff. The Nobel College is known for its cutting-edge research and technology programs. Recently, they have grown concerned about the security of their network infrastructure due to several incidents of unauthorized access to sensitive student data and research projects. Your mission is to conduct a comprehensive network security assessment and propose measures to enhance their network security. |
ASSIGNMENT SCENARIO AND TASKS
| Assignment Task – Part 1 |
| You need to start by examining the different types of Network Security principles, protocols and standards.You need to prepare a short presentation, along with speaker notes that:Discusses the different types of Network Security devices available. Examine network security protocols and the use of different cryptographic types in network security. For a higher grade you could also compare and contrast at least two major Network Security protocols. Further prepare a requirement specification document With reference to the given scenario, investigate and list out the purpose and requirements for a secured Network. Determine and list out the network hardware and software to use in this network. For a higher grade you could Create a design of a secure network according to a given scenario. Evaluate the importance of network security to an organization. |
| Assignment Task – Part 2 |
| Further Configure Network Security measures for the corporate environment. You will have to create an implementation and testing document that contains the implementation details Configure Network Security for your network. You could make your report comprehensive by provide detailed screenshots along with a short explanation of all the steps involved. Provide Network security configuration script/ files and screenshots with detailed comments.Further Carry out a detailed testing and present a test report.Develop and implement a Test Plan for the Network you have designed for The Nobel College and test the Network using the plan you have developed. For a higher grade you could:Provide screenshots/files/ scripts of the testing and analyze the results of testing to recommend improvements for the network.Critically evaluate the design, planning, configuration and testing of the Network designed for The Nobel College |
LEARNING OUTCOMES AND ASSESSMENT CRITERIA
| Pass | Merit | Distinction |
| LO1 Examine Network Security principles, protocols and standards | D1 Evaluate the importance of network security to an organization. | |
| P1 Discuss the different types of Network Security devices. P2 Examine network security protocols and the use of different cryptographic types in network security. | M1 Compare and contrast at least two major Network Security protocols. | |
| LO2 Design a secure network for a corporate environment | ||
| P3 Investigate the purpose and requirements of a secure network according to a given scenario. P4 Determine which network hardware and software to use in this network. | M2 Create a design of a secure network according to a given scenario. | |
| LO3 Configure Network Security measures for the corporate environment | D2 Critically evaluate the design, planning, configuration and testing of the network. | |
| P5 Configure Network Security for your network. | M3 Justify the choices made in the implemented network security configuration. | |
| LO4 Undertake the testing of a network using a Test Plan | ||
| P6 Comprehensively test your network using the devised Test Plan. | M4 Analyze the results of testing to recommend improvements to the network. | |
Plagiarism Notice
You are reminded that there exist Academic Misconduct Policy and Regulation concerning Cheating and Plagiarism.
Extracts from the Policy:
Section 3.4.1: Allowing others to do assignments / Copying others assignment is an offence
Section 3.4.2: Plagiarism, using the views, opinion or insights / paraphrasing of another person’s original phraseology without acknowledgement
Requirements
- It should be the student’s own work – Plagiarism is unacceptable.
- Clarity of expression and structure are important features.
- Your work should be submitted as a well presented, word-processed document with headers and footers, and headings and subheadings.
- You are expected to undertake research on this subject using books from the Library, and resources available on the Internet.
- Any sources of information should be listed as references at the end of your document and these sources should be referenced within the text of your document using Harvard Referencing style
- Your report should be illustrated with screen-prints, images, tables, charts and/or graphics.
- All assignments must be typed in Times New Roman, font size 12, 1.5 spacing.
The center policy is that you must submit your work within due date to achieve “Merit” and “Distinction”. Late submission automatically eliminates your chance of achieving “Merit and Distinction”. Also, 80% attendance is required to validate this assignment.
| Assignment Prepared By Siddhant Bhattarai | Date March 25, 2025 | |
| Brief Checked By Dhruba Babu Joshi | Signature | Date March 27, 2025 |
Assignment Task – Part 1
Different types of network security devices
In the current world of digitization, network security devices are very essential equipment that secures the system and data against any unauthorized access, malware and other forms of cyber threats(Aslan et al.,2023).Such devices work as the initial and in some cases the final defense measure against security breaches to guarantee confidentiality, integrity as well as availability of the information within the infrastructure of any organization. There are many different kinds of network security device and they all perform different provisions, and they all have positive features and negative features(Perwej et al.,2021).
- The firewall.
