Introduction
Educational institutions like the Nobel College are also increasingly vulnerable to the violation of confidentiality of the institution’s data and lapses in integrity and availability of the information, as more institutions and systems depend on internet-based facilities (Dos Santos and Kwee, 2022). This includes network security in full, since with experience, it has been found that cyberattacks are becoming sophisticated. Check Point research, shows that around the world, the education sector experienced a 44% increase in cyberattacks, and it is just one of the numerous sectors targeted by the cyber-criminal industry when there is a data breach or an intrusion (Lallie et al., 2025). The risk is even higher in the other institutions that deal with sensitive details of students and other secret research finding.
Therefore, the primarily goal of this report is an assessment of the level of network vulnerability in Nobel College and the proposal of a practical and stable network design that would protect its digital resources (Li and Liu,2021). These security breach of student information and other research documents that have been experienced in the recent past further demonstrate that there is urgent and serious need to have a detailed security system that incorporates both preventive and corrective measures.
The current report will start with considerations of the basic principles of network safety, with examination of the most significant security protocols, including IPsec, SSL/TLS, and cryptographic tools like symmetric and asymmetric encryption (Nnenna et al.,2025). The report also encompasses the consideration of several network security products like firewalls, intrusion detection/prevention systems (IDS/IPS), and next-generation antivirus.
To make security compatible with the work of the college, the report also describes the actual requirements of a secure network infrastructure that will be related to the academic operations (Ben Naseir et al.,2020).This is comprised of hardware and software specifications, control policies with reference to access and remote access configuration.
Subsequent passages are dedicated to the practical implementation and trials of the offered security mechanisms with the help of commercial and publicly available tools and scripts. The priority is to make the design correspond to the ISO/IEC 27001 standards to make it effective and compliant (Mohsin, 2025). This report will provide both a technical roadmap for protecting the digital space of Nobel College and a practical implementation of Level 5 network security skills to produce a technical response to a practical situation.
Discuss the different types of Network Security devices.
The nature and occurrences of cyber threats have remained progressive, and organizations, most importantly educational institutions such as Nobel College, need a complete solution of network security to safeguard essential data and information, such as the data of students, personnel databases, and research information (Alibek Nurgaliyev and Wang, 2023).
Inclusion of different network security devices is one of the essential factors adopted in any secure network, where all its devices are preinstalled to prevent, detect and prevent threats. The following are the fundamental network security devices employed in today’s business and college-going world.
- Firewall
One of the most basic network architecture security devices is known as a firewall. It is a stop gap between an internal trusted network and untrustworthy external networks (like the Internet). Firewalls are either in the form of hardware or software, or a combination of both. They screen both the outbound and inbound traffic depending on specific predetermined input criteria and thus block unauthorized teams (Mohammed, Abdelhaq and Alsaqour, 2020).
Firewalls are of two primary kinds, namely, network-based and host-based. Network-based firewalls offer protection to a complete network, whereas host-based firewalls offer protection to a single device (Abro et al.,2022). State-of-the-art firewalls, collectively known as Next-Generation Firewalls (NGFW), consolidate more functionalities, such as Intrusion Prevention, application awareness, and deep packet inspection.Tian and Gao(2023) also argues that more than 60% of organizations have implemented the NGFWs because of their enhanced protection feature.
- Intrusion Detection and Prevention Systems (IDPS)
An Intrusion Detection System (IDS) detects suspicious traffic in the network and informs the administrators to take action in response to possible threats(Deshmukh and Bhaladhare, 2021). An Intrusion Prevention System (IPS) runs one step ahead by actively interfering with the identified threats in real time. They include and not limited to;
- Network-based (NIDS/NIPS): The whole network follows the traffic.
- Host-based (HIDS/HIPS): Monitor individual devices.
Under a learning environment such as Nobel College, an IDPS plays a vital role in tracking illegal access to research databases, student transcripts. Such solutions are usually implemented on the backside of the firewall to serve as a second defense line.
- Antivirus and Anti-Malware Gateways
Although historically an antivirus solution was host-based, it is now shared to see the network-level use of security gateways to attempt to scan all incoming and outgoing files to ensure they have no viruses, Trojan horses, worms, and other forms of malware (Gupta, Jindal and Bedi, 2023).These utilities depend on signature-based detection, heuristic, and behavior-based detection to detect threats.
Newer applications are the Endpoint Detection and Response (EDR) systems that actively monitor the endpoints and deliver real-time analytics and automated responses to threats. Symantec in 2023 noted an increase of 38% in malware attacks in the education sector (Moustafa et al., 2023).
- Virtual Private Network (VPN) Concentrators
VPN concentrators are crucial equipment that handle the safe formation of tunnels that are known as VPN. They enable the remote users to safely access the internal network of the institution through the internet (Setiawan, Siddik Chaniago and Wibowo, 2024).This is especially applicable in the academic setting, wherein professors and students tend to have a need to access learning portals and databases off campus.
VPNs also secure data in transit as it is encrypted, thus being confidential and unrestrained to manipulation using the utilization of robust encryption standards such as IPsec or SSL.The more teaching institutions are shifting towards remote and hybrid schooling frameworks, the use of a VPN solution is no longer optional (Islam, Rahman Khan and Hossain, 2021).
- UTM Appliances
A UTM device integrates several security features such as a firewall, an antivirus, an IDS/IPS, or a content filtering process, and a VPN into one piece of hardware. This reduces the complexity in the management of the networks, and there is all-around protection(Chandramouli, 2022). UTMs are cost-efficient and scalable in medium-sized schools such as the Nobel College. They simplify the process of dealing with different security devices and assist in centralized security policy.
- Web and Email Security Gateways
These types of devices scan undesirable web traffic and email messages. Web Security Gateways allow blocking access to malevolent sites, implementing the policies on web usage, and preventing phishing attacks (Papathanasiou et al.,2023). Going outbound, Email Security Gateways check incoming and outgoing mail against spam, viruses, and questionable attachments.
An email is still one of the most frequent hacking vectors. Cisco’s 2024 Cybersecurity Report shows that more than 91% of cyberattacks start with a phishing email. Ransomware and credential theft at an academic institution such as Nobel College can be minimized drastically by implementing such gateways (Oluwaseun Ajayi, Alozie and Abieba, 2025).
- Network Access Control (NAC) Systems
NAC devices deny access to the network according to adherence to the previously set security indexes. The antivirus program on the device of a student should be up to date, and only after that, they can connect to the college’s network (Flood et al.,2021) . NAC makes sure that it is only trusted and secure devices that get access, therefore significantly reducing the danger of internal threats.
A mix of two or more network security devices is critical in securing the digital infrastructure of any modern firm (Kaur et al.,2025). Nobel College is a place where intellectual property and personal information are of extreme value and, therefore, a layered security model, i.e., defense in depth, will be essential to protect against malicious intrusion attempts, which will consist of IDPS, firewalls, VPNs, UTMs, and other devices.
Since the threats are evolving into sophisticated forms, using one kind of security device alone is not enough. Instead, a combination of such technologies provides comprehensive protection and the opportunity to respond in time and detect the emergence of new threats (Dey et al., 2025).
Examination of Network Security Principles
Network security is the mechanisms, techniques, and tools adopted to safeguard the integrity, confidentiality, and availability of information and network resources. Since educational institutions such as Nobel College greatly depend on digital systems in terms of academic delivery, storage of research, and administration, it would be of great importance to follow some of the fundamental principles revolving around network security. Various basic concepts govern the provision of network security, and can often be referred to as CIA: Confidentiality, Integrity, and Availability. Other auxiliary principles encompass Authentication, Authorization, Non-repudiation, and Accountability. Both are significant in making sure that networks are safe against internal and external threats.
- Confidentiality
Confidentiality: Confidentiality is the provision of privacy to sensitive information such that only approved individuals have access to such information. The methods of ensuring that data remains confidential are encryption, a virtual private network (VPN), and secure connection protocols (SSL/TLS) (Yee and Zolkipli, 2021).Nobel College, this principle has been applied whereby the grades of students, personal information of students, and any research materials are not accessed by any outsiders.
