Introduction
Students: In the box below, please explain the purpose of Hashing and explain how it is relevant to Digital Forensics Technology and Practices.
| Introduction |
| Hashing is important because it assists in the verification of data integrity as the unique hash value for each data can be used to detect any small change in the data. It is relevant in Digital forensics as it enables the investigators to detect whether the digital evidence has been tampered with by alteration or whether it has been corrupted. The integrity of the digital evidence is maintained by making a comparison of the original file’s hash value and the hash value of the files after the investigation to ensure it’s the same indicating that the evidence has not been tampered with. |
Screenshot 1 – Yourname Displayed as the Hostname
When you look at the hostname of the computer, the computer name should be Your First Name. The use of anyone else’s name may result in an academic integrity review by your professor. Please label your screenshot to receive full credit.
Take a screenshot of the Your Name as the Computer Name as the Hostname
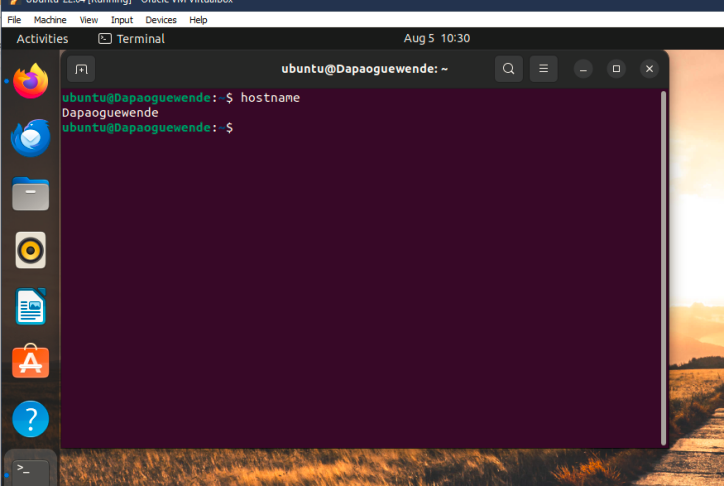
Screenshot 2 – Yourname file hashed with Sigcheck
Take a screenshot of the hostname.txt file hashed with sigcheck. The use of anyone else’s name may result in an academic integrity review by your professor. Also, it is mathematically possible that you and another student could have the same MD5 hash for your hostname text file. Please label your screenshot to receive full credit.
Take a screenshot of the yourname.txt file hashed with sigcheck
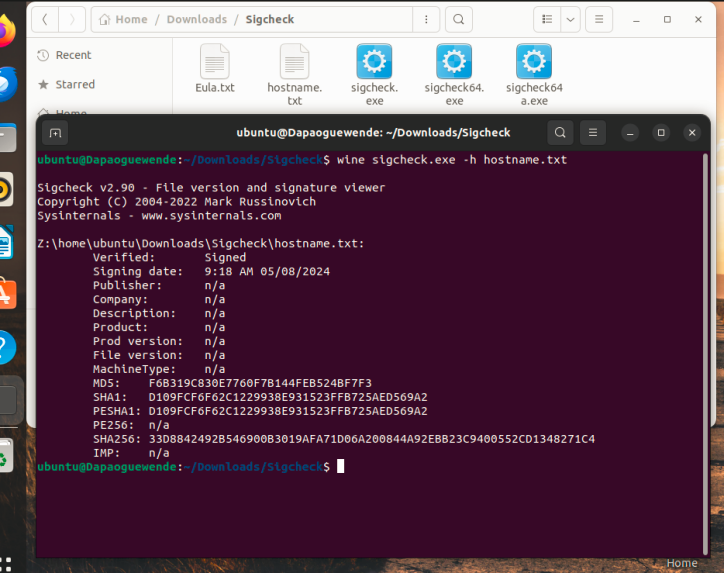
Screenshot 3 –Yourname file hashed with HashTab
Take a screenshot of the yourname.txt file hashed with Hashtab. The use of anyone else’s name may result in an academic integrity review by your professor. Please label your screenshot to receive full credit.
Take a screenshot of the yourname.txt file hashed with Hashtab
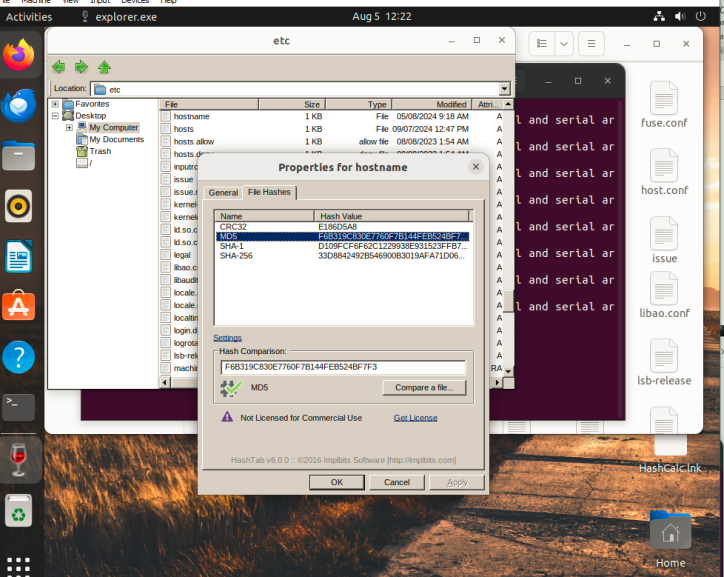
Screenshot 4 – Yourname file hashed with HashCalc
Take a screenshot of the yourname.txt file hashed with hashcalc. The use of anyone else’s name may result in an academic integrity review by your professor. Please label your screenshot to receive full credit.
