Introduction:
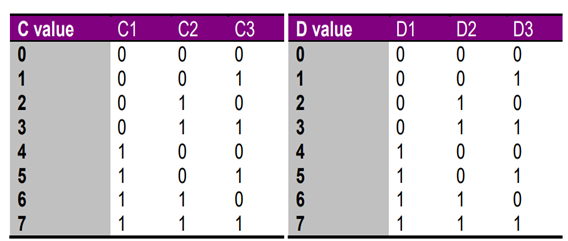
The main objective of this particular assignment is to build a lift operational logic circuit in Logisim. The logic circuit has two inputs, namely C and D which has values in the range of 0 to 7 representing the floor numbers. Floor 0,4 and 6 are known to be private floors and the operation of the lift from or to the private floors are restricted. Additionally, the lift does not move when starting and destination floors are same. This is modelled by a Successful LED light in the circuit. The LED is ON when lift movement is possible and the LED is OFF when the lift movement is restricted. The input C and input D are modelled by C1,C2,C3 and D1,D2 and D3 respectively with each having one bit.
Representation table of input C and D:
Successful operations from C to D:
1 to 2, 2 to 1, 1 to 3, 3 to 1, 1 to 5 , 5 to 1, 1 to 7, 7 to 1, 2 to 3, 3 to 2, 2 to 5, 5 to 2, 2 to 7, 7 to 2, 3 to 5, 5 to 3, 3 to 7, 7 to 3, 5 to 7, 7 to 5
Truth Table representation of C and D for Successful operation:
| C1 | C2 | C3 | D1 | D2 | D3 | Successful Operation (S) |
| 0 | 0 | 1 | 0 | 1 | 0 | 1 to 2 |
| 0 | 1 | 0 | 0 | 0 | 1 | 2 to 1 |
| 0 | 0 | 1 | 0 | 1 | 1 | 1 to 3 |
| 0 | 1 | 1 | 0 | 0 | 1 | 3 to 1 |
| 0 | 0 | 1 | 1 | 0 | 1 | 1 to 5 |
| 1 | 0 | 1 | 0 | 0 | 1 | 5 to 1 |
| 0 | 0 | 1 | 1 | 1 | 1 | 1 to 7 |
| 1 | 1 | 1 | 0 | 0 | 1 | 7 to 1 |
| 0 | 1 | 0 | 0 | 1 | 1 | 2 to 3 |
| 0 | 1 | 1 | 0 | 1 | 0 | 3 to 2 |
| 0 | 1 | 0 | 1 | 0 | 1 | 2 to 5 |
| 1 | 0 | 1 | 0 | 1 | 0 | 5 to 2 |
| 0 | 1 | 0 | 1 | 1 | 1 | 2 to 7 |
| 1 | 1 | 1 | 0 | 1 | 0 | 7 to 2 |
| 0 | 1 | 1 | 1 | 0 | 1 | 3 to 5 |
| 1 | 0 | 1 | 0 | 1 | 1 | 5 to 3 |
| 0 | 1 | 1 | 1 | 1 | 1 | 3 to 7 |
| 1 | 1 | 1 | 0 | 1 | 1 | 7 to 3 |
| 1 | 0 | 1 | 1 | 1 | 1 | 5 to 7 |
| 1 | 1 | 1 | 1 | 0 | 1 | 7 to 5 |
K-MAP of SOP form:
| D1D2D3 | |||||||||
| C1C2C3 | 000 | 001 | 011 | 010 | 110 | 111 | 101 | 100 | |
| 000 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 001 | 0 | 0 | 1 | 1 | 0 | 1 | 1 | 0 | |
| 011 | 0 | 1 | 0 | 1 | 0 | 1 | 1 | 0 | |
| 010 | 0 | 1 | 1 | 0 | 0 | 1 | 1 | 0 | |
| 110 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 111 | 0 | 1 | 1 | 1 | 0 | 0 | 1 | 0 | |
| 101 | 0 | 1 | 1 | 1 | 0 | 1 | 0 | 0 | |
| 100 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
S =
Solution of the K-map gives minimum SOP expression as given below.
