Slide 1:
Introduction
This complete presentation is going to highlight the details on the development of IoT infrastructure for a smart home.
The devices of IoT in smart homes provide excellent comfort but also create some security perturbations, unauthorized access, and data breaches.
The project aims to develop a customized security framework for IoT for use in smart homes.
Encryption protocols, secure authentication, and intrusion detection are significant measures.
The main goal of the project is to protect user data, ensure reliable smart home operations, and build confidence in IoT technologies.
Notes:
IoT devices have been almost practically used within smart homes and have made daily living convenient and state of the art in the various automation taking place within the area. However, such significant advancements have also provided a list of security challenges within the devices, including unauthorized access, data leakages, and possible manipulations from malicious parties. With this in mind, the study shall develop a robust smart home IoT setup security framework. Security features will be integrated under this framework through encryption protocols, secure authentication systems, and intrusion detection. Such security measures will protect users’ data, ensure smart home systems remain dependable, and generate confidence in such developing systems.
Slide 2:
Overview of project
This complete project is based on the below-listed objectives and scenarios.
Design a robust security framework for the IoT devices of smart homes.
Address security vulnerabilities with a multi-layered approach.
Implement advanced encryption, Secure authentication, and machine learning-based intrusion detection.
Increase the trust of the end-users by ensuring the security and privacy of data.
Comply with data protection regulations.
Reduces financial risks derived from cyber-attacks.
Ensure seamless interoperability with various devices brainstormed under the IoT ecosystem and also ensure cross-platform compatibility.
Notes:
The intent of the following project is to develop a strong and reliable security framework for IoT devices in smart homes. This comes third to giving focus to that some of the most important security issues in these interrelated systems. The framework that will be based on advanced encryption, secure authentication, and intrusion detection by machine learning in order to provide drastically improved security. Key objectives that to achieved include building user trust through proper privacy of their data, compliance with laws on data protection, and that financial risk reduction from unauthorized cyber-attacks. The system will be designed in a way that allows easy integration with the various IoT devices from that different manufacturers to ensure compatibility and operations across different platforms.
Slide 3:
Architectural Diagram
Key Components and Security Framework
Core Connectivity and Communication: The central hub which is provided in the figure, that represented as the router, serves that are provided to connect to the different smart home components, that helps to achieving easy and seamless communication and data circulation in the network.
Security Layers: This is the top layer of encryption that is used to secure the transmission of data. That will be between devices using protocols such as AES-256, that helps to make sure that the integrity of the data is monitored by thermostats or motion detectors.
Authentication Mechanisms: In the front door and alarm system, multi-factor authentication is applied as a security means to prevent unauthorized access in different devices.
Intrusion Detection Machine-learning-based IDSs monitor activities learned from devices, like garage doors and carbon monoxide detectors, to identify and take action on current anomalies.
Speaker Notes
Fig. 1 presents the architecture diagram of smart home IoT focusing on security. It can be seen from the diagram that the router takes the shape of a center point that interconnects the primary entities like the thermostat, the detectors of motion, and the garage doors so that they can communicate with one another. Security, in this system, is realized through various layers. There is, first of all, the issue of secure transmission that is achieved through the use of appropriate encryption protocols, such as the AES-256, that assures that intercepted data will not be readily understood. Then there is the multi-factor authentication that works because only genuine devices can access services- a second significant layer of defense for access control against malicious parties. Therefore, advanced intrusion detection systems avail themselves of machine learning to monitor and respond to suspicious activity to provide a proactive stance on security against potential threats.
Slide 4:
Changes In the Initial Project Plan
Changes In the Initial Project Plan
Consequently, the Project Team has realized the need for more robust testing and validation phases.
At this moment, this realization has resulted in a revision of the initial project plan, where more time and resources will be allocated for extensive testing, including functional and non-functional testing scenarios.
Recognizing the importance of regular security audits and compliance checks so that the framework remains up to date concerning the latest regulations and industry best practices, periodic security audits and compliance reviews have now been made part of ongoing maintenance and support activities within the project plan.
Speaker Notes
The outcome of the review process was mammoth changes in making the security framework solid and infallible. Project teams realized that testing and validation phases need to be developed in total, which wasn’t made part of the initial project plan. Hence, the same has been revamped to include more time and resources for testing functional and non-functional scenarios. It was also realized that regular security audits and compliance checks are essential so that the framework aligns with the latest regulations and Industry best practices. Periodic security audits and compliance reviews have been included within the regular maintenance and support activities in the project plan to ensure continued alignment with data protection laws and standards.
Slide 5:
Future Work
Some of the key areas in which researchers can focus to enhance security features in IoT are listed below.
In this regard, it describes blockchain security solutions to enhance the decentralized trust and data integrity of IoT networks.
Development of the encryption algorithms that would be resistant to attacks by future quantum computers
The development and extension of security frameworks on industrial IoT, smart cities, and other developing areas of IoT.
Researching advanced machine learning methods for better intrusion detection and threat mitigation on a regular basis.
Working with regulatory agencies to remain updated on the changing data protection laws and compliance requirements.
Implement privacy-preserving technologies, for example, homomorphic encryption, so that data can be processed securely but confidentially.
Notes:
Future projects can involve blockchain security to achieve the trust and integrity of data in IoT networks. That is the creation of quantum-resistant encryption algorithms, security framework extension to industrial IoT and intelligent cities, advanced machine learning for intrusion detection, and lastly, liaise with regulatory agencies to ensure they are abreast of all you have put in place on data set protection laws. It shall, in turn, apply the use of privacy-preserving technology. Also, use of homomorphic encryption allows data to be processed securely and confidentially.
Slide 6:
Conclusion
This complete presentation has provided a detailed discussion of how a well-maintained and secure infrastructure for IoT smart homes can be developed.
Where the presentation has highlighted that:
It is crucial to have a well-set framework for security in IoT devices of a smart home.
So, the project uses multi-tiered protection: encryption, authentication, and intrusion detection.
The presentation has focused on increasing trust on the part of users, to comply with regulations, and to decrease financial risks.
Continuous monitoring, collaboration with stakeholders, and adapting to new technologies are key.
The project aims at harnessing the potential offered by IoT while keeping a close eye on security, privacy, and reliability.
Notes:
To sum up this whole assessment it can be said that the assignment provides complete details on a multi-layered approach to developing the comprehensive security framework of smart home IoT devices that comes in handy in these fast-changing cyber threats. This project’s encryption, authentication, and intrusion detection are therefore set to help solve the complex security issue associated with the IoT ecosystem. The proposed framework highlights users by building adequate data protection, absolute regulatory compliance, and reduced financial risk, hence encouraging massive adoption of smart home technologies. But to remain effective at staving off cyber threats when those very threats are evolving, it will require ongoing vigilance, stakeholder collaboration, and rapid adaptation of new technologies to do so. This project is a crucial component of a much-needed journey to fully realize the IoT’s potential, with security, privacy, and reliability as fundamental parts of the foundation of that potential.