Firewalls can be viewed as gatekeepers that observes traffic entering and moving out of a network and either enables or blocks data packets according to a set of security policies. They may be hardware, software, or both-based and, in general, they are located at the interface between internal and external networks(Fadziso et al.,2023). One of the great firewall advantages is that they simply implement access control allowing blocking illegitimate users and averting attacks like port scanning or simple intrusion. Most however, traditional firewalls do not have high application-level visibility, and are not able to sense more technologically complicated malware, or insider threats. Modern networks are thus in need of next-generation firewalls (NGFWs), which in addition to deep packet inspection, intrusion prevention, and application awareness features, come at a greater price and complexity(Basholli et al.,2024).
- Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS)
The network security also depends greatly on the Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS). IDS scrutinizes the network traffic for unusual activities and posts alerts in case of suspicious ones, but IPS does the activity one notch forward by obstructing or deterrence the identified menace(Shukla et al.,2022).These systems work exceptionally well at detecting well-known patterns of attack, mandatory logins, and abnormal behaviors via signature-based detection or anomaly-based detection.
Inherent feature of IDS and IPS devices as the primary benefit is that they can recognize the threats, which can penetrate firewall or be caused by inside the system network. Nevertheless, their main weakness is the production of false positives-providing security alerts on non-malicious traffic-thus jamming the security personnel(Ghelani et al.,2022).They can be challenged to identify zero-day attacks whose threat signatures are not current.
- Virtual private network concentrator
The other common device used is known as Virtual Private Network (VPN) concentrator that offers encrypted and secure channels to remote user signing on to the organizational network. The VPN devices will also make data sent through the public networks to be confidential and inaccessible to third parties(Jimmy,2024).
This is particularly critical in the case of organizations such as universities whose distance employees and learners frequently access education and business systems. The high level of encryption and authentication that is provided by VPN devices is their main strength since it improves privacy and the data security(Erondu and Erondu,2023).VPNs also have their disadvantages, performance bottlenecks, particularly with large numbers of simultaneous users, and possible bypass of a multifactor authentication in the event of stolen credential use.
- Network Access Control (NAC)
NAC systems allow configuring security policies on devices that want to access the network. Such devices verify that adherence is met such as updated antivirus software, or operating system patches, before granting the devices access(Mallick and Nath,2024). The NAC has found its application in Bring Your Own Device (BYOD) settings such as colleges and universities where a wide range of personal devices might want to connect to institutional networks. NAC has the advantage of proactive type of defense: the network does not allow potentially vulnerable or infected machines to connect to the network(Mpamugo and Ansa,2024). But NAC may be difficult to set up and maintain, especially on large infrastructures, and can even cause latency or connectivity-problems when incorrectly configured.
- Unified Threat Management (UTM)
Appliance and these include firewall, antivirus, content filtering, intrusion prevention, and others. UTMs provide a package deal that makes it easy to control security of the smaller companies that have few IT personnel. The primary benefit of the latter is simplicity of installment and affordability as they eliminate the necessity of having separate gadgets(Kamruzzaman. One of the weakness is that,UMT when subject subjected to massive traffic as dedicated devices can perform, and a breakdown in the UTM can take away all possible network defenses against a variety of malicious traffic at once, and therefore, create one point of failure(Cochran,2024).
- Anti-virus and endpoint protection systems.
To ensure protection of the user devices against malware, ransomware and phishing attacks, it is very necessary to have antivirus and endpoint protection systems. Such system scans and identifies harmful software and removes them either in real-time or the scheduled scans(Solanki et al.,2024). They are used not only on desktops but their use further extends to mobile solutions as well as servers and even to IoT devices.
The most important advantage of endpoint protection is that it serves as protection of the last resort in cases where the perimeter has been bypassed(Kadhim,2024). The traditional antiviruses, however, are based on known signatures and may not be too helpful when more modern and polymorphic threats are being met unless additional behavioral analysis or machine learning mechanisms have been added.
Every device such as firewall, IDS/IPS, VPN, NAC, UTM and endpoint protection device serves a different purpose in the layered security design. They will only be as effective as they are configured, maintained and integrated into a larger security system(Arfeen et al.,2021). Although none of these devices is a perfect solution and is enough to guarantee protection, a combination of such tools depending on the size of the organization, the type of risk, and the operations requirement is an effective defense against the threats as they develop in the environment.
Network security protocols and the use of different cryptographic types in network security.
Network security protocols refer to rules and norms which oversee safe correspondence in the digital networks. The protocols play a crucial role in ensuring the confidentiality, integrity and authenticity of the data as it moves between systems, especially on un-trusted mediums such as the internet(Kizza,2024). Therefore, to ensure these parameters are met, network security processes use a diverse set of cryptographic solutions, among them symmetric encryption, asymmetric encryption, hashing and digital signatures(Arogundade, 2023). These cryptographic tools are used together to actually enable them to protect sensitive information, authenticate both the users and systems, and also to ensure that the communications cannot be tampered with by an evil user or hacker(Shwedeh et al.,2023).