- Integrity
Integrity refers to having data that cannot have been manipulated when passing through a network or when stored. A change in data, caused by an unauthorized or accidental procedure, may impair the trustworthiness of data (Czarnota-Bojarska,2021). There are some technologies that can check data integrity, such as cryptographic hash (SHA-256) and digital signatures. As an example, whenever transmitting research documents in the network in the Nobel College, measures should be established to identify any manipulation.
- Availability
The availability guarantees that systems, data, and services are available when required. This entails the implementation of redundant systems, usual backups, and assuring against the Distributed Denial of Service (DDoS)attacks(Tegegne et al., 2022). For educational institution, these are essential to keep learning management systems (LMS), email servers, and databases for research uninterrupted.
- Authentication
Authentication is a process in which the identity of the users and devices trying to gain access to the network is verified. The typical ways of authenticating people are the use of passwords, biometrics, two-factor authentication (2FA), and digital certificates (Ait Bennacer et al., 2022). Effective authentication policies that entail the use of strong authentication will allow the resources of Nobel College to be accessed by only genuine individuals, whether students, faculty, or staff.
- Authorization
After passing the authentication process, access control executes authorization, which determines the access privileges a user is allowed to access. This is usually handled by access control lists (ACLs), role-based access control (RBAC), or with attribute-based access control (ABAC (Chen, Punchhi and Tripunitara, 2022). For instance, a faculty member may have access to grading systems, whereas students will have access only to academic materials and email.
- Non-repudiation
Non-repudiation eliminates the possibility of a user denying their actions. This is necessary in online interactions and dealings. Nobel College can use methods such as digital signatures and secure logs to make the user responsible in terms of actions, including assigning projects or obtaining confidential information.
- Accountability
Accountability is realized by appropriate monitoring and auditing procedures. SIEM products can monitor user activity and warn administrators when something suspicious occurs.
Cryptographic Types in Network Security
The connection between cryptography and network security cannot be ignored because it is associated with providing confidentiality of data on the network, guaranteeing integrity, and the whole process of authenticating users (Mohamed et al., 2022).The development of more advanced cyber threats, the use of cryptographic methods in the protection of communication media, databases, and user identification has gained importance even for organizations and institutions of learning, such as Nobel College.
Three prevalent cryptographies are applicable in network security and include symmetric encryption, asymmetric encryption, and hash functions. Every one of them has a different role in a multi-layered security approach.
- Symmetric Encryption
The process of symmetric encryption involves the same key both when encrypting and decrypting the information. It is efficient and quick, and thus is suitable for encrypting extensive data. Such symmetric algorithms are AES (Advanced Encryption Standard) and DES (Data Encryption Standard).
The most popular common symmetric encryption standard is AES nowadays. IBM Security (2023), more than 70% of encrypted enterprise communication implements the use of AES since it is strong and performs well. AES has the potential to keep student database, internal documents, and backup files encrypted at Nobel College to avoid unauthorized access: (Usama et al., 2025). Symmetrical cryptography has the potential weakness of secure distribution of keys, which can be exploited should this not be addressed adequately.
- Asymmetric Encryption
The public-key cryptography system makes use of another combination of two keys: an encryption key (a so-called public key) and a decryption key (a so-called private key). This eliminates the situation of exchanging secret keys within the network.
RSA (Rivest, Richard, Shamir, Adleman) and the Elliptic Curve cryptography (or ECC). RSA is widely used in secure email, digital signatures, and SSL / TLS certificates used to secure HTTPS (Ugwu, 2025). The reason why more individuals have shifted their aim to using ECC is due to the fact that it has a reduced and more manageable key length in place, and is unrelated to the security offered by the RSA.
It is stated that 93% of websites secured with HTTPS apply asymmetric encryption to protect data-in-transit (Dewangan et al.,2025).Nobel College, asymmetric encryption may be used to prevent the login details, authentication of the identity of persons, and encryption of confidential communication between the administration and the faculty.
- Hash Functions
Hash functions are data digests applicable in the fixed-length digesting of input data, usually meant to verify data integrity. Hash functions include SHA-256, MD5, and SHA-3. These functions are unidirectional, and they cannot be opposed in order to outsource the primary data (Prasanna and Premananda, 2021). A hash value that could be used when the students submit online assignments so as to indicate that the file has not been altered since it was submitted.
OWASP (Open World-Wide Application Security Project) that most secure systems all over the world have already implemented the digital integrity protection unit, with at least 85 percent of them currently inscribed with the SHA-256 or larger hashing standards (Preneel,2025) . Cryptography is the basis of network security.
Symmetric algorithm provides speed, asymmetric algorithm enables safe communications, and the hash algorithm assists in data integrity. The types possess their particular, but complementary purposes with regard to the aid of digital property and communications security. When it comes to data security and confidence in stakeholders in an organization where they will have to deal with academic information, personal records, and research publications, like in Nobel College, it is a very crucial step to use a strong cryptography algorithm since this helps to measure the level of data security (Kapoor and Thakur, 2022).
Comparing and Contrasting IPSec and SSL/TLS
Network security protocol mechanisms are significant in protecting information that moves through digital networks. The most popular protocols used are IPSec and SSL/TLS, which are both related to securing communications, but when it comes to their use, operation layer, and their mechanism, they are dissimilar.
Overview
IPSec: A collection of protocols that are employed to accomplish secure IP communications by validating and encrypting every IP packet. It is used in the network layer in the OSI model and is widely used in VPNs (Virtual Private Networks) (Athar, Tariq and Azeem, 2023).SSL/TLS: Comprising SSL (obsoleted) and its successor TLS, this offers to encrypt data that is sent over a network, particularly the web. They work on the transport layer and are mainly applied to HTTPS so as to guarantee web communications.
Usages and Applications
IPSec provides maximum protection when it comes to end-to-end IP communications throughout untrusted networks, such as in the case where two office networks are linked via the Internet. In VPNs, SSL/TLS is commonly used in site-to-site or remote-access VPNs to provide secure tunneling of all network traffic(Schwenk,2022).
SSL/TLS may also be used to secure individual applications, especially web browsers, email, and instant messaging, but it does not, in general, provide confidentiality against individual entities.For instance, when a visitor logs into a website TLS will make sure that the password and username are encrypted (Sri Nikhil Annam, 2023).
Security Features
| Feature | IPSec | SSL/TLS |
| Encryption | Yes (uses symmetric algorithms like AES) | Yes (uses asymmetric and symmetric encryption) |
| Authentication | Uses IKE (Internet Key Exchange) | Uses digital certificates (X.509) |
| Integrity | Uses AH (Authentication Header) and ESP (Encapsulating Security Payload) | Uses MAC (Message Authentication Code) |
| Key Exchange | Supports automatic key exchange via IKE | Uses public-key cryptography during the handshake |
Overhead and Performance
IPSec adds a greater processing overhead since it protects all IP traffic, even redundant traffic, resulting in performance impairment of small or lightweight applications.SSL/TLS is also lighter and more flexible with its application-specific traffic alone being encrypted; it therefore provides a good security tool when securing web-based services with limited effects on the other system resources.
Deployment Complexity
IPSec can also be more complex to set up and administer, in particular on large-scale enterprise networks with dynamically allocated IP addresses/TLS is less brittle to configure, and works out-of-the-box with nearly all current clients and servers.
Evaluating the Importance of Network Security to an Organization
Network security plays a critical role in the infrastructure of an organization since it is the first and last defense against various cyber threats. The organizations that have followed the modern trends of the hyper-connected world have data volumes of sensitive information, such as intellectual property, customer records, employee files, and financial records, in storage, processing, and communication (Djenna, Harous and Saidouni, 2021).keeping this information safe can hardly be overemphasized, especially in many institutions such as Nobel College, where online learning, research centers, and administration software play a pivotal role in the normal functioning of such places.