Slide: Bibliography
Allifah, N. M., & Zualkernan, I. A. (2022). Ranking security of IoT-based smart home consumer devices. Ieee Access, 10, 18352-18369.https://ieeexplore.ieee.org/iel7/6287639/6514899/09698229.pdf
Alshboul, Y., Bsoul, A. A. R., Al Zamil, M., & Samarah, S. (2021). Cybersecurity of smart home systems: Sensor identity protection. Journal of Network and Systems Management, 29(3), 22.https://www.researchgate.net/profile/Abed-Al-Raoof-Bsoul/publication/349804291_Cybersecurity_of_Smart_Home_Systems_Sensor_Identity_Protection/links/627591ab2f9ccf58eb32f241/Cybersecurity-of-Smart-Home-Systems-Sensor-Identity-Protection.pdf
Devi, R. S., & Kumar, M. M. (2020, June). Testing for security weakness of web applications using ethical hacking. In 2020 4th International Conference on Trends in Electronics and Informatics (ICOEI)(48184) (pp. 354-361). IEEE. https://www.researchgate.net/profile/Mohankumar-Kumar/publication/343038606_Testing_for_Security_Weakness_of_Web_Applications_using_Ethical_Hacking/links/6142e138dabc4638f12b88b2/Testing-for-Security-Weakness-of-Web-Applications-using-Ethical-Hacking.pdf
Overview
Purpose
The primary focus for the purpose of the Smart home IOT security project is to comprehensively develop a strong and effective security framework especially in order to address the vulnerabilities and threats associated with Internet of Things IoT devices in the smart home environments. With the proliferation of IOT devices such as smart home environments. With smart thermostats, security cameras, smart locks, and in-home assistants now becoming a mainstream appliance, the risk of cyber-breaches into these related systems has grown exponentially. Such IoT devices may collect and transmit personal/private data; hence, they are a perfect catch for cybercriminals (Spanos et al., 2020). So, the prime objective is to provide data privacy, integrity, and availability and thereby protect the users from breaches and unauthorized access. The project aims to offer a safe environment for the technologies used in smart homes, which will enhance the users’ trust and confidence. Much essence will be embodied in advanced security implementation in such technologies as the users become aware of the risks that arise from the IoT devices to foster adoption and satisfaction.
The project is aimed at the realization of the goal of observing a wide range of regulations related to data protection, among them those specified by the General Data Protection Regulation and the California Consumer Privacy Act itself, which imposes very high demands on data security and privacy.
Scope
The scope of the project is comprehensive covering all the certain key aspects that are necessary to develop along with implementing and maintaining a strong and effective security framework for the smart home IOT devices. The project will eventually encompass the below listed components:
Security Framework Design
Multi-Layered Security Approach: Multiple layers of defense shall be implemented; including but not limited to encryption protocols, secure authentication systems, and intrusion detection mechanisms so that in case of a breach of one layer by a malicious entity, other layers shall continue to safeguard.
Encryption Protocols: Advanced encryption standards like AES-256 shall be utilized for data transmission and storage so that even if intercepted, data becomes undecipherable to any unauthorized entity.
Secure Authentication Systems: Implement multi-factor authentication for maximum access control by implementing a combination of passwords, biometrics, physical tokens, or other elements to prevent unauthorized access.
Intrusion Detection Systems: The use of machine learning-based IDS to monitor network traffic in real-time, detect anomalies, and respond dynamically to potential threats.
Integration with IoT Devices
Device Compatibility: Ensuring the security framework’s compatibility with a large number of smart home IoT devices, and ensuring seamless functionality in the case of different platforms and manufacturers.
Seamless Integration: This means the design will facilitate the framework’s integration with the existing IoT ecosystem without much disruption and still be implemented in a user-friendly fashion.
Development and Testing
Development Platforms: Utilize cutting-edge development tools and platforms to construct and improve the security framework.
Testing Environments: Controlled testing environments that emulate realistic conditions under which the framework shall be extensively tested for efficacy against different threat scenarios.
Pilot Deployment: Initial deployment in selected homes to assess performance, solicit user feedback, and tweak the system before large-scale deployment.
User Training and Support
Training Programs: It is essential to develop comprehensive training programs. These should be designed to educate users on the new security features and how to manage them effectively.
Support Systems: Proper support channels need to be created on the floor to help the users with any problems or queries after deployment for the smooth adoption and operation of the security framework (Akhilesh et al., 2022).
Regulatory Compliance and Ethical Considerations
Standards Conformity: A central role of ensuring that the security framework conforms to the relevant data protection regulations to user’s data privacy and integrity.
Ethical Data Handling: Ensure ethical handling of user data through policies and procedures, obtaining the explicit consent of the user about the handling of his data, and maintaining transparency.
Project Management and Documentation
Project Timeline: It defines a clear project timeline outlining the different phases from its initiation to planning, development, testing, deployment and review at the end.
Resource Allocation: This involves identifying and allocating relevant resources, including personnel, budget, and technological tools (Allifah & Zualkernan, 2022).
Documentation: Ensure proper documentation of all processes, decisions, and outfalls to keep track of the project and for future reference.
Objective
The primary objectives of the Smart Home IoT Security project are as follows: to increase user trust by creating a solid security framework that deals with the critical privacy and security issues, fully complying with all requirements related to data protection laws such as the GDPR and CCPA, thereby saving the company from possible legal risks and enhancing its image as a good, responsible supplier. Also, the project tries to make the products offered by the company unique in a crowded market by providing the best security features that attract consumers who are security conscious, thus giving it a competitive advantage (Yu, Zhang & Zhang, 2021). In addition, by avoiding data breaches and unauthorized access, the project tries to reduce financial risks related to cyber-attacks like potential legal costs, loss of revenue, and loss of brand name.
Assumptions and Constraints
The project on Smart Home IoT Security is founded on some key assumptions. Certain constraints need to be kept in consideration and dealt with critically for the appropriate completion of this project. The significant assumptions this project is founded upon are the availability of required technology and tools for the development and testing of the security framework. It is assumed that state-of-the-art development platforms, encryption protocols, and intrusion detection systems are readily available to the project team. Also, the project’s viability depends on stakeholders’ cooperation and efficient feedback from end-users, IoT device manufacturers, and regulatory bodies. This would aid in the establishment of security requirements, validation of the effectiveness of the security measures, and whether the same are compliant with regulations (Farooq & Hassan, 2021). Also, there is an assumption that the project team embodies the prerequisite expertise and experience in cybersecurity, IoT technology, and software development. Another assumption is that of the budget allocation, where the fixed amount of $150,000 was assumed to be adequate to support the project lifecycle from the initial stages of development, planning, testing, deployment, and maintenance; the budget is to cover staff costs, development tools, testing infrastructure, and support for the project during and after deployment.
In this case, it is assumed not only that the amount will be enough but also that it will be managed well to avoid a financial slump. However, it is also bound by a few essential factors that must be worked within. The project schedule seems to be the most prominent. It has to be done within a certain period. Adherence to this time scale demands that every project phase be properly planned and carried out since delays might Eat up the whole project. The fixed budget of $150,000 is another critical limitation as that will indicate the total outlay that can be spent on this project. This constraint demands careful budgeting and cost management to ensure that all essential activities are funded without overspending.
Another limitation of the availability of resources is brought about, especially by the limited availability of some IoT devices that would be needed in the case of full-scale testing. This will ensure that not all the tests are covered, leaving some vulnerabilities unhandled, which are only device-dependent. Against this issue, there will be biasing of the project towards attaining a representative sample of the commonly used IoT devices, which will ensure a broad applicability of the Security Framework (Ahanger et al., 2021). Technological dependence also forms a significant limitation. The project relies on platforms and tools that are hosted, managed, and operated by a third party for development purposes and assessment, wherein such a reliance may bring about several risks, such as instability of the platforms, compatibility issues, and unavailability of support.
The Smart Home IoT Security project is founded upon some critical assumptions of technology availability, stakeholder cooperation, team expertise, and budget sufficiency; simultaneously, it has to work within constraints of schedule, budget, and resource availability – as well as technology dependence. Having come to terms with these assumptions and limitations, the project intends to bridge the gap and establish a sound security mechanism for smart home IoT devices so that enhanced security, user trust, and regulatory compliance can be achieved by successfully designing and deploying the solution.
Project Organisation
Organizational Structure
In the Smart Home IoT Security project, a hierarchical organizational structure will be applied to have well-defined reporting lines, smooth communication, and efficient task management. This will define the various roles and responsibilities clearly and in a manner that each contributing team member will have a clear understanding of what is expected from them in the project. It will have the Project Manager at the top, with certain specific teams below the project manager, having all team leads in charge of a particular specialty like the Cybersecurity Experts, IoT Device Engineers, Software Developers, Quality Assurance QA, and User Training Specialists. The specific teams will comprise members dedicated to their specialty and report to their respective team lead.