- Transport Layer security
Transport Layer Security (TLS) is one of the most popular network security protocols that has effectively replaced an older protocol Secure Socket Layer (SSL)( Ambedkar,2025). TLS is mostly applied to encrypt web traffic, email, instant messaging and voice-over-IP (VoIP) communications. When a user visits a web site that starts with the prefix of https, the TLS protocol is in effect to encrypt the information being relayed between the browsers of the user and the web site server(Kumar et al.,2024). The main advantage of TLS is that leverages symmetric and asymmetric cryptography.
The initial state of a TLS connection involves secure exchange of a symmetric key through means of asymmetric encryption. After exchange of keys, the communication becomes symmetric and hence faster and more efficient in the continued communication(Sahu,2024). Message authentication codes (MACs) are also employed by TLS, to authenticate data integrity properties, that is, to ensure that the data has not been modified in transit.
- Internet protocol security
The other security protocol in network security crucial is the IPSec (Internet protocol Security). IPSec provides encryption and authentication services on network layer through encrypting IP packets(Bozkurt et al.,2023). It is also used effectively in the configuration of safe VPN tunnels, including remote access to a secure corporate or institutional network. IPSec has the capability of operating in transport mode and tunnel mode with the transport mode only encrypting data section of the packet whereas tunnel mode will encrypt the entire data packet together with the IP header and encapsulate the packet into a new one(Sharp,2023).
IPSec like TLS uses symmetric and asymmetric cryptography. It adopts protocols such as Internet Key Exchange (IKE) to conduct key exchange securely and offers robust encryption through algorithms coping with huge encryption and exchanges such as AES(Ali, 2021). Among the benefits of IPSec, is the fact that the latter is capable of securing all applications on the network in a transparent way. Nevertheless, it is more cumbersome to set-up and deal with compared to application layer protocols such as TLS.
- Secure Shell
Secure Shell (SSH) is required to administer a remote machine and transmitting files in an insecure network. By encrypting passwords and commands; SSH substitutes older and insecure techniques such as Telnet as it encrypts all information sent between the client and server(Mishra et al.,2024). SSH employs the asymmetric algorithm of exchanging keys and symmetric algorithm during the session.
It also integrates hashing as a way of message integrity. System administrators extensively use SSH to securely access distant servers and its main power is its simplicity, portability and security(Easttom,2022). Nevertheless, it becomes prone when poor credentials are utilized, or non-secure storage of the private keys.
- Hypertext Transfer Protocol Secure (HTTPS)
HTTPS is basically HTTP on top of TLS. It is the guideline of safe web surfing. In HTTPS, not solely is the information relayed between the browser and the web server encrypted, but the identity of the server is verified by the use of digital certificates provided by trusted Certificate Authorities (CAs)(Hu et al.,2021).
This offers secrecy as well as authentication that protects users against the man-in-the-middle attack. It has become a mandatory part of e-commerce, banking, and any site that carries sensitive data of a user. A weakness is that improper certificate handling expired / self signed certificates, might give an illusion of security and expose the user to be compromised(de Carné de Carnavalet and van Oorschot,2023).
- Wireless security protocols
Wired security protocols, including WPA2 and WPA3 (Wi-Fi Protected Access), play a vital role in ensuring security of wireless networks against unauthorized access, as well as eavesdropping(Halbouni and Leow,2023). These protocols encompass symmetric encryption- usually the AES algorithm- as a method of securing data transmitted by Wi-Fi.
The most recent standard, WPA3, adds forward secrecy and offline dictionary protection. Nevertheless, some weaknesses continue to prevail where users are using weak passwords or do not update the firmware regularly making the access points prone to exploit(Adbeib,2023).
Cryptography.
The foundation of these protocols is cryptography and therefore it is beneficial to know the kinds of cryptographic methods involved to enhance the appreciation of their functions in network security. Symmetric encryption employs one secret key to encrypt or decrypt a data. It is high in terms of efficiency and speed and it is therefore good in securing large data volumes during activities(Sarkar et al.,2021). Symmetric algorithms are represented by such examples as AES and DES, but nowadays, AES is considered to be the modern standard because of its strength and efficiency. Se curately transmitting the secret key, particularly via an insecure system, is also the main liability of symmetric encryption (Geetha et al.,2023).
Asymmetric encryption employs two keys encryption and the decryption keys. This scheme is an initial stage of secure conversation such as TLS handshake or SSH connections. The problem with the distribution of keys can be overcome with the method of asymmetric encryption, (asymmetric encryption; RSA and ECC (Elliptic Curve Cryptography)( Dowling et al.,2021).It is however computationally slower compared to symmetric encryption and cannot be applied when encrypting a large amount of information.
