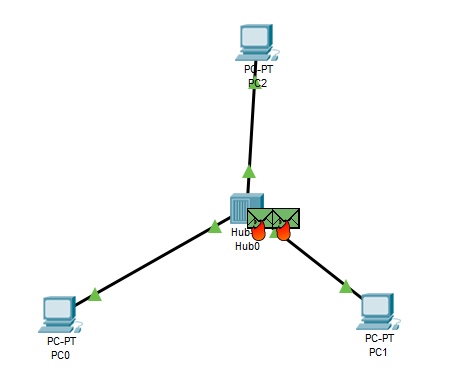
A hub is a hardware device used in networking also known as a network hub, it connects devices from one end to another in the network (Overtoom, Braun, and Carlson, Motorola Solutions Inc, 2014). they are normally used in the connection of devices that are in the local area network or devices within the same location. In hub there are several ports in that when the packets are sent through it, the packets arrive at the device at one port and are copied to different ports of the device so that all the sections of the local area network can be able to see the packets. The hub forms a single network section whereby all the devices that are connected to it will be able to communicate with each other directly.
Hubs are no longer in common use in organizations due to various reasons. First, the hubs do not maintain any record of the mac addresses belonging to devices that are connected to it. This results in the copying of the packets received from the ports to other ports of the local area network segments. the copying action causes the Rebroadcasting of the traffic causing unnecessary broadcast traffic thus creating congestion in the network (Albaugh, Benantar, Chang, and Madduri, International Business Machines Corp, 2010).
Therefore, switches are used in place of the hub since the switches are intelligent and can keep a record of the all devices mac addresses that are directly connected to them. When packets are received from one port of the switch, the switch already knows to which port the packet will be sent to. This allows the users to maximize the use of the bandwidth in the network and reduces traffic. Even if there are multiple ports in the switch the packets containing specific mac address will be sent to its specific destination without distribution to other ports.
In modern networking, the organizations use hubs to create a single segment in the local area network as it is more advantageous since the traffic sniffing becomes faster and also in case of network failure troubleshooting is easier.
Question 2:
A router is a hardware device in networking used to route packets from one network to another thereby providing a communication link between two or more networks possibly in local area network (LAN) or wide area network (WAN). In the router, there are different interfaces which allow the connection of different networks together (Morris, Kohler, Jannotti and Kaashoek, 2009). When a packet is sent from one network to another through the router’s routing protocols available i.e ICMP enables it to communicate and send the packets to the required destination. The packets are attached with its network address and the mac address enabling the router to identify the network to be routed easily. The ports in the router provide an interface for connecting Ethernet cables, DSL cables, and fiber cables and various devices and allow them to communicate to the internet. This means that these interfaces act as the gateway for the network devices connected to them (Lee, Cioffi, Jagannathan and Mohseni, 2017). Soma e routers are wireless thus provide a wireless network connection to devices like smartphone, tablets, laptops and even desktop computers fitted with wireless cards. The wireless access point enables the devices to connect to the network and even to the internet.
A switch is also a hardware device that links together different network elements that are in the same network domain. A switch allows user end devices that are in the same network to communicate together. It has multiple ports where devices are connected. When a packet is received from one port of the switch it has mac address which then the switch will be able to send to the specific destination since the switch keeps mac address of devices connected to it.
The difference between the functionality of the switch from that of the router is that; the switch connects or links together devices on the same network and allows communication between them while the router allows communication of devices that are in a different network. The packets that go through the router are attached to different network address and are routed to their destination while the packets in the switch have mac address which that enable identification of the final destination.
Question 3:
When two or more devices are connected to a hub and are well configured, devices will easily communicate when a PDU is sent at a time. But when two PDUs are sent at the same time and they arrive at the hub, communication will not go through because collision will occur (Mazzola, Alcatel Network Systems Inc, 2010). The hub will create a collision domain when two devices or nodes try to communicate at the same time. It only one device at time else by adding another hub the collision domain will become larger leading to traffic problems. This prevents communication from going through.
In order to avoid collision domain in a hub, we either send one PDU at a time so that one node in the network will send communication while the other will hear.
But the best mechanism in this scenario is to use a switch since the switch has several collision domains. When two PDUs are sent at the same time through it there will be no collision in the process meaning the devices will be able to send or receive packets swiftly without communication being interrupted (Kidong and Sanggook., Electronics Inc, 2014). The switch is much better than the hub as every port of the switch has its own collision domain.