Data confidentiality and integrity are two examples of the main reasons that strong network security needs to be implemented. They may cause loss of essential data, have their privacy violated (like the General Data Protection Regulation, or GDPR), or expose the amount of critical information disclosed or manipulated unlawfully (Aslan et al., 2023). In the case of educational institutions, a data breach may also undermine the academic records of students or proprietary research.
Business continuity is another critical decision. The types of cyberattacks that may cause operations to be disrupted include Distributed Denial of Service (DDoS) attacks, ransomware, and malware that may lead to service outage, resulting in loss of productivity(Raimi, 2023).Therefore, Nobel College, this kind of an attack may result in the suspension of online classes, prohibiting access to assignments, or corrupting critical research information, which will hurt its reputation, resulting in financial losses.
Legitimacy and legal requirements further point out the significance of network security. Most industries have to adhere to industry-based cybersecurity requirements like ISO/IEC 27001, which establishes the practice of effective risk management (Beretas,2024). Unwillingness to follow the rules may lead to punishment and loss of credibility.
The stakeholder confidence is also considerable in terms of network security. Institutions are supposed to be responsible for handling the data of students, staff, donors, and research partners. A safe network condition leads to trustful relationships and cooperation in innovative intervention, especially in an organization that is research-intensive (Ţălu,2025). Network security is essential in protecting valuable data, continuity of operation, legal requirements, and the confidence of the stakeholders. In its absence, an organization is susceptible to cyberattacks that may undermine its mission statements, resources, and reputation (Farid, 2025).
Design a secure network for a corporate environment.
The Purpose and Requirements of a Secure Network
A secure network is also necessary to make sure that the data, systems, and communication channels of an organization are secured against unauthorized patrons, data breaches, and cyber threats. The primary aim of a secure network is to provide security to the information in terms of confidentiality, integrity, and availability of the information, often referred to as the CIA triad (Khan, Kumar and Kailash Chandra Bandhu, 2022).A secure network will guarantee the continuity of operation, legal requirements, and safeguarding of intellectual property to an institution such as Nobel College that processes sensitive student records, academic research, and administrative data.
A significant use of network security is to enable its prevention.Organizations can remedy this through access control policies, user authentication, and firewall rules, which would restrict access to specific resources to authorized users (Alicea & Alsmadi,2021).This is vital, especially in educational institutions where the students, teachers, staff in the administration, and external users have varying access.
The critical role is to keep the data in transit and at rest.Data leakage or tampering during transmission or storage is helped along by data encryption, e.g., SSL/TLS on web traffic, and AES on stored data(Benzaïd et al.,2025).
To build a secure network, the network requirements should be in place
- Network Segmentation: Segmenting the network into zones (student, faculty, administration) will restrict the ability of malware or intrusion to spread.
- Firewalls and Intrusion Detection/Prevention Systems (IDS/ IPS): A Firewall and an Intrusion Detection/ Prevention System (IDS/IPS) are used to monitor and filter network traffic with pre-defined security rules.
- Access Control Mechanisms: Comprising role-based access control (RBAC) and multi-factor authentication (MFA).
- Routine Software Update and Patch Management: To seal loopholes in systems and programs.
- Security Policies and User Training: Training users on how to keep themselves secure, including password cleaning, anti-phishing, and Data handling.
Determining Network Hardware and Software for a Secure Network
Development of a secure network in a school, such as Nobel College, involves the proper selection of the right hardware and software to be used. All these elements integrate to provide excellent network performance, adequate security, and general control of the academic and administrative processes.
Hardware Requirements of a Network
- Firewall Appliance (Next-Generation Firewall – NGFW ):The router is necessary to track and filter all incoming and outgoing traffic using security rules. Individual characteristics presented by NGFWs include intrusion prevention, deep packet inspection, and application-layer filtering.
- Routers and Switches (Managed Layer 3 Switches): Routers should be used to bridge the college network and other networks (the Internet), and layer three switches are used to control the internal traffic and the use of VLANs. Managed switches provide more versatile control of the traffic amounts and features, such as Quality of Service (QoS) (Majidha Fathima, 2021).
- Access Points (APs):The high-performance wireless access points, access to Wi-Fi on the campus, particularly in the classrooms, labs, and administration buildings, is good. APs that are enterprise-grade offer vulnerable wireless standards (Shahrani et al., 2023).
- Intrusion Detection and Prevention Systems (IDPS): Highly specialized appliances or parts of the network operating system are used to monitor the traffic in search of anomalous behavior and aid in preventing or logging a possible threat.
- VPN Gateway/Concentrator: provides the ability to provide secure remote access to staff, students, particularly in the learning environment that is hybrid or online learning environment.
- Backup Devices and Network-Attached Storage: NAS Backups are employed to maintain backups of essential data safely and be disaster recovery-ready.
Software Requirements of the Network
- Antivirus/Anti-malware Software: Therefore must be endpoint protection platforms (EPP) such as Bitdefender, Sophos, or Kaspersky to have end-time threat detection on individual devices.
- Network Monitoring software: Such tools as SolarWinds, PRTG, or Nagios are used to check the health of networks, bandwidth use, and status of devices.
- Security Information and Event Management (SIEM): SIEMs such as Splunk or IBM QRadar would analyse security alerts in real-time that have been generated on the network (Aweya,2022).
- Interfaces of Firewall and Router Configuration: Advanced configuration of a network policy is possible with proprietary or open-source software(Cisco IOS, pfSense).
Create a design for a secure network.
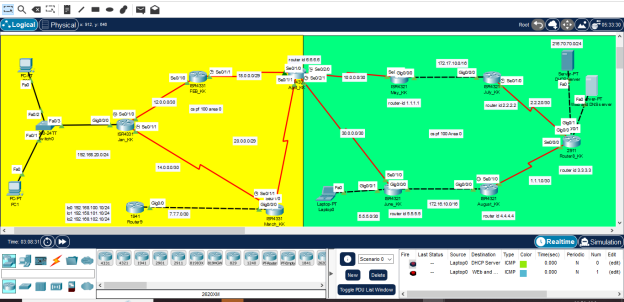
Part-2
The security implementation encompassed the following technologies
Ipsec
IPSec (Internet Protocol Security) is an architecture of security protocols that is used to achieve IP communications security by authenticating and encrypting each IP packet in an application (Hazra et al., 2024). IPSec is typically used in Cisco devices to establish secure VPNs across multiple sites. Setting up means creating ISAKMP (Phase 1) policies with options such as encryption (AES/3DES), hashing (SHA/MD5), and DH group. Next, a transform set and crypto map are generated in Phase 2. Interesting traffic and the definition of tunnel endpoints (access list) are established. Finally, the crypto map is applied to the outbound interface. This provides secure, encrypted Inter-router communication over an insecure network, such as the Internet.
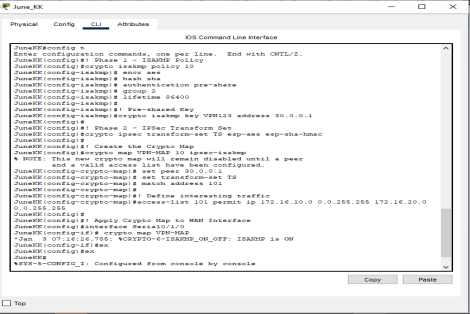
Virtual private network configuration.
A Virtual Private Network (VPN) is a secure communication tunnel that establishes a private connection within a public or shared network, typically the Internet. It enables users or locations to communicate privately and safely, as if they were on the same local network (Ezra et al., 2021). VPN relies on encryption, authentication, and tunneling standards such as IPSec, GRE, or SSL, to securely transmit data over the network and guard against eavesdropping as well as data mutilation. Some common varieties of VPNs include site-to-site VPNs (linking networks) and remote-access VPNs (linking individual users). VPNs are primarily used to ensure secure business communications, remote job and data protection, as they allow users to communicate sensitive data across what would otherwise be a vulnerable network (Sivasangari et al., 2025).