The data integrity is assured through the utilization of hashing algorithms such SHA-2, SHA-3. They turn any input to a fixed length string (hash) and a slight alteration in the input will cause an entirely different hash(Hazra et al.,2024).Hashes Digital signatures, file integrity checks and passwords in digital signatures, file integrity checks, and password storage, hashes are typically used. Although hashing is not a reversible process and works without keys, it plays a very significant role in verifying the authenticity of the data that is sent(Banoth and Regar,2023).
Digital signatures are a combination of hashing and asymmetric encryption that gives the integrity and authenticity of the messages.A message sender is able to hash the message and then encrypt the hashed value using his or her secret key(Lalem et al.,2023).A recipient is able to decrypt the cipher using the sending parties public key and can compare it with the hash that he or she calculates. This assures the authenticity of the sender as well as the safety of the message(Chamo,2025).
The topics of network security measures and cryptographic algorithms are tightly connected in the security of current communications. Secure and authenticated and tamper-proof information transmissions using protocols such as TLS, IPSec, SSH, and HTTPS rely on various combinations of encryption and hashing and digital signatures(Shankar et al.,2023).
Both protocols and types of cryptography have their own advantages and limitations and as a combination they increase the defenses against the extremely wide territory of cyber threats, and, thus, is a layered and redundant system(Salih et al.,2024).
Compare and contrast at least two major Network Security protocols.
| Aspect | TLS (Transport Layer Security) | IPSec (Internet Protocol Security) |
| Layer of Operation | Operates at the Application Layer (Layer 7) | Operates at the Network Layer (Layer 3) |
| Primary Use Cases | Securing web traffic (HTTPS), email (SMTPS), VoIP, instant messaging | VPNs, secure IP communications, remote access over untrusted networks |
| Encryption Scope | Encrypts application-level data (e.g., user credentials, web content) | Encrypts entire IP packets (data and headers) in tunnel mode |
| Key Management | Uses public key cryptography during the TLS handshake (RSA, ECC) | Uses Internet Key Exchange (IKE/IKEv2) for key exchange and authentication |
| Authentication Method | Server authentication via digital certificates; optional client authentication | Mutual authentication using pre-shared keys, certificates, or Kerberos |
| Encryption Algorithms | AES, ChaCha20, RC4 (deprecated); used with GCM, CBC, etc. | AES, 3DES, Blowfish, combined with ESP/AH headers |
| Performance | Faster for short-lived, application-level sessions; minimal overhead | Adds more overhead due to full-packet encryption; better for site-to-site VPNs |
| Flexibility and Deployment | Easily deployable in browsers and mobile apps | Requires more complex configuration and support at routers or firewalls |
| Granularity of Security | Provides end-to-end encryption between specific applications | Provides network-wide encryption regardless of applications |
| Protocol Components | TLS Record Protocol, Handshake Protocol, Alert Protocol | AH (Authentication Header), ESP (Encapsulating Security Payload) |
| Data Integrity Checks | MAC (Message Authentication Code) included in encrypted sessions | Integrity ensured via AH or ESP with authentication option |
| Typical Use in Institutions | Used by websites, online portals, and cloud applications | Used by universities or companies for remote access VPNs and secure branch connections |
| NAT (Network Address Translation) Compatibility | TLS is NAT-friendly and works well with firewalls | IPSec (especially AH) has NAT issues, although NAT-T (Traversal) addresses this |
| Visibility to Middle Devices | Encrypted payload is only visible to endpoints | Can obscure routing details due to full-packet encryption |
| Resilience Against Attacks | Strong against MITM, eavesdropping, downgrade attacks (if properly configured) | Strong against IP spoofing, replay attacks, and packet sniffing |
| Deployment Example | A student accessing Nobel College’s secure learning portal via HTTPS | A Nobel College staff connecting securely to the university network via VPN |
Evaluate the importance of network security to an organization.
Network security is extremely essential as it protects the integrity of data in the organization, availability of data and confidentiality of data. Organizations are now dependent on networked environments in the current digital age to facilitate communication and store sensitive information as well as manage organization operations (Yee and Zolkipli,2021).
In the absence of proper security, it is very easy to hack these networks and the hacking may be in form of data breach, ransom wares, phishing and unauthorized access. The Nobel College that deal with student records, research data and administrative systems, a breach has the potential of causing great financial loss, legal implications, detrimental effects on reputation, and service disruption.
Proper network security can help undertake data and IP theft and data manipulation since they are accessed through authorized users. It facilitates the continuation of businesses by ensuring that the critical infrastructures are not brought down by business downtime or cyber-attacks(Zarour et al.,2023). It can also assist organizations in satisfying the regulatory and compliance measures in the form of GDPR, HIPAA, or FERPA depending on the industry.