Question 4:
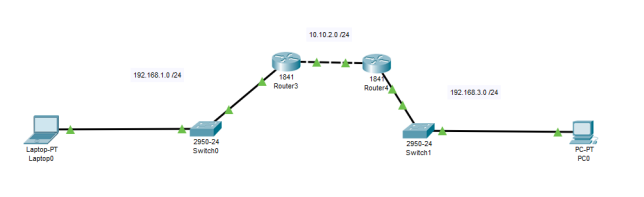
In a situation where two buildings are distant apart example 120 meters. Optical fiber cables will be used for connecting the network in the two buildings. This is because the maximum limit of the optic fiber connection Is 4km and in this situation, it will be more convenient. Ethernet cable cannot be used since its maximum limit is 100Mbs and the connection has to be buried. However, if the connection between the two building was not buried it would have been convenient to use ethernet cable where after 100M is reached a repeater like a hub or a switch will be used in order to extend the connection for the remaining 20M. but because the connection has to be buried optic fiber will work out since no extension will be required in the state or any termination in the connection.
There several factors that are considered in coming up with a solution to implement optic fiber cable in our connection. The first factor is that optic fiber cable covers a longer distance and in this building, it’s within the limit of the cable. It also considered that the optic cable will enable the transmission of the data through it at a higher speed (Keiser, 2013.). In the 120M distance, the speed of data transmission for the case of ethernet cable will reduce but for the fiber cable, the speed will be maintained. The security of data that is being transmitted through the Optic fiber cable is higher since data is transmitted through the light, therefore, it cannot be detected at all means. The fiber optic cable has higher bandwidth for data transmission this means that the volume of the data that will be transmitted across the connection of the two building is higher compared to using copper cable. Therefore, the amount of data that are required to be transmitted will not be limited. It also realized that the use of optic fiber increases the reliability of the transmitted data since its immune to severe environmental conditions like moisture and even electromagnetic interface since it doesn’t carry electric current.
Question 5:
Virtual Private Network (VPN) is a network that provides a secure connection to private networks that are connected through the internet. The main purpose of the VPN is to allow access of the user to the organization network from a remote station and carry out the duties as if one is at work. The virtual private network allows the computers that are connected remotely to perform as if they were in a secure local area network. This means that the connection between the endpoints is encrypted and all the communication and internet traffic goes through a tunnel that is securely known as VPN tunnel (Rekhter and Rosen, Cisco Technology Inc, 2013). The virtual private network is of two types remote access VPN and site to site VPN. The remote access VPN enables the users to connect to the network remotely through the internet and the site to site VPN enables the user to connect to the organization network directly from one end.
In every VPN connection, there are different protocols that ensure the security measures are met. These protocols include point to point tunneling protocol (PPTP), layer 2 tunneling protocol (L2TP), and open VPN. The differences between them is that:
PPTP is a lower level method of encryption that creates borders on the data packets and encrypts them in the connection. It is faster compared to L2TP and OpenVPN as it supports 128-bit keys. Also setting up PPTP is easy and its commonly used mechanism of creating virtual private networks.
L2TP is a protocol that is normally with another set of VPN protocol in order to provide a more secure connection. Between the L2TP connection ends there is secure tunnel generated and in this tunnel, the data is encrypted using IPSec protocol and communication in it is secured. It supports 256-bit key encryption doubling the encapsulation of data thereby improving data security.
OpenVPN is a protocol that is commonly used for creating a connection between two points and sites connection. It uses TLS and SSL protocol and provides a most secure connection with better performance and better speed. It supports up to 256-bit keys for encryption.
VPN security encryptions
Question 6:
Cloud computing is providing different services to the users over the internet which includes the storage of data, database, software’s, servers and even networking. The storage of data over the cloud allows the saving of files to a remote database and one can be able to recover them when in need. These services can either be private or public in that the public services are provided on the internet and there is a fee charged while for the case of private services they are provided to specific clients on a network (JoSEP, KAtz, KonWinSKi, Gunho, PAttERSon and RABKin, 2010.
There are different types of cloud computing like platform as a service (PaaS) and infrastructure as the service (IaaS). The difference between them is that:
Infrastructure as a service involves the provision of resources like storage, hardware, servers and networking over the internet without organization incurring the cost of purchasing them all they need is to pay for them as they use. The types of businesses that are likely to use IaaS are the startup or small business instead of purchasing their IT infrastructure. The Iaas will provide the business with the scalability of their service provision. it also costs efficient in a way that business will not get into much expenditure rather they will pay for these services when they and for what they need.