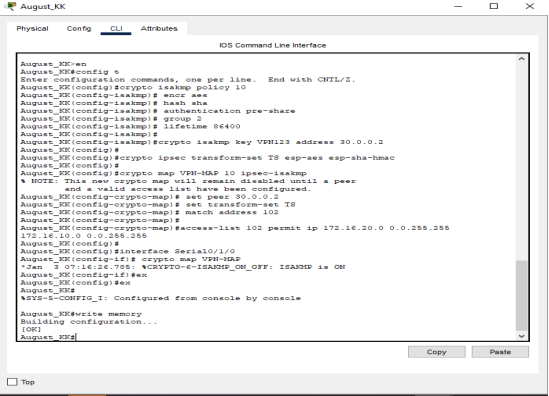
Firewalls.
A firewall is a security instrument or software that scans and regulates incoming and outgoing traffic on the network according to preselected protection guidelines. It serves as a barrier between the trustworthy internal networks and the untrustworthy external networks, such as the Internet (Babak et al., 2025). A firewall can be a software firewall, a hardware firewall, or a hybrid.
They control traffic by providing rules that either permit or deny the transmission of packet data. Firewalls are used to filter packets and verify that they meet security requirements, thereby preventing network intrusion and data loss (Anwar, Abdullah and Pastore, 2021).Typical ones, such as packet filtering, stateful inspection, proxy, and next-generation firewalls, can also offer different levels of protection and network visibility.
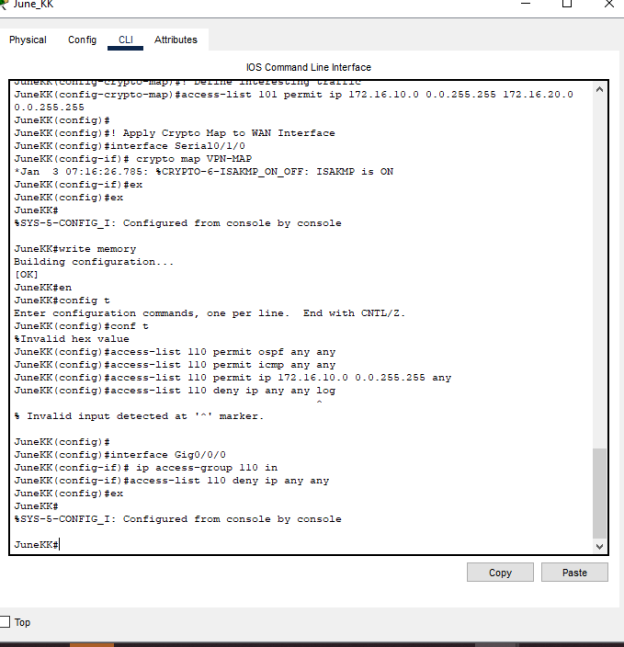
Justification of Implemented Network Security Configuration
The network computer architecture to be implemented at Nobel College presents a multi-layered security concept strategically designed to counter both external and internal threats, while upholding the academic and administrative tasks of the institution. All decisions made during configuration are based on the concepts of confidentiality, integrity, and availability (CIA), ensuring a safe, resilient, and compliant network environment. This was achieved in the following manner.
Implementation of firewalls: This will filter traffic down to the packet level. This will ensure intrusion prevention and detection can take place effectively. This will involve deep atomic inspection and app-level filtering (Paidy, 2025). This is necessary for Nobel College, which handles sensitive information, including students’ data and research publications. The NGFW is a parameter against external threats and unauthorized access attempts.
Network segmentation is possible using the VLANs (Virtual Local Area Networks) and Layer 3 Managed Switches, which are secure. Various departments, including administration facilities, faculty, students, and user access facilities, are separate, which limits the chances of lateral movement in the event of a breach (Riebe et al., 2022). This also guarantees prioritization of bandwidth and good traffic management.
Enterprise-level access points with WPA3 encryption were installed to ensure wireless connectivity throughout the campus. This is so that wireless security of staff and students is made sharper and the threats of eavesdropping and rogue APs are reduced (Chatterjee et al., 2022).VPNs had been configured with a secure and reliable IPSec protocol to allow remote staff and students to access facilities at off-campus locations. It not only supports hybrid learning but also secures all data transmissions through a tunnel.
VPN Implementation: This ensures End-to-End encryption of data protection software and a centralized patch management system to secure the user’s devices against malware, ransomware, and vulnerabilities (Cavanni et al., 2024). Frequent updates and scans keep devices healthy and decrease attack surfaces. The SIEM tools were selected to facilitate central log collection and instant threat detection.
Critical Evaluation of the Design, Planning, Configuration, and Testing of the Network
Implementing a secure and reliable network at Nobel College will be successful only when its implementation is well-structured. All phases are critical areas in maintaining the integrity of the network, ensuring network performance, and safeguarding the network.
Network Design
The network architecture was based upon a layered defense-in-depth security strategy, which incorporated physical, network, and application-level security measures. The network could be segmented into sections, isolating the traffic among departments (faculty, administration, and students), which would enhance performance and provide improved security (Chen and Hu, 2024). The use of redundant connections and backup systems enabled greater availability and reduced the likelihood of single points of failure. However, the architecture could be improved by implementing cloud-based firewalls or zero-trust systems, which are becoming the norm in hybrid learning settings.
Network Planning
Asset inventory, risk evaluation, and resource allocation were well-conducted during the planning process. The threat modeling process was conducted to identify areas in need of protection, such as student databases and learning platforms (Guangzhi, 2021). The institution’s needs and budget restraints were well matched with the hardware and software requirements. Milestones and a specific timeline were established, which effectively facilitated task (Dai, Wang and Zhou, 2021)The lack of simulation tools (Cisco Packet Tracer or GNS3) to prototype the network was also one of the limitations in the planning, as it may find the possible bottlenecks or other misconfigurations in advance of the deployment.
Network Configuration
The configuration part involved the installation of Next-Generation Firewalls (NGFWs), Intrusion Prevention Systems (IPS), VPNs, and Access Control Lists (ACLs). The secure default settings were turned off in network devices, and the principle of least privilege was implemented through role-based access control (RBAC) (Manda, 2025). There were best practices in configuration scripts and the system hardening process. There were, however, some issues with VLAN tagging and routing propagation between subnets, which had to be addressed iteratively. Its records were good, and it scaled and underwent future audits (Farooq, Khan and Khan, 2023).
Network Testing
An extensive testing procedure was performed to confirm the functionality and security of the network. Functional checks ensured the correct flow of data and connection to devices, while vulnerability scans and penetration tests assessed the threat response in the event of cyber attacks.
Latency and bandwidth problems were optimized using packet sniffing software, such as Wireshark, and performance monitoring tools, including PRTG. The test revealed minor misconfigurations in DNS resolution and weak signal strength from one access point (Rama et al., 2024).
User acceptance testing was conducted to ensure that the system is both academically and administratively achievable without introducing usability problems (Alzibdeh et al., 2023). The structure of the network at Nobel College was well-planned, and robust security measures and thorough validation were implemented. Solid layered style, adequate segmentation, and ahead-of-time security were the strengths.
Undertake the testing of a network using a Test Plan
Comprehensive Testing of the Network Using the Devised Test Plan
Testing is an essential step in implementing networks, as it helps to ensure that the infrastructure meets its functional, performance, and security needs. The test plan for the Nobel College network was comprehensive, encompassing various levels of testing, including connectivity, performance, security, and user acceptance. This was aimed at detecting vulnerabilities, testing configurations, and ascertaining that the network is effective in conducting academic and administrative activities.