Roles and Responsibilities
Project Manager: The Project Manager shall be responsible for managing the whole project to ensure that it is on track concerning timelines and budgets. This will include interfacing between different teams, resource management, and problem handling arising during the project lifecycle. The Project Manager shall set project milestones, place regular meetings to assess progress and maintain distinct communication with all stakeholders (Ahanger et al., 2021). Also, the Project Manager will facilitate the project meets a pre-determined scope, identify risks and manage them appropriately, and ensure the project meets the organizational multi-concern strategic aspirations.
Cybersecurity Experts: The design and implementation of robust security would be the role of the Cybersecurity Experts with proven experience in smart home IoT. Key responsibilities would include encryption protocols, secure authentication systems, intrusion detection methodologies, threat assessment, identification of possible vulnerabilities, design features that could mitigate specific risks, etc. They shall collaborate closely with the IoT Device Engineers and the Software Developers so any security measures are incorporated to seamlessly complement the operation of the IoT devices and the overall system architecture. The Cybersecurity Experts should also be updated on the latest trends in technology about security and any newly published regulations to ensure compliance and state-of-the-art protection.
IoT Device Engineers: The IoT Device Engineers shall integrate security features designed into the smart home IoT devices. That includes ensuring compatibility across various devices, performance optimization of the security feature, and maintaining the functionality of the current devices. They shall do this in conjunction with the Cybersecurity Experts who implement the security protocols and the Software Developers to ensure the effective integration of software components in the devices.
Software Developers: The Software Developers will develop the software that the IoT devices need to operate safely. This would concern writing codes for security, designing user interfaces, and developing backend systems required for safe data transmission and storage. This would be done in close cooperation with the Cybersecurity Experts, where encryption and authentication procedures will be put in place, and with the IoT Device Engineers, where these soft components will be implemented directly into the devices.
Quality Assurance (QA) Team: In-depth testing and validation of the security framework and its implementation on IoT devices shall be done by the QA Team. Its responsibilities can be enlisted as below: The QA Team shall develop test plans and execute test cases to find defects, problems, and other issues. They will also create very detailed reports on findings and work directly with the development teams to resolve any issues that arise. The QA Team has a huge role in deciding the reliability (Touqeer et al., 2021) and robustness of the security framework before it is ever deployed to end-users.
User Training Specialists: The User Training Specialists will train the end-users to use the new security features and ensure a person can effectively use them. This position shall create documents for training purposes and conduct training sessions on all the security features. Provide ongoing facilitation and support to users. The User Training Specialists shall generate user manuals, video tutorials, and FAQs for the help of users regarding understanding and managing security features (Alshboul et al., 2021). They will also be gathering feedback from users to understand any confusing or painful aspects of the process and work with development teams to make this smoother for the end users. For any project’s success, it is an absolute must that end users feel adequately informed and comfortable with new security features.
Managerial Process Plan
This section talks about the start-up plan of the project, the risk management plan of the project, and then the closing plan of the project.
Project Start-up Plan
Kickoff Meeting: This is an initial meeting with stakeholders to define the goals and deliverables of the project.
Resource Allocation: Resource allocation involves team member allocation and tool and platform acquisition.
Project Charter: The document defines the project scope and objectives and identifies the project stakeholders.
Risk Management Plan
The Smart Home IoT Security project’s successful completion depends upon identifying potential risks. These include:
Technical Failures: Hardware or software failures which may hamper the process of development and implementation of any feature of security.
Budget Overruns: Unplanned expenses of an amount in excess of the budgeted $150,000.
Delays: missing of project milestones. This is because either the “resources can not be made available or there is a “technical hurdle that was not anticipated “.
Resource constraints: Either specific IoT devices needed to perform a test are not available or non-availability of crucial personnel are.
Compliance Issues. Failure to fully comply with some regulatory standards, for example, GDPR or CCPA.
Cybersecurity Threats: These are the new, emerging threats likely to compromise the security framework upon or after implementation.
Risk Analysis
Each of the identified risks is evaluated for its impact and likelihood:
Technical Failures: Higher impact, moderate likelihood.
Budget Overruns: Very high impact, moderate likelihood.
Delays: Moderate impact, high likelihood.
Resource Constraints. Medium impact, medium likelihood.
Compliance Issues: High impact-low likelihood.
Cybersecurity Threats: Very High Impact and Moderate Likelihood
Risk Mitigation
Risks’ impacts minimization strategies include the following:
Technical Failures Implement regular testing and maintenance schedules, and maintain a backup system for critical components.
Budget Overruns: Instigate contingency fund also allocated a regular review for each budget drawn.
Delays: A Project timeline with buffer periods has to be created along with clear communication among the team members.
Resource Constraints: Maintain a dynamic resource allocation plan and cross-train the team members.
Compliance Issues Activate legal experts who ensure compliance with the regulations. Regular compliance audits should be carried out.
Cybersecurity Threats: Security protocols- constantly update them along with doing real-time threat monitoring.
Project Closeout Plan
| Project Closeout Plan | Details |
| Final Deliverables | Ensure that all project deliverables, such as the security framework, user manuals, and training materials, are completed and meet predefined quality standards. |
| Project Review | Conduct a review meeting with all stakeholders to discuss the project’s successes, challenges, and areas for improvement. This review will help capture valuable insights for future projects. |
| Documentation | Compile all project-related documents and reports, including design documents, test results, user feedback, and training materials. Proper documentation ensures that the project’s outcomes and processes are well recorded. |
| Closure Report | Prepare a final report summarizing the project outcomes, including an assessment of objectives met, performance metrics, and lessons learned. This report will provide a comprehensive overview of the project’s impact and highlight best practices for future initiatives. |
Bottom of Form
Technical Process Plan
Development Process Model
Description of the Chosen Development Model: Agile
The Agile development method will be utilized in the Smart Home IoT Security project. Agile is a flexible, step-by-step method of creating software by undertaking small, incremental amounts of effort, emphasizing teamwork, customer input, and deadlines for each stage. Unlike traditional Waterfall methods, which demand the completion of one phase before work can begin on another phase, Agile development and testing co-occur. Work is divided into a series of short, manageable chunks or sprints, ensuring the project is not prolonged. Where, in each sprint, some tasks are given higher priority, and completed first. Such as coding, testing, or the introduction of new features (Guerrero-Ulloa, Rodríguez-Domínguez & Hornos, 2023). This cyclic process allows the team to have a functional prototype of the project at the end of each sprint, which can be checked and refined based on the feedback. Scrum ensures continuous communication among team members and with stakeholders through various meetings, such as daily stand-ups, sprint reviews, etc., that encourage teamwork.
The flexibility of Agile suits the Smart Home IoT Security project best because security threats keep changing, and updates are needed on time. The team that will be carrying out the project will accommodate new security issues, user feedback, and improvements with Agile without needing to wait till the project is complete.
Justification for Selecting this Model
The reasons the Agile methodology was chosen for the Smart Home IoT Security are:
First, the IoT security domain is fast-paced and dynamic and requires flexibility in development. Then also being iterative allows this methodology to respond quickly to newfound threats or security features in its cycle.
Secondly, Agile encourages continuous interaction among developers, security experts, and end-users (Moedt van Bolhuis et al., 2023). This interaction is essential in the early identification of problems and ensuring that the security solutions will indeed meet the needs of the user.
Finally, the in-built feedback loops of Agile help to ensure the high quality and usability of the security features. Reviewing and refining at the end of each sprint gives the team the means to ensure the final product is robust, user-friendly, and secure.
Therefore, Agile is very suitable for addressing the unique challenges of developing a comprehensive and efficient smart home IoT security solution.
Analysis of Technical Methods and Tools
Development tools
Integrated Development Environment (IDE): Where it will use Visual Studio Code as it supports a wide range of programming languages and also has lots of useful extensions available.
Programming Languages: The selection of programming languages is done with Python and JavaScript. Python is very flexible with security analysis and automation. With Python, this course also adds the most critical elements of JavaScript for building user interfaces.