The attack surface has been extended due to the increasing culture of remote work and BYOD (Bring Your Own Device), and, as a result, the need to maintain a high level of network security is not merely a technical requirement but a dictate of strategy(Abrahams et al.,2023).Investing in network security that the stakeholders get to develop trust, stability in the operations, and the long-term survival of the organization in this ever-hostile cyber environment.
Assignment Task – Part 2
Design a secure network for a corporate environment
Secure network allows the security of online facilities, privacy, accountability, data integrity, and safe communication in an organization. The Nobel College, a school with thousands of students and employees that is famous due to its technology and research courses, this accession to safe network can hardly be overemphasized(Rani et al.,2022).The college experienced cases of unauthorized access to sensitive student data/research contents, there is increased need to have the college come up with secure network infrastructure that is not only academically appropriate but also on administration requirements.
The main intention of a secure network in The Nobel College is to secure the confidential information of students i.e. their record, academic records, research, financial and internal communication. A safe network means that only authorized people can access the relevant resources in the network and as a result avoiding data attacks and unauthorized manipulations (Jones and Suchithra,2023).
The other major objective is to establish secure and dependable online interface of research facilities, online learning services, online libraries, and administrative systems. Also, remote access to the network should be provided to staff, students, and researchers safely, particularly in the age of hybrid and distance learning(Ali et al.,2021).
To meet these objectives, a secure network for the college must fulfill several key requirements:
- Access Control – User authentication within the network should be made strong i.e. multi-factor authentication (MFA), role-based access control (RBAC) and user-based account provisioning (students, faculty and admin)( Venugopal et al.,2023).Access to certain systems and data must be authorized to authentic users.
- Data Encryption– The information being sent and the data that is not being sent should be encrypted using powerful encryption algorithms such as AES-256.The user and system communications, such as email, web portal along with cloud platform must be secured with protocols such as TLS(Basholli et al.,2023).
- Perimeter security Firewalls: Intrusion Prevention: Firewalls are essential. Firewalls in form of hard wares and soft wares must be installed to counter incoming and outgoing traffic. Real-time detection and prevention of suspicious activities should be installed, i.e., Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS).
- Segmentation and Isolation: segments within the network must be segmented (e.g., research labs, student network, staff network) into VLANs or subnetting. This restricts proliferation of attacks and specifies compartmentalization of sensitive resources(Admass et al.,2024).
- Endpoint Security– All of the connected devices such as laptops, desktops, mobile devices, and servers should be secure against invasions with up to date antivirus software, patch management, and host-based firewalls.
- Secure Remote Access- As more learning and administration is required to be done remotely, the network must be able to support VPNs that allow encrypted tunnels connecting to the network behind authentication.
- Monitoring and Logging: An integrated logging and SIEM (Security Information and Event Management) system should be used to conduct ongoing monitoring to warrant early threat detection, compliance and auditing.
- Policy Enforcement (IT security) college policy should exist in some of the issues where it should be the acceptable use of IT, password policy, information handling and incident response policy.
- User Awareness and Training – On a larger scale, the issue of security should not be seen as exclusively technical, but users should also be trained about the concept of phishing, social engineering and best online practices.
Hardware and software requirements.
Network Hardware:
- Next Generation Firewalls (NGFWs): Next-Generation Firewalls (such as Fortinet or Cisco Firepower) can be installed at the network perimeter, which allows controlling network traffic and security policies.
- Managed switches and routers: Cisco or HP enterprise level, switches and routers allows VLAN separation, quality of service (QoS), and the ability to support access control lists (ACLs).
- Wireless Access Points (WAPs): use secure wireless access points such as Ubiquiti or Aruba, which support WPA3 encryption and centralized Wi-Fi access over the campus.
- VPN Gateways: The remote access devises, such as Palo Alto GlobalProtect or Cisco AnyConnect, enable the remote access to both students and staff in a secure way.
- Network Servers: These can be authentication servers (i.e RADIUS), DNS servers and DHCP servers, which support redundancy and failover.
Network Software:
- Antivirus and Endpoint security: Antivirus systems such as Sophos or Bitdefender prevent the devices against malware and threats.
- Network Monitoring Tools: Network monitoring tools such as SolarWinds or PRTG enable an organization to analyses traffic in real time and alert it.
- SIEM Solutions: There are programs such as Splunk or IBM QRadar which allow us to correlate the logs, detect incidents and respond to them.
- Identity and Access Management (IAM): Microsoft Active Directory as well as Group Policy to secure access and authenticate access to users.