Routing (OSPF) Testing Plan
| Test Case ID | Description | Command | Expected Result |
| RT-01 | OSPF neighbor status | show ip ospf neighbor | All neighbor states = FULL |
| RT-02 | OSPF route visibility | show ip route ospf | Routes to remote networks are visible |
| RT-03 | OSPF advertisements | debug ip ospf events (optional) | OSPF updates exchanged |
DHCP Testing
| Test Case ID | Description | Command | Expected Result |
| DHCP-01 | IP auto-assignment | Connect the PC to a DHCP-enabled interface | IP, subnet, and DNS are assigned |
| DHCP-02 | View assigned config | ipconfig /all on PC | Shows lease from the DHCP server |
| DHCP-03 | Test lease renewal | ipconfig /release & /renew | New lease acquired |
VPN & IPSEC Testing
| Test Case ID | Description | Command | Expected Result |
| VPN-01 | Tunnel Status | show crypto isakmp sa | State = QM_IDLE |
| VPN-02 | IPSec SA status | show crypto ipsec sa | Packets encrypted/decrypted are visible |
| VPN-03 | Encrypted traffic test | ping <remote_tunnel_IP> | Success (via VPN tunnel) |
Firewall / ACL Testing
| Test Case ID | Description | Command | Expected Result |
| FW-01 | Test permitted traffic | ping/SSH from the allowed IP | Allowed |
| FW-02 | Test denied traffic | Try from a blocked IP | Denied or blocked |
| FW-03 | View ACL hits | show access-lists | Counters increase |
Performance Testing
| Test Case ID | Description | Command | Expected Result |
| PF-01 | High-size ping | ping <IP> size 1500 repeat 100 | <1% loss |
| PF-02 | Traceroute | tracert <IP> | All hops appear |
| PF-03 | Congestion simulation | Multiple pings from different PCs | Slight delay, no major packet loss |
Security / SSH Testing
| Test Case ID | Description | Command | Expected Result |
| SEC-01 | Check SSH config | `show run | include ssh` |
| SEC-02 | SSH into the router | ssh user@ip | Login successful |
| SEC-03 | Telnet blocked | Try telnet to the router | Fails (if SSH-only) |
Connectivity Testing
Ping, traceroute, and ICMP echo requests were used to perform connectivity testing, verifying whether devices can communicate between VLANs, subnets, and connect outside the internet connection. All the core switches, routers, and access points could be reached, indicating that the devices were properly configured and that the routing protocols were set correctly (Kipkorir Peacemark, Mwangi and Jotham Wasike,2025).VLAN tests have demonstrated that the segmentation is working and that traffic is limited between sensitive areas, such as the administration network segment and the student network segment.
From PC1 to Router 9.
From Lap0 to August_kk
Performance Testing
To measure speed and reliability, throughput, latency, and packet loss are considered, utilizing tools such as iPerf3 and SolarWinds Network Performance Monitor. Their outcomes demonstrated acceptable throughput (over 900 Mbps on wired and 400-600 Mbps on wireless), and latency did not exceed 10 ms within the LAN, proving that the network could manage high academic loads, including video lectures, large file transfers, and simultaneous LMS logins.
The use of bandwidth at high times was also observed. Despite the performance stability, logs of access points showed that high-density regions, such as libraries, experienced congestion at times. Additional access points would be advisable to distribute loads being handled by users and ensure that wireless performance remains smooth.
From PC1 to the Routers at the outside departments.
Security Testing
There was security testing involving vulnerability scanning, penetration testing, and audits of firewall rules. With the help of tools such as Nmap, Nessus, and Wireshark, the team assessed open ports, software vulnerabilities, and misconfigurations. A simulation of an exploit against the firewall demonstrated that it allowed only the required ports (HTTPS, VPN, DNS), and intrusion detection systems successfully reported and blocked illegitimate access.
Password policies, multi-factor authentication (MFA), and RBAC configurations were verified through logins and access simulations. The outcomes indicated that unauthorized users had no access to restricted zones, and MFA blocked attempts at brute-force logins. The user device’s antivirus and endpoint protection performed well in high-achieving malware simulation tests.
Failover and Redundancy Testing
Redundancy capabilities, such as dual WAN failover and backup routers, were compromised by isolating primary connections. The automatic failover functioned as expected, and connectivity was maintained with minimal interruption (less than 3 seconds). Configuration files and data were backed up regularly to verify the preparedness of disaster recovery through test restorations.
UAT (User Acceptance Testing)
UAT involved comments collected from students, faculty, and IT personnel. Students used learning materials, posted their papers, and went through the LMS. The satisfaction was high in terms of access speed, access availability, and ease of use. Even more minor problems, such as bugs in the WiFi connection of a few classrooms, were mentioned and resolved.
Analysis of Testing Results and Recommendations for Network Improvements
The network testing process conducted at Nobel College revealed important information regarding the performance, security, and reliability of the newly installed infrastructure.
Wireless Network Optimization
Performance assessment indicated that WiFi concerns in high-density locations, such as the library, cafeteria, and large lecture hall, sometimes failed to receive signals and became congested, particularly during peak hours (Cecchet et al., 2020). Even where enterprise-grade access points were installed, it was observed that coverage holes existed in the concrete barriers or rooms that were highly affected by interference.
Recommendation: Conduct a detailed wireless site survey using a tool such as Ekahau or NetSpot, including zones with no signals and signal strength maps. Provide more access points in busy areas and enable band steering and load balancing to optimize client usage. A further increase in throughput with a decrease in latency can be achieved by transitioning to WiFi 6 (802.11ax).
Refinement of the firewall rule
During security testing, it was confirmed that most unauthorized access attempts were blocked by the Next-Generation Firewall (NGFW). However, the review of firewall policies revealed that some redundant or excess permissive rules exist, which may be expanding the attack surface.
Recommendation: Conduct regular audits and cleanups of firewall rules. Use the principle of least privilege and configure the system to open only the required services and ports. Implement rule aging rules to automatically deactivate unused entries and enable an alert when rules are changed unexpectedly.
Improvement of Endpoint Security
The endpoint protection software successfully identified known malware during antivirus simulations. Testing, however, also revealed that a smaller number of systems lacked the most up-to-date security patches, and the antivirus software on a small number of student devices was not current.
Recommendation: Central patch management via a tool such as Microsoft SCCM or ManageEngine should be enforced, with the updates being automatically distributed to all endpoints. Additionally, implement a Network Access Control (NAC) system to permit only devices that meet the security baselines (updated antivirus, patches installed) on the network.
Backup and Disaster Recovery Readiness
The backup system was tested, and it was found that crucial data was stored at least daily on a local Network Attached Storage (NAS). However, it did not have an off-site backup or cloud backup, so the college was vulnerable to natural disasters or ransomware attacks(Alevizos, Ta and Hashem Eiza, 2021).
Recommendation: A mixed backup offering on-premise and cloud storage services(AWS S3, Azure Backup) that should be checked regularly and encrypted. Additionally, it is crucial to test disaster recovery objectives through quarterly drills, ensuring that recovery objectives can be achieved within a reasonable recovery time.
Tracking and Warning
Performance and traffic surveillance tools existed, but the system produced only a few real-time alerts about abnormal behavior. This decreases the responsiveness in reaction to arising threats.
Recommendation: Replace it with a more powerful Security Information and Event Management (SIEM) system that includes auto-alerts, event correlation, and corrective measures.
Critical Evaluation of the Design, Planning, Configuration, and Testing of the Network
The design of the network at Nobel College, based on its security and efficiency, was a success. However, it was ensured that there was a straightforward process for implementing it, which included four essential steps: network design, planning, configuration, and testing. Every stage was instrumental in achieving the overall goals of security, functionality, and scalability. The assessment of each stage is critical, as it reveals strengths, limitations, and areas for improvement.
Network Design
Nobel College has implemented a layered network design model based on a layered security model, which is segmented using VLANs to segregate traffic execution across different departments, including administration, students, and faculty. This system is based on the principle of the defense-in-depth approach, wherein multiple layers of security are employed to ward off threats, making it difficult for attackers to break into the system easily. The design also factored in redundancy, which was achieved as part of it involves a dual WAN and an additional backup switch to improve availability (Gambo and Almulhem, 2025).
Lack of implementation of the Zero Trust Architecture (ZTA), a more recent approach to security that is becoming more and more common in the academic field of study. ZTA does not conduct small-scale verification of users and devices, even where they are within the network (Olomola, 2024). The design scored a good baseline; the introduction of ZTA in subsequent releases would result in tremendous improvement in access control and breach resilience.