Take a screenshot of the yourname.txt file hashed with Hashcalc
Screenshot 5 – MD5 of Yourname File in /usr/share/windows-binaries
The file in /usr/share/windows-binaries should have first name. The use of anyone else’s name may result in an academic integrity review by your professor. Please label your screenshot to receive full credit.
Take a screenshot of the MD5 Hash of the Yourname File in /usr/share/windows-binaries
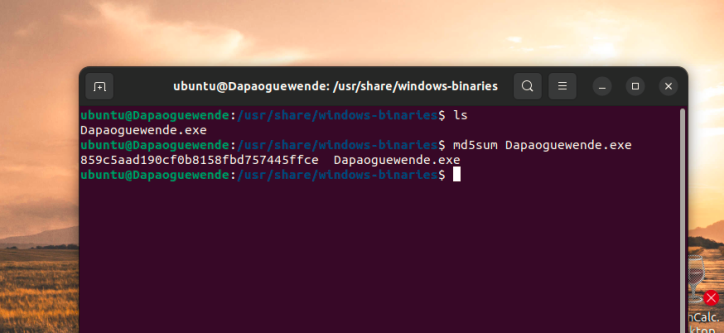
Screenshot 6– SHA1 hash of Yourname File in /usr/share/windows-binaries
Provide the SHA1 hash of the yourname file in /usr/share/windows-binaries directory. The use of anyone else’s name may result in an academic integrity review by your professor. Please label your screenshot to receive full credit.
Take a screenshot of the SHA1 hash of the Yourname File in /usr/share/windows-binaries
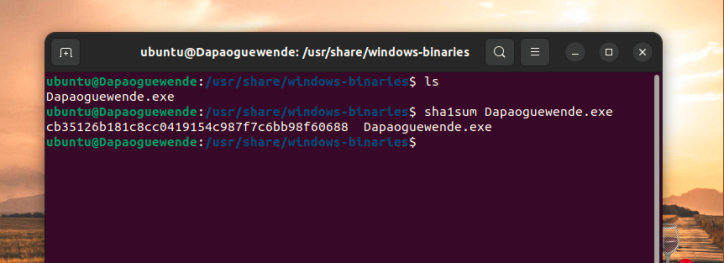
Screenshot 7– SHA256 hash of Yourname File in /usr/share/windows-binaries
Provide the SHA256 hash of the yourname file in /usr/share/windows-binaries directory. The use of anyone else’s name may result in an academic integrity review by your professor. Please label your screenshot to receive full credit.
Take a screenshot of the SHA256 hash of the Yourname File in /usr/share/windows-binaries
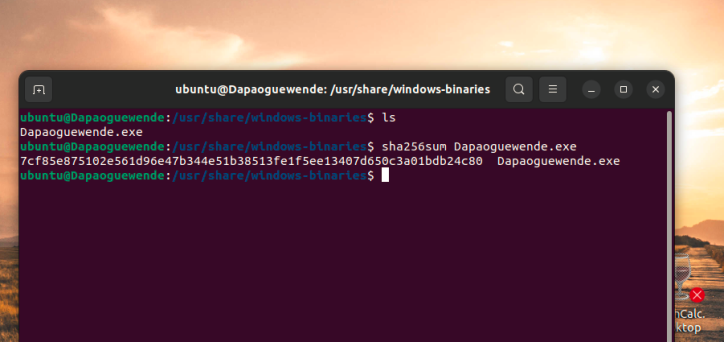
Screenshot 8– SHA384 hash of Yourname File in /usr/share/windows-binaries
Provide the SHA384 hash of the yourname file in /usr/share/windows-binaries directory. The use of anyone else’s name may result in an academic integrity review by your professor. Please label your screenshot to receive full credit.