Design of a secure network
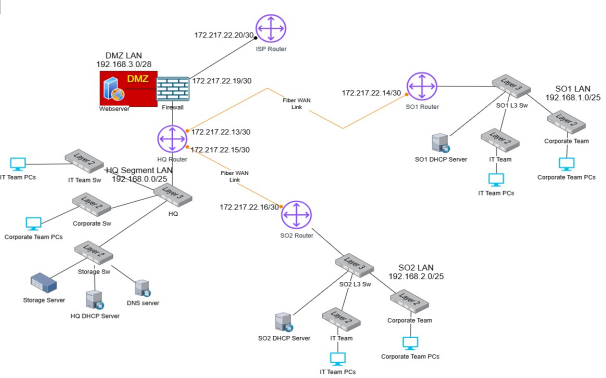
Configure Network Security measures for the corporate environment
IP addressing for your topology.
| Location / Device | Network/Subnet | Subnet Mask | Gateway |
| HQ | 192.168.0.0/25 | 255.255.255.128 | 192.168.0.1 |
| SO1 | 192.168.1.0/25 | 255.255.255.128 | 192.168.1.1 |
| SO2 | 192.168.2.0/25 | 255.255.255.128 | 192.168.2.1 |
| DMZ (Web Server) | 192.168.3.0/28 | 255.255.255.240 | 192.168.3.1 |
| Cloud LAN (ISPs) | 10.0.0.0/28 (per link) | 255.255.255.240 | Depends on config |
| WWW Server | 200.200.200.1/24 | 255.255.255.0 | N/A |
| PC | 210.210.210.1/24 | 255.255.255.0 | N/A |
DMZ (Web Server)
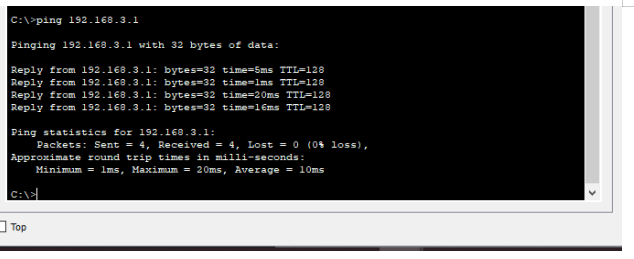
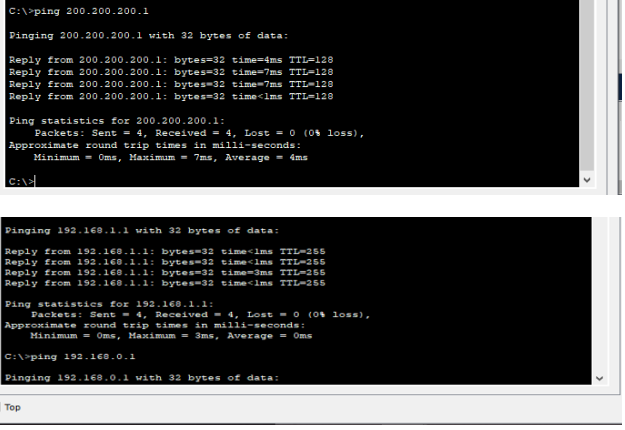
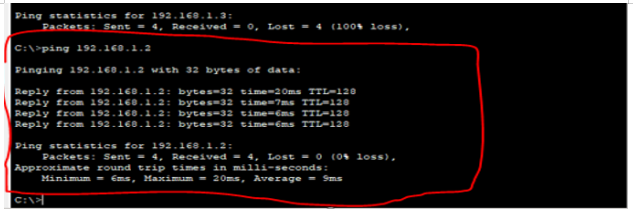
Testing the connecting of the server
To ping the www server
References
Aslan, Ö., Aktuğ, S.S., Ozkan-Okay, M., Yilmaz, A.A. and Akin, E., 2023. A comprehensive review of cyber security vulnerabilities, threats, attacks, and solutions. Electronics, 12(6), p.1333.
Perwej, Y., Abbas, S.Q., Dixit, J.P., Akhtar, N. and Jaiswal, A.K., 2021. A systematic literature review on the cyber security. International Journal of scientific research and management, 9(12), pp.669-710.
Fadziso, T., Thaduri, U.R., Dekkati, S., Ballamudi, V.K.R. and Desamsetti, H., 2023. Evolution of the cyber security threat: an overview of the scale of cyber threat. Digitalization & Sustainability Review, 3(1), pp.1-12.
Basholli, F., Juraev, D.A. and Egamberdiev, K., 2024. Framework, tools and challenges in cyber security. Karshi Multidisciplinary International Scientific Journal, 1(1).
Shukla, S., George, J.P., Tiwari, K. and Kureethara, J.V., 2022. Data security. In Data ethics and challenges (pp. 41-59). Singapore: Springer Singapore.
Ghelani, D., Hua, T.K. and Koduru, S.K.R., 2022. Cyber security threats, vulnerabilities, and security solutions models in banking. Authorea Preprints.
Jimmy, F.N.U., 2024. Cyber security vulnerabilities and remediation through cloud security tools. Journal of Artificial Intelligence General science (JAIGS) ISSN: 3006-4023, 2(1), pp.129-171.