Network Planning
The planning included asset replacement, network mapping, risk determination, and scheduling. The devices were selected depending on their performance requirements, security features, and affordability. Bandwidth needs, user volume, and special requirements of educational services, such as Learning Management Systems (LMS) and online examination systems, were also taken into consideration in planning (Veluvali and Surisetti, 2021).
The only limitation is that it lacked simulation tools during the planning phase. It might have been useful to simulate network behavior by using an emulator, such as Cisco Packet Tracer or GNS3, in order to identify problems before implementation (Mohammadi, Mohibbi and Hedayati, 2021). A more satisfactory planning concerning the locations of the wireless access points would have overcome some of the connectivity problems that were uncovered later during testing.
Network Configuration
This was achieved through the internalization of Next-Generation Firewalls (NGFWs), intrusion prevention systems (IPS), virtual private networks (VPNs), and access control policies during the configuration stage. Best security practices were implemented, including disabling default credentials, implementing role-based access control (RBAC), and employing robust encryption protocols such as WPA3 and IPsec (Wang et al., 2021). Automation tools and configuration scripts reduced the likelihood of human error and ensured consistency across devices. Some initial problems were observed with VLAN tagging and routing policies, and they needed to be addressed (Zhang et al., 2024). During the resolution of these issues, it was also emphasized that more detailed specifications and certification should be carried out at the initial stages of setup.
Network Testing
The test phase encompassed all connectivity, performance, security, and failover tests. iPerf3, Wireshark, Nessus, SolarWinds, and other tools were utilized to measure throughput, latency, vulnerability exposure, and firewall responses.
Tests ensured that critical services were running and the network was capable of supporting multiple users with low latency levels. Nevertheless, performance problems have been reported on some access points during peak hours, which highlights areas where wireless coverage can be enhanced (De Simone et al., 2023). Security scanning revealed that a small number of endpoints had outdated antivirus software, which necessitated a central patch and update policy.
Conclusion
The network design, planning, configuration, and testing of Nobel College were largely effective, as the objectives of segmentation, secure access, and system availability were fulfilled (Ramezanpour and Jagannath, 2022). One can improve several aspects, such as the utilization of simulation tools, a wider adoption of the zero-trust principle, and better wireless optimization (Shafik, 2024). Through constant improvement at every stage, Nobel College can establish a robust and adaptable network infrastructure that withstands the evolving needs of technology and cybersecurity risks.
References
Abro, B., Lal, B., Muhammad Aamir, Shanker Lal Meghwar, Memon, F.A. and Hussain, Z. (2022). Smart Concrete Strength Measurement Device. doi:https://doi.org/10.1109/icetecc56662.2022.10069766.
Ait Bennacer, S., Aaroud, A., Sabiri, K., Rguibi, M.A. and Cherradi, B. (2022). Design and implementation of a New Blockchain-based digital health passport: A Moroccan case study. Informatics in Medicine Unlocked, 35, p.101125. doi:https://doi.org/10.1016/j.imu.2022.101125.
Alevizos, L., Ta, V.T. and Hashem Eiza, M. (2021). Augmenting zero trust architecture to endpoints using blockchain: A state‐of‐the‐art review. Security and Privacy, 5(1). doi:https://doi.org/10.1002/spy2.191.
Alicea, M. and Alsmadi, I. (2021). Misconfiguration in Firewalls and Network Access Controls: Literature Review. ProQuest, [online] 13(11), p.283. doi:https://doi.org/10.3390/fi13110283.
Nawras Alzibdeh, Alrashdan, M.T. and Alaaeddin Almabhouh (2023). Bandwidth Utilization with Network Traffic Analysis. [online] pp.1–5. doi:https://doi.org/10.1109/icmnwc60182.2023.10435712.
Anwar, R.W., Abdullah, T. and Pastore, F. (2021). Firewall best practices for securing smart healthcare environment: A review. Applied Sciences, [online] 11(19), p.9183. doi:https://doi.org/10.3390/app11199183.
Aslan, Ö., Aktuğ, S.S., Okay, M.O., Yilmaz, A.A. and Akin, E. (2023). A Comprehensive Review of Cyber Security Vulnerabilities, Threats, Attacks, and Solutions. Electronics, [online] 12(6), pp.1–42. doi:https://doi.org/10.3390/electronics12061333.
Athar, D.S., Tariq, D.J. and Azeem, A. (2023). Trust in State Institutions and Satisfaction with Life among Christian Minorities in Pakistan. 2(1), pp.17–32. doi:https://doi.org/10.24312/ucp-jhss.02.01.184.
Aweya, J. (2022). Mapping Network Device Functions to the OSI Reference Model. Designing Switch/Routers, pp.53–91. doi:https://doi.org/10.1201/9781003311249-4.
Babak, V., Babak, S., Eremenko, V., Kuts, Y. and Zaporozhets, A. (2025). Protection of Measurement Information from Unauthorized Access. Studies in Systems, Decision and Control, pp.409–458. doi:https://doi.org/10.1007/978-3-031-89406-0_10.
Ben Naseir, M., Dogan, H., Apeh, E. and Ali, R. (2020). National Cybersecurity Capacity Building Framework for Countries in a Transitional Phase. Proceedings of the 22nd International Conference on Enterprise Information Systems. [online] doi:https://doi.org/10.5220/0009576708410849.
Chafika Benzaïd, Nawal Guerd, Nour, Khaled Zeraoulia and Taleb, T. (2025). A Multi-Layered Zero Trust Microsegmentation Solution for Cloud-Native 5G & Beyond Networks. 2022 IEEE Wireless Communications and Networking Conference (WCNC), pp.1–7. doi:https://doi.org/10.1109/wcnc61545.2025.10978671.
Beretas, C. (2024). Information Systems Security, Detection and Recovery from Cyber Attacks. Universal Library of Engineering Technology, [online] 01(01), pp.27–40. doi:https://doi.org/10.70315/uloap.ulete.2024.0101005.
Raffaella Buonsanti, Zaza, L., Bojana Rankovic and Schwaller, P. (2024). A holistic data-driven approach to synthesis predictions of colloidal nanocrystal shapes. Research Square (Research Square). doi:https://doi.org/10.21203/rs.3.rs-5397033/v1.
Cavanni, V., Ceravolo, R. and Miraglia, G. (2024). Knowledge Transfer between Oscillators to Enrich Dynamic Monitoring Datasets. doi:https://doi.org/10.58286/29790.
Cecchet, E., Acharya, A., Tergel Molom-Ochir, Trivedi, A. and Shenoy, P. (2020). WiFiMon: a mobility analytics platform for building occupancy monitoring and contact tracing using wifi sensing. pp.792–793. doi:https://doi.org/10.1145/3384419.3430598.
Chandramouli, R. (2022). Guide to Secure Enterprise Network Landscape. Guide to a Secure Enterprise Network Landscape. [online] doi:https://doi.org/10.6028/nist.sp.800-215
Chatterjee, A., Gerdes, M., Khatiwada, P. and Prinz, A. (2022). Applying Spring Security Framework with TSD-based OAuth2 to Protect Microservice Architecture APIs: A Case Study. IEEE Access, pp.1–1. doi:https://doi.org/10.1109/access.2022.3165548.
Chen, H. and Hu, Z. (2024). Exploring Data Traceability Methods in Information Management Within Universities: An Action Research and Case Study Approach. IEEE Access, 12, pp.175196–175217. doi:https://doi.org/10.1109/access.2024.3493860.
Chen, Y.F., Punchhi, R. and Tripunitara, M. (2022). The poor usability of OpenLDAP Access Control Lists. IET Information Security. doi:https://doi.org/10.1049/ise2.12079.
Czarnota-Bojarska, J. (2021). The ethics of organizational research: Methodological considerations for ensuring respondents’ anonymity and confidentiality. EWOP in Practice, [online] 15(1). doi:https://doi.org/10.21825/ewopinpractice.87141.