Security tools
Penetration Testing: OWASP ZAP and Kali Linux are some of the tools that will be used to simulate cyber-attacks to find and fix vulnerabilities (Devi & Kumar, 2020). These tools will play a very important role in identifying gaps or vulnerabilities which may exist within the system and will allow it to foster its security.
Encryption: Where special focus will be made on the transmission of data between devices will be encrypted with encryption protocols by using OpenSSL.
Testing tools
Automated Testing: In order to perform the user interface testing will use Selenium. The tool is very well-known for its efficient testing performance and for highlighting the lapses that occur within an interface of any type of system or application.
Load Testing: The system’s performance will be tested under various conditions like load by Apache JMeter to check if it is withstanding the various types of loads and pressure conditions at the time of rigorous tasking.
Monitoring tools
Network Monitoring: Wireshark shall be used to analyze network traffic to trace unusual actions.
Device Management: Ansible is going to be in charge of the configuration and updates of IoT devices to ensure they are kept secure and updated.
Evaluation of the Tools’ Effectiveness and Compatibility
The chosen tools are relevant and effective in carrying out the requirements of the project. Visual Studio Code is a productive and easy-to-use IDE with support for multiple languages, including robust out-of-the-box extensions tailored for Python and JavaScript. This further ensures the development experience is seamless and interoperable across various programming environments. Python and JavaScript are chosen because they are very efficient in the work areas stated. In the large Python libraries, there will be a wide range of security checks, while JavaScript will undertake the dynamic creation of Web UIs (Panduman et al., 2022). Since these two languages are so enormously popular nowadays, this practice will always guarantee solid community and stable technical support.
OWASP ZAP and Kali Linux are the most commonly used tools for penetration testing. Features offered by these tools for finding and fixing security weaknesses go on an extensive scale. Therefore, OWASP ZAP and Kali Linux can effectively secure IoT devices (Abdullah, (2020).
OpenSSL is a strong tool for encryption implementation, known for its reliability in securing data during transmission, ensuring data remains private and unchanged. Selenium and Apache JMeter-but potent test tools. Selenium performs reliable and extensive automation of testing interfaces, while JMeter tests the performance of the system under a large number of scenarios, checking its efficiency against these loads.
Wireshark and Ansible are valid for managing and controlling the network and the different devices. Wireshark monitors the traffic in the network and will very quickly detect any strange patterns, while Ansible automates the management process of the devices for their security. Both tools fit perfectly with the requirements of this project, meaning that the development process of the Smart Home IoT Security will be secure, efficient, and easy to manage.
Approach and Analysis
Segmentation network is all about isolating IoT from all other parts of the network to make it more secure. This technique makes it more secure by reducing malware risks and unauthorized access. That is so because because, by breaking down an extensive network into definite spec zones, even though one area is breached, it is pretty hard for attackers to reach other zones. But segmentation adds complexity to the network management and needs increased setup effort of hardware required for the same. Despite these issues, network segmentation is a must to control security breaches because it will prevent an attacker from moving laterally inside a network, thereby minimizing the impact of such a security breach to a great extent. The authentication and authorization of devices are very crucial to maintaining the security of all IoT devices. In the project, robust and efficient authentication and authorization technologies will be used that allow only authorized devices to connect to the network. This technique reduces the possibility of unauthorized access and security breaches to a great extent. However, their implementation over different devices of varying capability might be bound to be a challenging task, which requires adequate planning and testing of compatibility. Reliable authentication methods prevent unauthorized access because only trusted devices can communicate over the network, which is instrumental in keeping the system intact.
Data encryption will also be done, and it will end-to-end so that the data sent from IoT gadgets gets encrypted. The mechanism will assist in ensuring data privacy and integrity, whereby the risk of being exposed is minimal. Latency problems are created using encryption, and these may cause some issues in transferring the data. There is still a need for encryption because exposure to data and data breaches is a real threat to IoT systems.
Ethical Implications
The Smart Home IoT Security project would have several critical ethical considerations that need to be addressed to keep the user rights secured and their trust intact. Ethical implications for the Privacy of Data, Consent of Users, Transparency, and Regulatory Compliance would be the prime ones.
Data Privacy: Data privacy is a paramount in the context of smart home IOT devices that often handle sensitive and personal information. The project’s multi rare security approach aims to eventually ensure that all the user data is effectively encrypted and kept secure while defending unauthorized access along with any kind of security breaches.
User Consent: Another critical point, from an ethical point of view, refers to the need to obtain the direct and express consent of the user before their data is collected and processed. The user shall be adequately informed about what data will be collected, for what it will be used, and how it will be protected (Majumder, Veilleux & Miller, 2020). Clear and straightforward procedures for obtaining consent will be available in this project so that users may knowingly decide on their data.
Transparency: Transparency is also essential in building trust between us and the providers of this technology. In that regard, this project will make sure that the users understand in full detail the security put in place and the workings of the use of their data (Wan). That will involve extensive and easily understandable information on the protocols used for encryption, the systems designed for authentication, and the mechanisms for intrusion detection in place.
Compliance: Complying with the various existing regulations, such as GDPR and CCPA, is a requirement by law and ethics. The regulations are envisioned to protect user rights and ensure responsible management of personal data. In realizing this, the project shall fully comply with all the rules by implementing practices that meet or exceed the standards set for data protection in the rules.
References
Abdullah, H. S. (2020). Evaluation of open-source web application vulnerability scanners. Academic Journal of Nawroz University, 9(1), 47-52. https://journals.nawroz.edu.krd/index.php/ajnu/article/download/532/398
Ahanger, T. A., Tariq, U., Ibrahim, A., Ullah, I., & Bouteraa, Y. (2020). Iot-inspired framework of intruder detection for smart home security systems. Electronics, 9(9), 1361.https://www.mdpi.com/2079-9292/9/9/1361
Akhilesh, R., Bills, O., Chilamkurti, N., & Chowdhury, M. J. M. (2022). Automated penetration testing framework for smart-home-based IoT devices. Future Internet, 14(10), 276. https://www.mdpi.com/1999-5903/14/10/276
Allifah, N. M., & Zualkernan, I. A. (2022). Ranking security of IoT-based smart home consumer devices. Ieee Access, 10, 18352-18369.https://ieeexplore.ieee.org/iel7/6287639/6514899/09698229.pdf
Alshboul, Y., Bsoul, A. A. R., Al Zamil, M., & Samarah, S. (2021). Cybersecurity of smart home systems: Sensor identity protection. Journal of Network and Systems Management, 29(3), 22.https://www.researchgate.net/profile/Abed-Al-Raoof-Bsoul/publication/349804291_Cybersecurity_of_Smart_Home_Systems_Sensor_Identity_Protection/links/627591ab2f9ccf58eb32f241/Cybersecurity-of-Smart-Home-Systems-Sensor-Identity-Protection.pdf
Devi, R. S., & Kumar, M. M. (2020, June). Testing for security weakness of web applications using ethical hacking. In 2020 4th International Conference on Trends in Electronics and Informatics (ICOEI)(48184) (pp. 354-361). IEEE. https://www.researchgate.net/profile/Mohankumar-Kumar/publication/343038606_Testing_for_Security_Weakness_of_Web_Applications_using_Ethical_Hacking/links/6142e138dabc4638f12b88b2/Testing-for-Security-Weakness-of-Web-Applications-using-Ethical-Hacking.pdf
Farooq, M., & Hassan, M. (2021). IoT smart homes security challenges and solution. International Journal of Security and Networks, 16(4), 235-243.https://www.researchgate.net/profile/Mansoor-Farooq-3/publication/356544776_IoT_smart_homes_security_challenges_and_solution/links/62c415a99a17145f5f468b1f/IoT-smart-homes-security-challenges-and-solution.pdf