Erondu, C.I. and Erondu, U.I., 2023. The Role of Cyber security in a Digitalizing Economy: A Development Perspective. International Journal of Research and Innovation in Social Science, 7(11), pp.1558-1570.
Mallick, M.A.I. and Nath, R., 2024. Navigating the cyber security landscape: A comprehensive review of cyber-attacks, emerging trends, and recent developments. World Scientific News, 190(1), pp.1-69.
Mpamugo, E. and Ansa, G., 2024. Enhancing Network Security in Mobile Applications with Role-Based Access Control. Journal of Information Systems and Informatics, 6(3), pp.1872-1899.
Kamruzzaman, A., Ismat, S., Brickley, J.C., Liu, A. and Thakur, K., 2022, December. A comprehensive review of endpoint security: Threats and defenses. In 2022 International Conference on Cyber Warfare and Security (ICCWS) (pp. 1-7). IEEE.
Cochran, K.A., 2024. Network Security: Safeguarding Digital Pathways. In Cybersecurity Essentials: Practical Tools for Today’s Digital Defenders (pp. 215-247). Berkeley, CA: Apress.
Solanki, P.S., Singh, A., Sao, S. and Atkekar, N.D., 2024. Protection of Research Data and Devices from Malware Attacks Using Endpoint Security System in Network. International Journal of Scientific Research in Network Security and Communication, 12(3), pp.15-18.
Kadhim, V.K., 2024. TECHNIQUES TO PROTECT AGAINST CYBER ATTACKS. The American Journal of Engineering and Technology, 6(07), pp.81-93.
Arfeen, A., Ahmed, S., Khan, M.A. and Jafri, S.F.A., 2021, November. Endpoint detection & response: A malware identification solution. In 2021 international conference on cyber warfare and security (ICCWS) (pp. 1-8). IEEE.
Kizza, J.M., 2024. Computer network security protocols. In Guide to Computer Network Security (pp. 409-441). Cham: Springer International Publishing.
Arogundade, O.R., 2023. Network security concepts, dangers, and defense best practical. Computer Engineering and Intelligent Systems, 14(2).
Shwedeh, F., Malaka, S. and Rwashdeh, B., 2023. The Moderation Effect of Artificial Intelligent Hackers on the Relationship between Cyber Security Conducts and the Sustainability of Software Protection: A Comprehensive Review. Migration Letters, 20(S9), pp.1066-1072.
Ambedkar, B.R., 2025. Efficient Exploration of Secure Socket Layer at Transport Layer Security. Knowledgeable Research: A Multidisciplinary Peer-Reviewd Refereed Journal, 3(06), pp.1-6.
Kumar, D.D., Mukharzee, J.D., Reddy, C.V.D. and Rajagopal, S.M., 2024, March. Safe and secure communication using SSL/TLS. In 2024 International Conference on Emerging Smart Computing and Informatics (ESCI) (pp. 1-6). IEEE.
Sahu, S.K., 2024. Protocol Security. In Building Secure PHP Applications: A Comprehensive Guide to Protecting Your Web Applications from Threats (pp. 315-346). Berkeley, CA: Apress.
Bozkurt, F., Kara, M., Aydın, M.A. and Balik, H.H., 2023, September. Exploring the vulnerabilities and countermeasures of SSL/TLS protocols in secure data transmission over computer networks. In 2023 IEEE 12th International Conference on Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications (IDAACS) (Vol. 1, pp. 400-407). IEEE.
Ali, I., 2021. Examining cyber security implementation through TLS/SSL on academic institutional repository in Indonesia. Berkala Ilmu Perpustakaan dan Informasi, 17(2), pp.238-249.
Sharp, R., 2023. Network Security. In Introduction to Cybersecurity: A Multidisciplinary Challenge (pp. 171-233). Cham: Springer Nature Switzerland.
Mishra, A., Sahoo, G.S., Sekaran, R., Umamaheswari, B., Futane, P.R. and Choudhary, S., 2024, June. Exploring the Potential of Secure Shell (SSH) as a Wireless Network Security Tool. In 2024 15th International Conference on Computing Communication and Networking Technologies (ICCCNT) (pp. 1-7). IEEE.
Easttom, C., 2022. Virtual private networks, authentication, and wireless security. In Modern Cryptography: Applied Mathematics for Encryption and Information Security (pp. 309-327). Cham: Springer International Publishing.
Hu, Q., Asghar, M.R. and Brownlee, N., 2021. A large-scale analysis of HTTPS deployments: Challenges, solutions, and recommendations. Journal of Computer Security, 29(1), pp.25-50.
de Carné de Carnavalet, X. and van Oorschot, P.C., 2023. A Survey and Analysis of TLS Interception Mechanisms and Motivations: Exploring how end-to-end TLS is made “end-to-me” for web traffic. ACM Computing Surveys, 55(13s), pp.1-40.