Dai, L., Wang, W. and Zhou, Y. (2021). Design and Research of Intelligent Educational Administration Management System Based on Mobile Edge Computing Internet. Mobile Information Systems, 2021, pp.1–12. doi:https://doi.org/10.1155/2021/9787866.
De Simone, L., Mauro, M.D., Natella, R. and Postiglione, F. (2022). A Latency-Driven Availability Assessment for Multi-Tenant Service Chains. IEEE Transactions on Services Computing, pp.1–14. doi:https://doi.org/10.1109/tsc.2022.3183938.
Deshmukh, M.S. and Pavan Ravikesh Bhaladhare (2021). Intrusion Detection System (DBN-IDS) for IoT using Optimization Enabled Deep Belief Neural Network. 2021 5th International Conference on Information Systems and Computer Networks (ISCON). doi:https://doi.org/10.1109/iscon52037.2021.9702505.
Deshmukh, M.S. and Pavan Ravikesh Bhaladhare (2021). Intrusion Detection System (DBN-IDS) for IoT using Optimization Enabled Deep Belief Neural Network. 2021 5th International Conference on Information Systems and Computer Networks (ISCON). doi:https://doi.org/10.1109/iscon52037.2021.9702505.
Dey, S., Sen, K., Saha, N.C. and Saha, S. (2025). Analytical approaches for quantifying and characterizing microplastics: Environmental impacts and bioaccumulation in aquatic Systems. Green Analytical Chemistry, 12, p.100191. doi:https://doi.org/10.1016/j.greeac.2024.100191.
Djenna, A., Harous, S. and Saidouni, D.E. (2021). Internet of Things Meet Internet of Threats: New Concern Cyber Security Issues of Critical Cyber Infrastructure. Applied Sciences, [online] 11(10), p.4580. Available at: https://www.mdpi.com/2076-3417/11/10/4580.
Dos Santos, L.M. and Kwee, C.T.T. (2022). Refusing the Implementation of Information Technology Governance and Information Technology Development in Higher Education Institutions: Voices from Senior Leaders. COVID-19 Challenges to University Information Technology Governance, pp.127–146. doi:https://doi.org/10.1007/978-3-031-13351-0_6.
Ezra, P.J., Misra, S., Agrawal, A., Oluranti, J., Maskeliunas, R. and Damasevicius, R. (2021). Secured Communication Using Virtual Private Network (VPN). Lecture Notes on Data Engineering and Communications Technologies, 73, pp.309–319. doi:https://doi.org/10.1007/978-981-16-3961-6_27.
Farid, F. (2025). A Threat Analysis Framework for Cyberattacks in Smart Cities. Advances in the Internet of Things, pp.101–124. doi:https://doi.org/10.1201/9781003506638-6.
Farooq, M., Khan, R. and Khan, M.H. (2023). Stout Implementation of Firewall and Network Segmentation for Securing IoT Devices. Indian Journal of Science and Technology, [online] 16(33), pp.2609–2621. doi:https://doi.org/10.17485/IJST/v16i33.1262.
Flood, R., Chan, S., Chen, W. and Aspinall, D. (2021). Checking Contact Tracing App Implementations. Edinburgh Research Explorer (University of Edinburgh), pp.133–144. doi:https://doi.org/10.5220/0010237201330144.
Gambo, M.L. and Almulhem, A. (2025). Zero Trust Architecture: A Systematic Literature Review. [online] doi:https://doi.org/10.36227/techrxiv.173933211.18231232/v1.
Guangzhi, W. (2021). Application of adaptive resource allocation algorithm and communication network security in improving educational video transmission quality. Alexandria Engineering Journal, 60(5), pp.4231–4241. doi:https://doi.org/10.1016/j.aej.2021.02.026.
Gupta, N., Jindal, V. and Bedi, P. (2023). A Survey on Intrusion Detection and Prevention Systems. SN computer science, 4(5). doi:https://doi.org/10.1007/s42979-023-01926-7.
Hazra, R., Chatterjee, P., Singh, Y., Podder, G. and Das, T. (2024). Data Encryption and Secure Communication Protocols. Advances in web technologies and engineering book series, pp.546–570. doi:https://doi.org/10.4018/979-8-3693-6557-1.ch022.
Islam, Md.Z., Rahman Khan, M.A. and Hossain, Md.I. (2021). Analysis the importance of VPN for Creating a Safe Connection Over the World of Internet. IJARCCE, 10(10). doi:https://doi.org/10.17148/ijarcce.2021.101017.
Kapoor, J. and Thakur, D. (2022). Analysis of Symmetric and Asymmetric Key Algorithms. ICT Analysis and Applications, pp.133–143. doi:https://doi.org/10.1007/978-981-16-5655-2_13.
Yee, C.K. and Zolkipli, M.F. (2021). Review on Confidentiality, Integrity and Availability in Information Security. Journal of ICT in Education, 8(2), pp.34–42. doi:https://doi.org/10.37134/jictie.vol8.2.4.2021.
Kaur, K.P., Singh, S.K., Kumar, S., Mehra, I., Bansal, S., Chui, K.T., Sharma, V. and Sharma, S.K. (2025). Advanced Tools and Technologies for Phishing Prevention. IGI Global eBooks, [online] pp.187–212. doi:https://doi.org/10.4018/979-8-3693-8784-9.ch009.
Khan, M.A., Kumar, A. and Kailash Chandra Bandhu (2022). Worldwide Interoperability for Microwave Access network optimization with and without relay station for next generation internet access. International Journal of Communication Systems, 35(17). doi:https://doi.org/10.1002/dac.5318.
Lallie, H.S., Thompson, A., Titis, E. and Stephens, P. (2025). Analysing Cyber Attacks and Cyber Security Vulnerabilities in the University Sector. Computers, [online] 14(2), p.49. doi:https://doi.org/10.3390/computers14020049.
Li, Y. and Liu, Q. (2021). A comprehensive review study of cyber-attacks and cyber security; emerging trends and recent developments. Energy Reports, 7(7), pp.8176–8186. doi:https://doi.org/10.1016/j.egyr.2021.08.126.
K. M. Majidha Fathima (2021). A Survey of the Exemplary Practices in Network Operations and Management. Algorithms for intelligent systems, pp.181–194. doi:https://doi.org/10.1007/978-981-15-8530-2_14.
Manda, J.K. (2025). Next-Generation Firewall Technologies for Telecom: Evaluating Advanced Firewall Technologies and Their Role in Protecting Telecom Networks from Evolving Cyber Threats . SSRN Electronic Journal. doi:https://doi.org/10.2139/ssrn.5136748.
Mohamed, A.K.Y.S., Auer, D., Hofer, D. and Küng, J. (2022). A systematic literature review for authorization and access control: definitions, strategies and models. International Journal of Web Information Systems, [online] 18(2). doi:https://doi.org/10.1108/ijwis-04-2022-0077.
Mohammadi, M.K., Mohibbi, A.A. and Hedayati, M.H. (2021). Investigating the challenges and factors influencing the use of the learning management system during the Covid-19 pandemic in Afghanistan. Education and Information Technologies, 26. doi:https://doi.org/10.1007/s10639-021-10517-z.
Mohammed, Y., Abdelhaq, M. and Alsaqour, R. (2020). Prediction Algorithm for Mobile Ad Hoc Network Connection Breaks. International journal of Computer Networks & Communications, 12(6), pp.49–63. doi:https://doi.org/10.5121/ijcnc.2020.12604.
Mohsin, Dr.K. (2025). Cybercrime and Privacy in the Digital Age: Legal Frameworks, Emerging Challenges, and Future Trends. [online] doi:https://doi.org/10.2139/ssrn.5169894.
Moustafa, N., Koroniotis, N., Keshk, M., Zomaya, A.Y. and Tari, Z. (2023). Explainable Intrusion Detection for Cyber Defences in the Internet of Things: Opportunities and Solutions. IEEE Communications Surveys & Tutorials, [online] pp.1–1. doi:https://doi.org/10.1109/COMST.2023.3280465.