Take a screenshot of the SHA384 hash of the Yourname File in /usr/share/windows-binaries
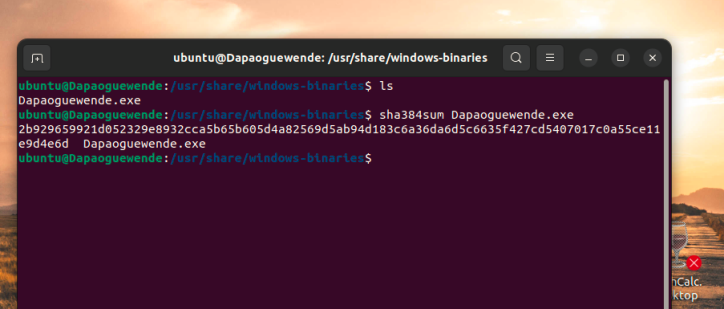
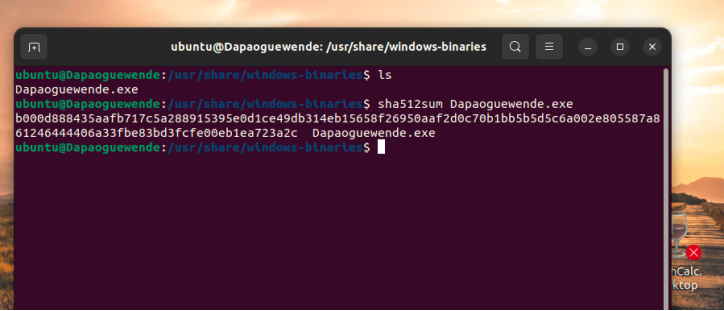
Screenshot 9– SHA512 hash of Yourname File in /usr/share/windows-binaries
Provide the SHA512 hash of the yourname file in /usr/share/windows-binaries directory. The use of anyone else’s name may result in an academic integrity review by your professor. Please label your screenshot to receive full credit.
Take a screenshot of the SHA512 hash of the Yourname File in /usr/share/windows-binaries
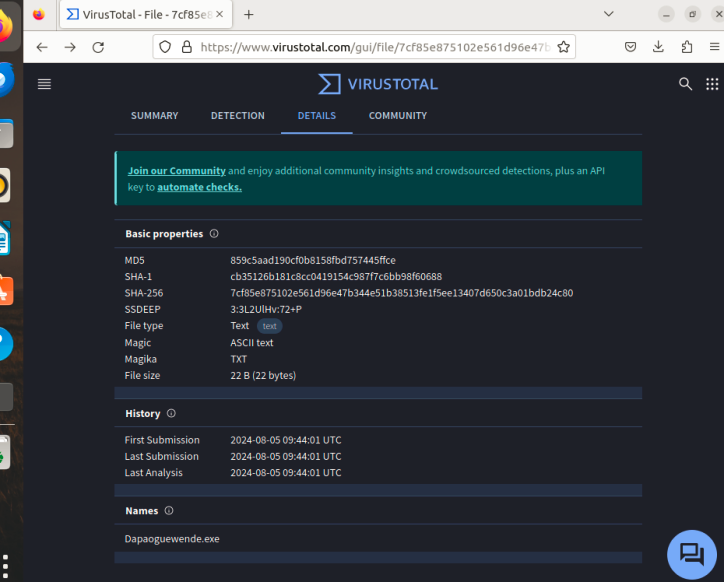
Screenshot 10 – Virustotal Statistics
Provide the virus total statistics. Timestamps from a previous semester or a different name may result in an academic integrity review by your professor. Please label your screenshot to receive full credit.
Take a screenshot of your Virustotal screenshot with the timestamp from this semester.
Conclusion
Utilizing the virus total program also gives us the same hash values and it also provides a comprehensive analysis of the files after scanning for the availability of the file in multiple virus scanning engines to detect malware and other threats. Virustotal also indicates the presence of vulnerabilities in a file. This is relevant in digital forensics as malware detection is a critical aspect in digital forensics to assess the nature of the threats identified in evidence files.
While doing this lab I learned how to utilize wine to run Windows applications in Ubuntu Linux where the Windows tools used such as sigcheck and hashcalc were installed using wine to compute the hash values. To calculate the hash values using the terminal, inbuilt Linux commands were used that include md5sum, sha1sum, and sha256 to get the specific hash values required as shown above.
APA References
Students
Khairunnisak, K., & Widodo, W. (2023). Digital Forensic Tools And Techniques For Handling Digital Evidence. Jurnal RESISTOR (Rekayasa Sistem Komputer), 6(1), 1–11. https://doi.org/10.31598/jurnalresistor.v6i1.1266
Mando_elnino. (2023, March 27). A Brief use of Sysinternals: Sigcheck. Medium. https://medium.com/@mando_elnino/explaining-and-using-sysinternals-sigcheck-f74ac4356000
Masri, R., & Aldwairi, M. (2017, April 1). Automated malicious advertisement detection using VirusTotal, URLVoid, and TrendMicro. IEEE Xplore. https://doi.org/10.1109/IACS.2017.7921994
Roussev, V. (2009). Hashing and Data Fingerprinting in Digital Forensics. IEEE Security & Privacy Magazine, 7(2), 49–55. https://doi.org/10.1109/msp.2009.40
Xenya, M. C., & Quist-Aphetsi, K. (2019). A Cryptographic Technique for Authentication and Validation of Forensic Account Audit Using SHA256. 2019 International Conference on Cyber Security and Internet of Things (ICSIoT). https://doi.org/10.1109/icsiot47925.2019.00008