Halbouni, A., Ong, L.Y. and Leow, M.C., 2023. Wireless security protocols wpa3: A systematic literature review. IEEE Access, 11, pp.112438-112450.
Adbeib, K.A., 2023. Comprehensive study on wi-fi security protocols by analyzing wep, wpa, and wpa2. African Journal of Advanced Pure and Applied Sciences (AJAPAS), pp.385-402.
Sarkar, A., Chatterjee, S.R. and Chakraborty, M., 2021. Role of cryptography in network security. The” essence” of network security: an end-to-end panorama, pp.103-143.
Geetha, V., Singh, P., Patil, N.S. and Reddy, S.S.S., 2023. Introduction To Cryptography And Network Security. AG PUBLISHING HOUSE (AGPH Books).
Dowling, B., Fischlin, M., Günther, F. and Stebila, D., 2021. A cryptographic analysis of the TLS 1.3 handshake protocol. Journal of Cryptology, 34(4), p.37.
Hazra, R., Chatterjee, P., Singh, Y., Podder, G. and Das, T., 2024. Data Encryption and Secure Communication Protocols. In Strategies for E-Commerce Data Security: Cloud, Blockchain, AI, and Machine Learning (pp. 546-570). IGI Global.
Banoth, R. and Regar, R., 2023. Asymmetric Key Cryptography. In Classical and Modern Cryptography for Beginners (pp. 109-165). Cham: Springer Nature Switzerland.
Lalem, F., Laouid, A., Kara, M., Al-Khalidi, M. and Eleyan, A., 2023. A novel digital signature scheme for advanced asymmetric encryption techniques. Applied Sciences, 13(8), p.5172.
Chamo, Y.Y., 2025. Enhancing Symmetric Encryption Using Digital Signatures. University of Ibadan Journal of Science and Logics in ICT Research, 13(1), pp.179-187.
Salih, S.Q., Sekhar, R., Tawfeq, J.F., Ibrahim, A., Shah, P. and Radhi, A.D., 2024. Integrated Digital Signature Based Watermarking Technology for Securing Online Electronic Documents. Fusion: Practice and Applications, 14(1), pp.120-128.
Shankar, G., Ai-Farhani, L.H., Anitha Christy Angelin, P., Singh, P., Alqahtani, A., Singh, A., Kaur, G. and Samori, I.A., 2023. Improved multisignature scheme for authenticity of digital document in digital forensics using edward‐curve digital signature algorithm. Security and Communication Networks, 2023(1), p.2093407.
Yee, C.K. and Zolkipli, M.F., 2021. Review on confidentiality, integrity and availability in information security. Journal of ICT in Education, 8(2), pp.34-42.
Kim, L., 2022. Cybersecurity: Ensuring confidentiality, integrity, and availability of information. In Nursing Informatics: A Health Informatics, Interprofessional and Global Perspective (pp. 391-410). Cham: Springer International Publishing.
Abrahams, T.O., Ewuga, S.K., Kaggwa, S., Uwaoma, P.U., Hassan, A.O. and Dawodu, S.O., 2023. Review of strategic alignment: Accounting and cybersecurity for data confidentiality and financial security. World Journal of Advanced Research and Reviews, 20(3), pp.1743-1756.
Zarour, M., Alenezi, M., Ansari, M.T.J., Pandey, A.K., Ahmad, M., Agrawal, A., Kumar, R. and Khan, R.A., 2021. Ensuring data integrity of healthcare information in the era of digital health. Healthcare technology letters, 8(3), pp.66-77.
Rani, S., Kataria, A. and Chauhan, M., 2022. Cyber security techniques, architectures, and design. In Holistic approach to quantum cryptography in cyber security (pp. 41-66). CRC Press.
Jones, K.I. and Suchithra, R., 2023. Information security: A coordinated strategy to guarantee data security in cloud computing. International Journal of Data Informatics and Intelligent Computing, 2(1), pp.11-31.
Ali, B., Gregory, M.A. and Li, S., 2021. Multi-access edge computing architecture, data security and privacy: A review. Ieee Access, 9, pp.18706-18721.
Venugopal, L.K., Rajaganapathi, R., Birjepatil, A., Raja, S.E. and Subramaniam, G., 2023. A novel information security framework for securing big data in healthcare environment using blockchain. Engineering Proceedings, 59(1), p.107.
Basholli, F., Mezini, R. and Basholli, A., 2023. Security in the components of information systems. Advanced Engineering Days (AED), 7, pp.185-187.
Admass, W.S., Munaye, Y.Y. and Diro, A.A., 2024. Cyber security: State of the art, challenges and future directions. Cyber Security and Applications, 2, p.100031.