Guerrero-Ulloa, G., Rodríguez-Domínguez, C., & Hornos, M. J. (2023). Agile methodologies applied to the development of Internet of Things (IoT)-based systems: A review. Sensors, 23(2), 790. https://www.mdpi.com/1424-8220/23/2/790
Majumder, A. J. A., Veilleux, C. B., & Miller, J. D. (2020). A cyber-physical system to detect IoT security threats of a smart home heterogeneous wireless sensor node. IEEE Access, 8, 205989-206002.https://ieeexplore.ieee.org/iel7/6287639/8948470/09253655.pdf
Medileh, S., Laouid, A., Euler, R., Bounceur, A., Hammoudeh, M., AlShaikh, M., … & Khashan, O. A. (2020). A flexible encryption technique for the internet of things environment. Ad Hoc Networks, 106, 102240. https://e-space.mmu.ac.uk/625910/1/A_Flexible_Encryption_Technique_for_the_Internet_of_Things%20%281%29.pdf
Moedt van Bolhuis, W., Bernsteiner, R., Hall, M., & Fruhling, A. (2023). Enhancing IoT Project Success through Agile Best Practices. ACM Transactions on Internet of Things, 4(1), 1-31. https://dl.acm.org/doi/pdf/10.1145/3568170
Osman, A., Wasicek, A., Köpsell, S., & Strufe, T. (2020). Transparent Microsegmentation in Smart Home {IoT} Networks. In 3rd USENIX Workshop on Hot Topics in Edge Computing (HotEdge 20). https://www.usenix.org/system/files/hotedge20_paper_osman.pdf
Panduman, Y. Y. F., Funabiki, N., Puspitaningayu, P., Kuribayashi, M., Sukaridhoto, S., & Kao, W. C. (2022). Design and implementation of SEMAR IoT server platform with applications. Sensors, 22(17), 6436. https://www.mdpi.com/1424-8220/22/17/6436
Spanos, G., Giannoutakis, K. M., Votis, K., Viaño, B., Augusto-Gonzalez, J., Aivatoglou, G., & Tzovaras, D. (2020, August). A lightweight cyber-security defense framework for smart homes. In 2020 International Conference on INnovations in Intelligent SysTems and Applications (INISTA) (pp. 1-7). IEEE.. https://ieeexplore.ieee.org/abstract/document/9194689/
Tahir, M., Sardaraz, M., Muhammad, S., & Saud Khan, M. (2020). A lightweight authentication and authorization framework for blockchain-enabled IoT network in health-informatics. Sustainability, 12(17), 6960. https://www.mdpi.com/2071-1050/12/17/6960
Touqeer, H., Zaman, S., Amin, R., Hussain, M., Al-Turjman, F., & Bilal, M. (2021). Smart home security: challenges, issues and solutions at different IoT layers. The Journal of Supercomputing, 77(12), 14053-14089.https://www.researchgate.net/profile/Mudassar-Hussain-2/publication/351459297_Smart_home_security_challenges_issues_and_solutions_at_different_IoT_layers/links/6263d2338e6d637bd1f6f177/Smart-home-security-challenges-issues-and-solutions-at-different-IoT-layers.pdf
Wan, Y., Xu, K., Xue, G., & Wang, F. (2020, July). Iotargos: A multi-layer security monitoring system for internet-of-things in smart homes. In IEEE INFOCOM 2020-IEEE Conference on Computer Communications (pp. 874-883). IEEE. https://par.nsf.gov/servlets/purl/10191612
Yu, R., Zhang, X., & Zhang, M. (2021, March). Smart home security analysis system based on the internet of things. In 2021 IEEE 2nd International Conference on Big Data, Artificial Intelligence and Internet of Things Engineering (ICBAIE) (pp. 596-599). IEEE. https://ieeexplore.ieee.org/abstract/document/9389849/
Project Description
Business Stakeholders
Name | Contact | Impact | Influence | Concern | Contribution | Engagement Strategy |
Smart Home Device Manufacturers | High – Product design and security | High – Technology implementation | Ensuring device security | Provide secure IoT devices | Regular meetings, collaboration on design | |
Homeowners | High – Users of IoT devices | Medium – Adoption of security measures | Privacy, safety, ease of use | Feedback on user experience | Surveys, user forums, awareness campaigns | |
Cybersecurity Firms | High – Security implementation | High – Expertise in cybersecurity | Effective threat detection and mitigation | Expertise and advanced security solutions | Partnerships, joint R&D projects | |
Internet Service Providers (ISPs) | Medium – Network security | Medium – Influence on network security | Secure internet connectivity | Secure internet infrastructure | SLAs, regular security audits | |
Government Regulatory Bodies | High – Compliance and regulations | High – Enforcement of security standards | Compliance with data protection laws | Regulations, guidelines, oversight | Policy consultations, compliance reports | |
Privacy Advocacy Groups | Medium – Advocacy and awareness | Medium – Influence on public opinion | User privacy and data protection | Raising awareness, lobbying for privacy | Collaboration on privacy guidelines |
Project Overview
Internet of things (IoT) has been found to be widely used and adapted by various industries due to its features and capabilities. IoT devices have revolutionized the way in which people live as it also offers how wide range of feature that make it convenient for any kind of business operation or even the smallest of things to be done efficiency and automatically (Eltresy et al., 2021). However, with this technological advancement, IoT devices and communication has also been found to have several security risks associated to it. The security risks include unauthorized access, data breaches, and potential control by malicious entities.
Detailed Explanation
The project includes design as well as development of a smart home IoT infrastructure that will be implemented with multi-layered security approach that will be implemented significantly for the smart home environment (Choi et al., 2021). The IoT smart home infrastructure will include installation, and connection of IoT devices as a home network setup where various IoT functionalities will be utilized and the user will be able to communicate and operate the devices through their end devices such as mobile phone and tablets (Davis, Mason & Anwar, 2020). It will include the integration of significant encryption protocols, secure authentication systems, and intrusion detection systems. By addressing vulnerabilities at both the device and network levels, the solution aims to protect sensitive user data and ensure the reliable operation of smart home systems.
Proposed Solution
Effectiveness Comparison
Multilayered Security Approach: The solution that has been proposed for IoT smart home infrastructure includes a multilayered security approach which includes encryption protocols, secure authentication systems as well as intrusion detection systems (Gazis & Katsiri, 2021). This method is better than the single layered security solution since it often fails to address the complex nature of IoT security threats.
Encryption Protocols: The data transmission between IoT devices will be protected by the use of advanced encryption protocols, for example AES-256 encryption which is such a technique that even if data interception occurs it cannot be read by unauthorized users (Wan et al., 2020). AES-256 provides more secure way when compared with other simpler methods such as AES-128 because its keys are long and it makes it very hard to break.
Secure Authentication Systems: The use of multi-factor authentication (MFA) enhances security as it requires multiple forms of verification before getting access (Abdulla et al., 2020). This is more effective than that compared to single factor authentication as it only depends upon passwords and it can easily be compromised.
Intrusion Detection Systems: Machine learning based intrusion detection systems will keep track of any suspicious activities on the network and consequently respond to possible threats. This is better than traditional IDS that rely mostly on a predetermined signature for only known threats. By recognizing deviating activity trends, Machine learning-based IDS is able to recognize unknown threats and thereby, having a much more active response on security.
Comparison with Alternative Approaches
Traditional Security Approaches: Traditional security approaches such as basic firewall setup, and antivirus software are not sufficient when it comes to IoT smart home infrastructure an it only focuses on protecting the endpoint devices and do not offer support to the interconnected nature of IoT devices (Mabodi et al., 2020). Additionally, they are reactive rather than proactive which often leads them to mitigate threats only after they have occurred.
Alternative IoT Security Solutions: While some may be dedicated to certain fields like network or device security, many IoT security solutions do not provide a comprehensive approach for security. For example, others can be overly dependent on updates of device firmware, yet this does not resolve the issues of network insecurity. The solution that has been proposed here, is more comprehensive as it incorporates security measures at both network and device levels so that one can have better protection against possible threats.
Significance of the Project
The following are some of the significance with respect to the IoT smart home office;
Enhanced User Trust: The proposed solution significantly enhances user trust by ensuring the privacy and security of their data. This is crucial for the adoption of smart home technologies which is relate to the data breaches and unauthorized access that might hamper the users from being able to use the IoT devices.