Ochulor Nnenna, Prof. Olaniyi Oyinlola, Dr. Anthony Ihuoma and Dr. Chris AC-Ogbonna (2025). Central Bank of Nigeria agricultural financeoptionsand food Security in Nigeria. INTERNATIONAL JOURNAL OF RESEARCH IN SOCIAL SCIENCE AND HUMANITIES, 06(04), pp.135–147. doi:https://doi.org/10.47505/ijrss.2025.4.11
Alibek Nurgaliyev and Wang, H. (2023). Analysis of reverse engineering. doi:https://doi.org/10.1109/icaci58115.2023.10146175.
Abiola Olomola (2024). Zero Trust Architecture and Business Risk Alignment: Comprehensive Governance Framework, Implementation Methodologies, and Future Security Trends for Enterprise Environments. International Journal of Scientific Research and Management (IJSRM), [online] 12(10). doi:https://doi.org/10.18535/ijsrm/v12i10.ec13.
Oluwaseun Ajayi, O., Alozie, C.E. and Abieba, O.A. (2025). Blockchain’s Transformative Potential in Securing Digital Identities and Personal Data. Engineering and Technology Journal, 10(02). doi:https://doi.org/10.47191/etj/v10i02.09.
Pavan Paidy (2025). Unified Threat Detection Platform with AI, SIEM, and XDR. International Journal of Artificial Intelligence, Data Science, and Machine Learning, [online] 6(1), pp.95–104. doi:https://doi.org/10.63282/3050-9262.IJAIDSML-V6I1P111.
Papathanasiou, A., Liontos, G., Liagkou, V. and Glavas, E. (2023). Business Email Compromise (BEC) Attacks: Threats, Vulnerabilities and Countermeasures—A Perspective on the Greek Landscape. Journal of Cybersecurity and Privacy, [online] 3(3), pp.610–637. doi:https://doi.org/10.3390/jcp3030029.
Kipkorir Peacemark, Mwangi, E. and Jotham Wasike (2025). A Machine Learning-Based Packet Sniffer for Detection and Classification of the Denial-Of-Service Attack Packets at the Network Layer. International Journal of Research and Innovation in Applied Science, X(V), pp.568–582. doi:https://doi.org/10.51584/ijrias.2025.100500051.
Prasanna, S.R. and Premananda, B. s. (2021). Performance Analysis of MD5 and SHA-256 Algorithms to Maintain Data Integrity. 2021 International Conference on Recent Trends on Electronics, Information, Communication & Technology (RTEICT), Recent Trends on Electronics, Information, Communication & Technology (RTEICT), 2021 International Conference on, [online] pp.246–250. doi:https://doi.org/10.1109/RTEICT52294.2021.9573660.
Preneel, B. (2025). MASH Hash Functions (Modular Arithmetic Secure Hash). pp.1488–1489. doi:https://doi.org/10.1007/978-3-030-71522-9_594.
Lukman Raimi (2023). Business Continuity and Disaster Recovery Strategies as Resilience Tools after Cyberattacks in Toxic Enterpreneurship Ecosystems. CRC Press eBooks, pp.349–364. doi:https://doi.org/10.1201/9781003319887-21.
Rama, B., K, S., Sudhamani, K., Dhule, S.M., Rani, L.J., Rajkamal, B. and Nagalaxmi, V. (2024). Preparation of Allium Cepa Peel Extract-mediated Silver Nanoparticles: A Hair Dye Formulation. Chinese Journal of Applied Physiology, 40, p.e20240023. doi:https://doi.org/10.62958/j.cjap.2024.023.
Ramezanpour, K. and Jagannath, J. (2022). Intelligent zero trust architecture for 5G/6G networks: Principles, challenges, and the role of machine learning in the context of O-RAN. Computer Networks, 217, p.109358. doi:https://doi.org/10.1016/j.comnet.2022.109358.
Riebe, T., Kühn, P., Imperatori, P. and Reuter, C. (2022). U.S. Security Policy: The Dual-Use Regulation of Cryptography and its Effects on Surveillance. European Journal for Security Research. doi:https://doi.org/10.1007/s41125-022-00080-0.
Schwenk, J. (2022). Attacks on SSL and TLS. Guide to Internet Cryptography, pp.267–328. doi:https://doi.org/10.1007/978-3-031-19439-9_12.
Setiawan, F., Siddik Chaniago, F. and Wibowo, A. (2024). Implementasi SSL VPN (Secure Socket Layer Virtual Private Network) Pada Badan Bank Tanah. Syntax Idea, 6(6), pp.2505–2516. doi:https://doi.org/10.46799/syntax-idea.v6i6.3438.
Shafik, W. (2024). An Overview of Computational Modeling and Simulations in Wireless Communication Systems. CRC Press eBooks, pp.8–40. doi:https://doi.org/10.1201/9781003457428-2.
Shahrani, A.M.A., Rizwan, A., Algarni, A., Alissa, K.A., Shabaz, M., Singh, B.K. and Zaki, J. (2023). A Deep Learning Network-on-Chip (NoC)-Based Switch-Router to Enhance Information Security in Resource-Constrained Devices. Journal of Circuits, Systems and Computers, 33(04). doi:https://doi.org/10.1142/s0218126624500646.
Sivasangari, A., Ajitha, P., Gomathi, R. M., Anandhi, T., Vardhini, V. D., & Kumar, P. A. (2025). Designing a secure and robust virtual private network (VPN) framework for enhanced network communication protection. AIP Conference Proceedings, 3257, 020116. https://doi.org/10.1063/5.0264873
Sri Nikhil Annam (2023). Strategies for Data Privacy in Telecommunication Systems. International Journal of Scientific Research in Computer Science, Engineering and Information Technology, pp.397–406. doi:https://doi.org/10.32628/cseit2390681.
Tegegne, M.D., Melaku, M.S., Shimie, A.W., Hunegnaw, D.D., Legese, M.G., Ejigu, T.A., Mengestie, N.D., Zemene, W., Zeleke, T. and Chanie, A.F. (2022). Health professionals’ knowledge and attitude towards patient confidentiality and associated factors in a resource-limited setting: a cross-sectional study. BMC Medical Ethics, [online] 23(1), pp.1–10. doi:https://doi.org/10.1186/s12910-022-00765-0.
Tian, Y.-C. and Gao, J. (2023). Network Performance Architecture. Signals and communication technology, pp.275–320. doi:https://doi.org/10.1007/978-981-99-5648-7_8.
Ugwu, C. (2025). Patient Data Protection in the U.S. Healthcare Sector: Current Practices, Challenges, and Future Directions. [online] doi:https://doi.org/10.2139/ssrn.5180610.
Muhammad Usama, Aziz, A., Alsuhibany, S.A., Hassan, I. and Farrukh Yuldashev (2025). IDCE: Integrated Data Compression and Encryption for Enhanced Security and Efficiency. Computer Modeling in Engineering & Sciences, 0(0), pp.1–10. doi:https://doi.org/10.32604/cmes.2025.061787.
Veluvali, P. and Surisetti, J. (2021). Learning management system for greater learner engagement in higher education—a review. Higher Education for the Future, 9(1), p.234763112110498. doi:https://doi.org/10.1177/23476311211049855.
Wang, B., Ali-Eldin, A. and Shenoy, P. (2021). LaSS. Proceedings of the 30th International Symposium on High-Performance Parallel and Distributed Computing. doi:https://doi.org/10.1145/3431379.3460646.
Zhang, L., Hu, S., Trik, M., Liang, S. and Li, D. (2024). M2M communication performance for a noisy channel based on latency-aware source-based LTE network measurements. Alexandria Engineering Journal, [online] 99, pp.47–63. doi:https://doi.org/10.1016/j.aej.2024.04.063.
Ţălu, M. (2025). Cyberattacks and Cybersecurity: Concepts, Current Challenges, and Future Research Directions. Digital Technologies Research and Applications, 4(1), pp.44–60. doi:https://doi.org/10.54963/dtra.v4i1.919.