Platform as a service is a platform that allows the users to create software’s that are provided over the internet. It provides the resources necessary for software creation and the users pay for them as they utilize them in the lifecycle (Hayes, 2009.). Example of PaaS platform is Force.com and Google App Engine and they provide scalability and one can develop and test their software’s. The business that employs these services is the applications developing organizations. This is because the platform provides a humble space that allows the develop different software’s on the internet. Also, they are provided with all the resources they require in the development cycle and in return they incur little cost rather than installing different types of software in their computers for software development.
Question 7:
ADSL is an acronym standing for Asymmetric Digital Subscriber Line. It is a technology for communication which transmits information of digital form that is of higher bandwidth on the existing phone lines from businesses and homes.
The Asynchronous ADSL denotes the state in which more bandwidth is allocated in order to put in line the downstream traffic that originates from the internet to the users than the upstream traffic which moves from user to internet. This means that data flowing from the internet is more than the one required for uploading from the user’s endpoint. It happens in a way that the traffic in DSL is communicated through the usual telephone line over the DSL terminal adapter which is also referred as a DSL modem and it links the computer to DSL line creating a communication link between the user’s computer and the internet. Since each user is assigned to their own telephone line service degradation does not occur. The asynchronous DSL increases the user’s bandwidth thereby increasing their speed in their connection since it can be installed using the twisted pair cable supposedly removing the need for implementation of special cabling. This leads to ADSL becoming a cost-effective way of transmitting a large volume of data at the higher bandwidth.
Question 8:
A firewall is a hardware component or a program for network security which monitors the network traffic that is incoming or outgoing and chooses whether to permit or deny particular traffic basing on the security protocols set. The set of rules defines the traffic that should be allowed to enter or exit from the organization’s private network or from the computer system. This defines the barrier that is set between the untrusted network from the outside like the internet and the trusted network within the organization. Depending on the type of firewall that is put in place one can be able to restrict traffic from accessing to particular Ip address and the domain names or can enable one to be able to block traffics from the IP ports they are using.
There are different types of traffic in a particular network like sensitive traffic, interactive traffic, busty traffics.
The sensitive traffic is the traffic where the operator is expecting to deliver on time. This may include video gaming and online conference call.
The session traffic is the traffics that controls the session that users are performing their tasks in their activities
The busty traffic if the traffic whereby sessions are created at a regular time interval
Firewalls perform packet filtering in that it will be able to allow particular packets to pass through while restricting others. If it is configured to permit HTTP packets only to pass through to a specific port all the other packets including the RDP connections will be denied (Judge, Beadle and Chicharo, 2010). The firewall will be able to evaluate the source ip address and the destination address and compares it with the set protocols, therefore, denying other connections from transmitting data.
References
Albaugh, V.A., Benantar, M., Chang, P.Y.T. and Madduri, H.H., International Business Machines Corp, 2010. Dynamic service-on-demand delivery messaging hub. U.S. Patent 7,849,130.
Hayes, B., 2009. Cloud computing. Communications of the ACM, 51(7), pp.9-11.
JoSEP, A.D., KAtz, R., KonWinSKi, A., Gunho, L.E.E., PAttERSon, D. and RABKin, A., 2010. A view of cloud computing. Communications of the ACM, 53(4).
Keiser, G., 2013. Optical fiber communications. Wiley Encyclopedia of Telecommunications.
Kidong, L.E.E. and Sanggook, K.I.M., LG Electronics Inc, 2014. MAC PDU Signaling and operating methods for access class barring and back-off control for large-scale radio access network. U.S. Patent 8,908,619.
Lee, B., Cioffi, J.M., Jagannathan, S. and Mohseni, M., 2017. Gigabit dsl. IEEE Transactions on communications, 55(9), pp.1689-1692.
Mazzola, A.J., Alcatel Network Systems Inc, 2010. Distributed routing network element. U.S. Patent 5,461,624.
Morris, R., Kohler, E., Jannotti, J. and Kaashoek, M.F.,2009. The Click modular router. ACM SIGOPS Operating Systems Review, 33(5), pp.217-231.
Overtoom, E.J., Braun, M.R. and Carlson, M., Motorola Solutions Inc, 2014. Dual-role compatible USB hub device and method. U.S. Patent 6,732,218.
Rekhter, Y. and Rosen, E.C., Cisco Technology Inc, 2013. Virtual private network employing tag-implemented egress-channel selection. U.S. Patent 6,526,056.
Judge, J., Beadle, H.W.P. and Chicharo, J., 2010. Sampling HTTP response packets for prediction of Web traffic volume statistics. In IEEE GLOBECOM 1998 (Cat. NO. 98CH36250)(Vol. 5, pp. 2617-2622). IEEE.