Regulatory Compliance: Implementation of security measures can ensure compliance with data protection laws such as GDPR and CCPA. This avoids any kind of potential fine that can degrade the reputation.
Financial Risk Mitigation: By preventing data breaches and unauthorized access, the proposed solution mitigates financial risks associated with cyberattacks.
Project Plan
Resource
The successful completion of this project will require a diverse team of specific resources and the following are some of the human resources for this project;
IoT Device Engineers: Will be responsible for integrating the security framework into the IoT devices in order to ensure seamless functionality and compatibility.
Cybersecurity Experts: Responsible for designing and implementing security features to protect the IoT devices and network.
Software Developers: Will be responsible to develop the software components that is needed for the secure operation and user interaction with the IoT devices.
Project Manager: The project manager will be responsible to develop the timeline, cost and allocated resources as per need while being the mode of communication between project team and stakeholders.
The successful completion of this project will require specific resources and the following are some of the essential resources for this project;
Smart Home IoT Devices: A variety of smart home devices will be needed for practical implementation and testing of the security features.
Development platform: Software tools and platforms are necessary for coding, testing, and deploying the security solutions.
Testing Environment: Controlled environments to simulate real-world conditions and thoroughly test the effectiveness of the infrastructure.
Cost
Expense Category | Allocation Amount | Description |
Personnel Costs | $90,000 | Allocated for cybersecurity experts, IoT device engineers, and software developers |
Development Tools | $30,000 | For purchasing and licensing development platforms and software tools necessary for the project |
Testing Infrastructure | $10,000 | For setting up and maintaining testing environments |
Maintenance and Updates | $20,000 | Allocated for ongoing maintenance and updates to the security framework post-deployment |
Total Estimated Budget | $150,000 | Ensures adequate funding for all phases of the project, from initial development to support |
This budget ensures that all phases of the project are comprehensively funded, from initial development to post-deployment supported.
Timeline
Phase | Duration | Activities |
Phase 1: Requirement Gathering and Stakeholder Consultation | 1 month | Engage with stakeholders to gather detailed requirements and specifications. |
|
| Understand the security concerns and expectations of homeowners, manufacturers, and regulatory bodies. |
Phase 2: Design and Architecture of the Security Framework | 2 months | Develop a comprehensive security framework for the smart home IoT environment. |
|
| Design multi-layered security protocols, including encryption, authentication, and intrusion detection. |
Phase 3: Development and Integration of Security Features | 3 months | Implement the security measures into the smart home IoT infrastructure. |
|
| Ensure seamless integration of security features with IoT devices and user interfaces. |
Phase 4: Testing and Validation | 2 months | Conduct testing of the security framework in controlled environments. |
|
| Validate the effectiveness of security measures against various threats. |
Phase 5: Deployment and User Training | 1 month | Deploy the security framework across selected smart home environments. |
|
| Conduct training sessions for users to ensure effective use of the security features. |
Phase 6: Final Review and Project Closure | 1 month | Review project outcomes against initial objectives and requirements. |
|
| Document lessons learned and best practices for future projects. |
|
| – Close the project with a final report to stakeholders and a plan for ongoing support and updates. |
Conclusion
The proposed project has been aimed to develop a comprehensive security framework which would secure the smart home IoT devices against such threats. Here, a smart home with IoT devices will be developed while incorporating various security features in it. By incorporating advanced encryption protocols, secure authentication, and intrusion detection systems, the project aims to mitigate the significant security risks associated with IoT devices. The proposed solution offers enhanced protection compared to traditional methods that ensures the safety of user data and reliable operation of smart home systems. The proposal also provides detailed project plan that has been given here in order to deliver the significant business value and promote reliability in smart home technologies.
References
Abdulla, A. I., Abdulraheem, A. S., Salih, A. A., Sadeeq, M. A., Ahmed, A. J., Ferzor, B. M., … & Mohammed, S. I. (2020). Internet of things and smart home security. Technol. Rep. Kansai Univ, 62(5), 2465-2476. https://sciendo.com/pdf/10.2478/cait-2021-0029
Choi, W., Kim, J., Lee, S., & Park, E. (2021). Smart home and internet of things: A bibliometric study. Journal of Cleaner Production, 301, 126908. https://fardapaper.ir/mohavaha/uploads/2021/06/Fardapaper-Smart-home-and-internet-of-things-A-bibliometric-study.pdf
Davis, B. D., Mason, J. C., & Anwar, M. (2020). Vulnerability studies and security postures of IoT devices: A smart home case study. IEEE Internet of Things Journal, 7(10), 10102-10110. https://ieeexplore.ieee.org/ielaam/6488907/9219268/9050664-aam.pdf
Eltresy, N. A., Dardeer, O. M., Al-Habal, A., Elhariri, E., Abotaleb, A. M., Elsheakh, D. N., … & Abdallah, E. A. (2020). Smart home IoT system by using RF energy harvesting. Journal of Sensors, 2020(1), 8828479. https://onlinelibrary.wiley.com/doi/pdf/10.1155/2020/8828479
Gazis, A., & Katsiri, E. (2021). Smart home IoT sensors: Principles and applications a review of low-cost and low-power solutions. International Journal on Engineering Technologies and Informatics, 2(1), 19-23. https://skeenapublishers.com/journal/ijeti/IJETI-02-00007.pdf
Mabodi, K., Yusefi, M., Zandiyan, S., Irankhah, L., & Fotohi, R. (2020). Multi-level trust-based intelligence schema for securing of internet of things (IoT) against security threats using cryptographic authentication. The journal of supercomputing, 76, 7081-7106. https://arxiv.org/pdf/2001.05354
Wan, Y., Xu, K., Xue, G., & Wang, F. (2020, July). Iotargos: A multi-layer security monitoring system for internet-of-things in smart homes. In IEEE INFOCOM 2020-IEEE Conference on Computer Communications (pp. 874-883). IEEE. https://par.nsf.gov/servlets/purl/10191612
ASSESSMENT 3
Assessment Task: Project Action Plan Review Report
Student Name:
Student ID:
University Name:
Author’s Note:
Table of Contents
Issues, Risk and Change Management
Project Overview
The smart home security project that has been proposed here is aimed to design and develop a smart home IT infrastructure that would include enhanced security with respect to IT devices within the smart home such that it can address the growing concerns regarding unauthorized access, database, and potential control by unwanted malicious users. The primary purpose of this report is to develop a comprehensive infrastructure for smartphone that integrates comprehensive security framework and also ensures the security operations of IoT devices within smart home environment. The following are the project goals associated with this project;
Designing and implementing multi-layered security measures to protect IoT devices from cyber threats.
Enhancing user privacy and data protection through robust encryption and authentication mechanisms.
Developing intrusion detection systems to detect and respond to security breaches in real-time.
Ensuring seamless integration of security features with existing IoT devices and user interfaces.
Providing homeowners with a secure and reliable smart home experience.
It is important to secure IoT devices within the smart home since devices has the sensitive nature of data that the values such as personal information, surveillance footage, home automation controls and others security breach in the IoT infrastructure can lead to serious consequences that includes privacy violations, property damage and might get access to sensitive data. The scope of the project includes the development of IoT smart home infrastructure which is integrated with security framework that includes all aspects of smart home IoT devices, from initial setup to daily operation. This framework will include functionalities such as encryption, authentication, and intrusion detection, which is specifically related for smart home environments. The project will also involve testing the operative ability of the IoT smart home environment and security framework in real-world scenarios to ensure its effectiveness and reliability.
Project Usage Scenarios
The smart home IoT security project has been found to offer benefits to the diverse range of stakeholders that have been involved in the smart home IoT project. These benefits are associated with the smart home device manufacturers, smart home owners, cybersecurity firms, Internet Service Providers (ISPs), government regulatory bodies, and privacy advocacy groups.
Smart Home Device Manufacturers: With respect to smart home device manufacturers, the project provides an opportunity to improve market competitiveness and customer trust. The manufacturers will be able to make an impact where they will be able to improve their brand image such that they will seem reliable and efficient for the customers as the customers will see find it secure and reliable (Moedt van Bolhuis et al., 2023). For example, A smart lock manufacturer can advertise their product as having advanced encryption and authentication features, which can satisfy the customers and give their competition a tough competition in the market.
Home Owners: On the other hand, homeowners are able to have more privacy and security for their smart home devices and personal information. This will enable them to securely manage and monitor their smart home gadgets remotely via the Smart Home IoT safety project. Even in their absence, the homeowner can keep monitor on burglars with the help of mobile applications that provide them with SMS updates on real-time basis and can operate the cameras they have fitted in their houses so as to ensure its security.
Cybersecurity Firms: cybersecurity firms have also been found to benefit from the increased demand of cyber security services as well as solution with respect to smart home security projects (Wan et al., 2020). As the smartphone IT security project have been found to develop better traction, donations will be able to offer specialized security services with respect to the smart home services in order to secure the smart home infrastructure. For example, a cybersecurity firm will be able to provide and conduct penetration testing services over the smart home infrastructure that will be done in order to identify and mitigate existing vulnerabilities for the vulnerabilities that might occur in the near future, and such vulnerabilities could be mitigated.
Government Regulatory Bodies: Government regulatory bodies also benefit from the Smart Home IoT security project as it allows improved regulation and standards for IoT security. Governments can implement laws and guidelines to ensure that the IoT devices meet required security standards (Mabodi et al, 2020). This can reduce the risk of cyberattacks and also protect the customers. For example, these government bodies can implement rules such that all smart home devices that are developed must comply with specific security standards as this would create more secure environment for the adoption of smart home IoT infrastructure.
Internet Service Providers (ISPs): With the Smart Home IoT security project, Internet Service Providers (ISPs) will be able to become different from their competitors and build a strong customer base. Secure communication with respect to IoT security features can be beneficial for the devices that are connected on a network and it must be provided by the associated ISP (Gazis & Katsiri, 2021).
Privacy Advocacy Groups: The privacy groups have been found to provide IoT security project such that it can create issues while also promote the protection of privacy right. These groups have been found to educate the public regarding the importance of securing the IoT devices while also advocate stronger security and privacy measures (Eltresy et al., 2020). For example, an advocacy group can create campaign with respect to laws that require IoT manufacturers to prioritize user privacy and data protection in their products that can empower consumers and also promote responsible IoT development.
The Smart Home IoT security project offers significant benefits to stakeholders across the smart home environment (Gazis & Katsiri, 2021). By enhancing security and privacy protection in the IoT smart home office, the project has been found to contribute to a safer and more secure smart home environment for everyone included in it along with providing trust and innovation that becomes more responsible for IoT technologies.
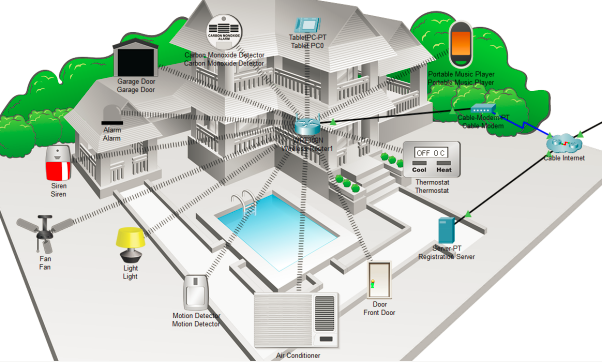
Project Architecture
Project Architecture
The above figure is the architectural diagram of a smart home system. It illustrates that various components and devices have been integrated into a residential building in order to enable automation, security, and energy management functionalities (Choi et al., 2020). The diagram presents a visual representation of the overall architecture of a smart home system. In the figure, it could be seen that a house with different connected devices and components are present. The key elements shown include:
Security components: Carbon monoxide detectors, motion detectors, alarm system, and siren.
Climate control: Air conditioner, thermostat, and fan.
Connectivity: Cable modem, cable internet, and a registration server.
Appliances and devices: Garage doors, tablet PC, portable music players, and lights.
The following is the detailed outline of the IoT smart home architecture;
Home Network Gateway (Wireless Router): The central hub has been found to provide connection to all IoT devices in the home network.
Internet Connection (Cable Modem): This component provides internet access for remote control and monitoring.
User Devices (Tablet PC, Portable Music Player): These are the devices used by homeowners to interact with and control the smart home system.
Server (Registration Server): Servers have been stored in the infrastructure which makes sure that it manages device registration, authentication, and data storage.
Development Platforms:
Arduino IDE: Utilized for programming microcontroller-based IoT devices.
Raspberry Pi OS: Operating system for Raspberry Pi devices used as the home network gateway.
Software Tools:
OpenSSL: Used to mplement encryption protocols to secure data transmission between IoT devices and user interfaces.
Wireshark: It is a network protocol analyzer used for monitoring and troubleshooting network traffic (Davis, Mason & Anwar, 2020).
Suricata: It is an open-source network threat detection engine for intrusion detection.
Technologies:
MQTT (Message Queuing Telemetry Transport): MQTT is a messaging protocol which is used for efficient communication between IoT devices and the central hub.
Zigbee and Z-Wave: Wireless communication protocols that is used by smart home devices to ensure reliable and low-power connectivity (Tahir et al., 2021).
Firebase: Provides cloud storage and real-time database services for the management of data across devices.
Third-Party Libraries/Tools
OpenSSL: Implements encryption protocols to secure data transmission between IoT devices and user interfaces.
Suricata: It is an open-source network threat detection engine for intrusion detection.
Use Case Diagram
The image presents a use case diagram for an IoT Smart Home Architecture, that outlines the interactions between the customer, IoT device manufacturers, and the ISP/cloud provider. The figure shows the following;
Customer can register/sign in, access IoT devices, control appliances, utilize smart services, and monitor devices via an end device.
ISP/cloud provider offers services like providing ISP, cloud data storage, security, and data management (Davis, Mason & Anwar, 2020).
IoT device manufacturers provide IoT devices and process payments, while complying with regulatory laws.
Key functionalities include device access, appliance control, smart services utilization, device monitoring, security provisioning, and data management (Spanos et al., 2022).
Interactions between the actors enable seamless smart home operations and services.
Issues, Risk and Change Management
Timeline and Resource Management
The management of timeline as well as resources for the smart home IoT security project had been found to be crucial in order to make it a success. Detailed project plan had been developed that had outlined all the phases that have been included in the project starting from requirement gathering till the final review and project closure. Gantt chart as well as project management software had been used in order to progress keep an eye on the problems that had been made by the project says that the project management team can ensure that the deadlines have been met successfully (Osman et al., 2021). Regular status meetings were held with the project team to review progress and address any issues promptly. Critical resources had been composed of a team of cybersecurity specialists, IoT device engineers, software developers, and the required tools and platforms for development and testing. Resource distribution as well as allocation allowed for each team member in getting all the help that they needed along with the instruments thus, making it possible to work quickly (Panduman et al., 2022). Additionally, there were backup strategies prepared in order to deal with time wasting or lack of supplies such that the project can continue as planned.
Challenges Faced
Security Protocol Integration: One of the major challenges was to integrate advanced security protocols into the IoT devices however, it was not supposed to affect the performance system IoT devices found to have limited processing powers along with memory which made it difficult to implement the security features (Touqeer et al., 2021). To overcome this, significant encryption algorithms and efficient authentication mechanisms had been selected. The team also collaborated closely with device manufacturers to ensure seamless integration without compromising performance.
Interoperability Issues: One of the significant challenges faced in this report was how to ensure that the entire security framework of the internet connected things aspects was compatible with a wide range of devices from different manufacturers. Diverse devices have been used along with diverse communication protocols and standards (Yu, Zhang & Zhang, 2021). In order to have an operational strategy, a design had been created for a security platform that allowed for flexibility while maintaining modularity thus enabling customization with regard to both devices and the standards themselves. To resolve compatibility problems extensive tests were undertaken using numerous gadgets.
User Participation: It was another challenge to convince household proprietors to accept and use properly the security features. Not all users are conversant with technology and thus some of them might fail to comprehend while executing security measures (Wan et al., 2020). User friendly interfaces and significant user training programs were developed and this has been done for users to realize why it matters and how they can use the security feature effectively related educational resources are such as tutorials, and FAQs were made available.
Change Management
Several changes were made to the initial project plan to address emerging issues and improve the project’s overall effectiveness.
Enhanced Security Measures: Initially the project plan included basic encryption and authentication protocols for enhanced security measures. However, it was decided through further research and stakeholder feedback that they should adopt more advanced security measures among others multi-factor authentication and real-time intrusion detection systems and hence, they made this change in order to address likely flaws effectively and provide an even greater degree of safety.
Extended Testing Phase: In the original plan, two months had been allocated with respect to testing as well as validation phase. However, it had come out to be apparent in such a manner that the testing and validation phase required more time in order to conduct testing across various devices as well as scenario with respect to the smart home infrastructure. Further, the testing as well as validation phase has been extended by adding one month extra in order to ensure that every potential security that the system could perform under any kind of situation.
User Training and Support: When the initial plan was being made, it was intended to have a brief user training session during the deployment period as well. However, it was obvious that there was a need for more thorough training and support from the reactions of some users who volunteered. To do this, the training program has now been modified so that it comprises various sessions, user manuals that are more detailed together with continuous assistance through telephone calls as well as website-based materials (Abdulla et al., 2020).
Resource Reallocation: In order to manage the scope of security measures that had been increased and extended testing phase, additional resources were required to be allocated. Due to this scenario, the project had been required to hire more cybersecurity expert but also extending the contract of keeping members. Various budget adjustment had to be made in order to accommodate certain changes so that the project could be conducted successfully.
Hence, effective timeline and resource management had been done with the combination of adaptive strategies to overcome challenges and a flexible approach to change management. These had been considered to be key to the successful execution of the Smart Home IoT security project.
Conclusion and Future Works
Smart home IoT security project has been found to be successfully completed while all the objectives as well as goals has been achieved in a comprehensive manner with respect to the smart home environment. System has been found to be effectively ensuring that devices can get registered to the server in a secure manner and it also incorporates remote operations, monitoring, detection, energy management, access control, and software updates. Various platforms have been utilized in order to develop and implement the system infrastructure such as software tools, third party libraries, and project has been able to deliver a secure and user-friendly solution with the help of these platforms as it has been found to enhance the security, convenience and energy efficiency of smart homes.
Future Work
In the future, it might be useful to integrate artificial intelligence technology in order to predict attacks even before they happen without taking much advantage of a system. Moreover, adjusting the devices within the system could help increase user acceptance by expanding its reach regarding internet-of-things (IoT) devices. Additionally, implementation of the blockchain system in place can protect integrity as well as confidentiality during data transmission within an interconnected environment such as IoT.
References
Abdulla, A. I., Abdulraheem, A. S., Salih, A. A., Sadeeq, M. A., Ahmed, A. J., Ferzor, B. M., … & Mohammed, S. I. (2020). Internet of things and smart home security. Technol. Rep. Kansai Univ, 62(5), 2465-2476. https://sciendo.com/pdf/10.2478/cait-2021-0029
Choi, W., Kim, J., Lee, S., & Park, E. (2021). Smart home and internet of things: A bibliometric study. Journal of Cleaner Production, 301, 126908. https://fardapaper.ir/mohavaha/uploads/2021/06/Fardapaper-Smart-home-and-internet-of-things-A-bibliometric-study.pdf
Davis, B. D., Mason, J. C., & Anwar, M. (2020). Vulnerability studies and security postures of IoT devices: A smart home case study. IEEE Internet of Things Journal, 7(10), 10102-10110. https://ieeexplore.ieee.org/ielaam/6488907/9219268/9050664-aam.pdf
Eltresy, N. A., Dardeer, O. M., Al-Habal, A., Elhariri, E., Abotaleb, A. M., Elsheakh, D. N., … & Abdallah, E. A. (2020). Smart home IoT system by using RF energy harvesting. Journal of Sensors, 2020(1), 8828479. https://onlinelibrary.wiley.com/doi/pdf/10.1155/2020/8828479
Gazis, A., & Katsiri, E. (2021). Smart home IoT sensors: Principles and applications a review of low-cost and low-power solutions. International Journal on Engineering Technologies and Informatics, 2(1), 19-23. https://skeenapublishers.com/journal/ijeti/IJETI-02-00007.pdf
Mabodi, K., Yusefi, M., Zandiyan, S., Irankhah, L., & Fotohi, R. (2020). Multi-level trust-based intelligence schema for securing of internet of things (IoT) against security threats using cryptographic authentication. The journal of supercomputing, 76, 7081-7106. https://arxiv.org/pdf/2001.05354
Moedt van Bolhuis, W., Bernsteiner, R., Hall, M., & Fruhling, A. (2023). Enhancing IoT Project Success through Agile Best Practices. ACM Transactions on Internet of Things, 4(1), 1-31. https://dl.acm.org/doi/pdf/10.1145/3568170
Osman, A., Wasicek, A., Köpsell, S., & Strufe, T. (2020). Transparent Microsegmentation in Smart Home {IoT} Networks. In 3rd USENIX Workshop on Hot Topics in Edge Computing (HotEdge 20). https://www.usenix.org/system/files/hotedge20_paper_osman.pdf
Panduman, Y. Y. F., Funabiki, N., Puspitaningayu, P., Kuribayashi, M., Sukaridhoto, S., & Kao, W. C. (2022). Design and implementation of SEMAR IoT server platform with applications. Sensors, 22(17), 6436. https://www.mdpi.com/1424-8220/22/17/6436
Spanos, G., Giannoutakis, K. M., Votis, K., Viaño, B., Augusto-Gonzalez, J., Aivatoglou, G., & Tzovaras, D. (2020, August). A lightweight cyber-security defense framework for smart homes. In 2020 International Conference on INnovations in Intelligent SysTems and Applications (INISTA) (pp. 1-7). IEEE.. https://ieeexplore.ieee.org/abstract/document/9194689/
Tahir, M., Sardaraz, M., Muhammad, S., & Saud Khan, M. (2020). A lightweight authentication and authorization framework for blockchain-enabled IoT network in health-informatics. Sustainability, 12(17), 6960. https://www.mdpi.com/2071-1050/12/17/6960
Touqeer, H., Zaman, S., Amin, R., Hussain, M., Al-Turjman, F., & Bilal, M. (2021). Smart home security: challenges, issues and solutions at different IoT layers. The Journal of Supercomputing, 77(12), 14053-14089. https://www.researchgate.net/profile/Mudassar-Hussain-2/publication/351459297_Smart_home_security_challenges_issues_and_solutions_at_different_IoT_layers/links/6263d2338e6d637bd1f6f177/Smart-home-security-challenges-issues-and-solutions-at-different-IoT-layers.pdf
Wan, Y., Xu, K., Xue, G., & Wang, F. (2020, July). Iotargos: A multi-layer security monitoring system for internet-of-things in smart homes. In IEEE INFOCOM 2020-IEEE Conference on Computer Communications (pp. 874-883). IEEE. https://par.nsf.gov/servlets/purl/10191612
Wan, Y., Xu, K., Xue, G., & Wang, F. (2020, July). Iotargos: A multi-layer security monitoring system for internet-of-things in smart homes. In IEEE INFOCOM 2020-IEEE Conference on Computer Communications (pp. 874-883). IEEE. https://par.nsf.gov/servlets/purl/10191612
Yu, R., Zhang, X., & Zhang, M. (2021, March). Smart home security analysis system based on the internet of things. In 2021 IEEE 2nd International Conference on Big Data, Artificial Intelligence and Internet of Things Engineering (ICBAIE) (pp. 596-599). IEEE. https://ieeexplore.ieee.org/abstract/document/9389849/