Minimized Boolean Expression:
S = C1’C2C3’D3 + C3D1’D2D3′ + C2’C3D1’D2 + C1C3D1’D3 + C2C3D2’D3 + C1’C3D1D3 + C2’C3D2D3
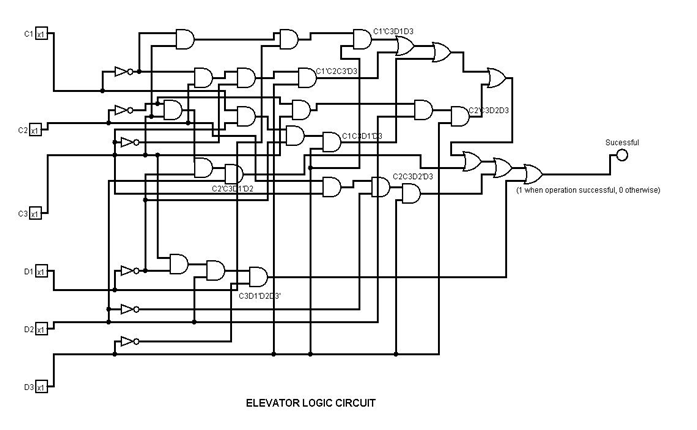
Logisim Circuit Diagram:
Testing:
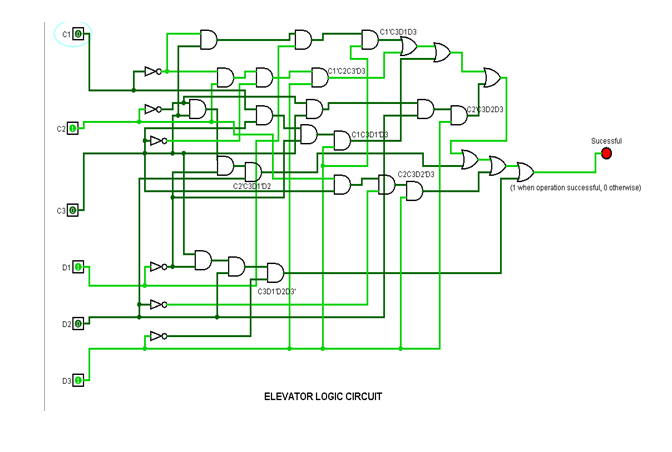
C input C1C2C3 = 010(C = 2) and D input D1D2D3 = 101(D = 5)
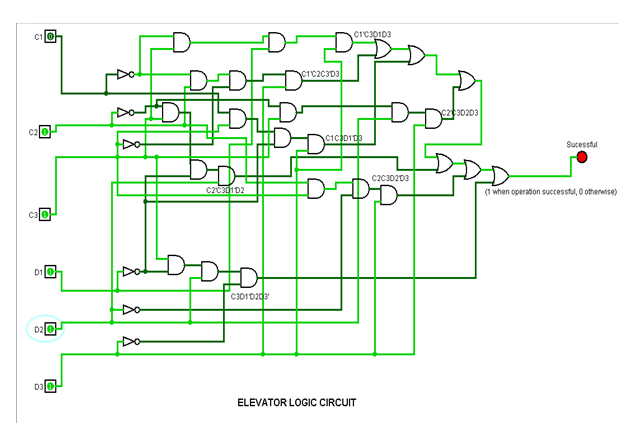
C input C1C2C3 = 011(C=3) and D input D1D2D3 = 111(D=7)
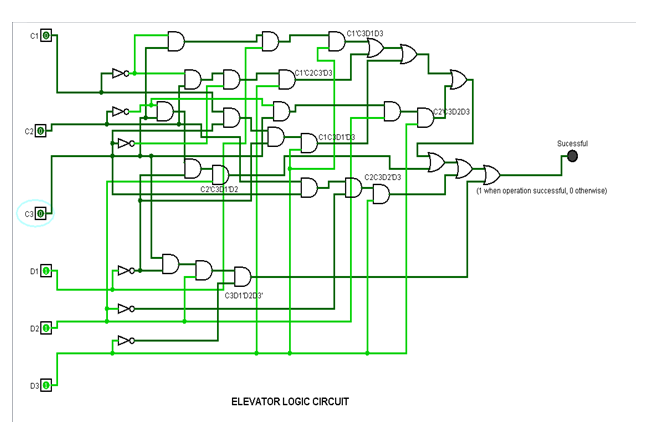
C input C1C2C3 = 000(C=0) and D input D1D2D3 = 111(D=7)
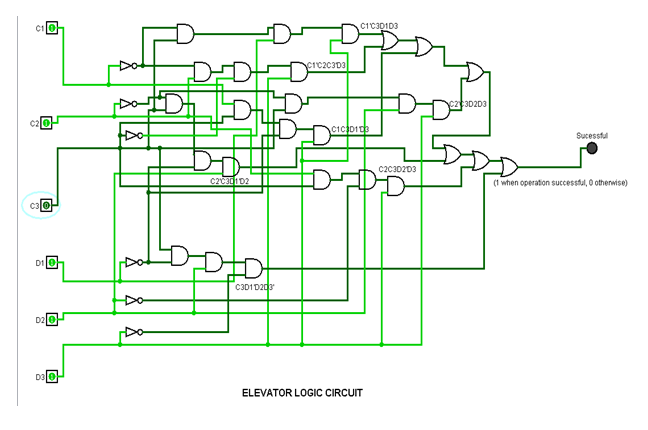
C1C2C3 = 110(C=6) and D1D2D3 = 111(D=7)
It is evident from the testing that the lift movement is working according to the truth table. The first test is Successful as C=2 and D= 5 and both are valid input for movement. The second test is also Successful as C=3 and D=7 and both operations are valid. However, in the third test is not Successful as C=0 (a private floor) and D = 7 (valid for movement). This way as the destination floor is private in fourth test (as C =110 and D=111) the lift movement is Unsuccessful.
Conclusion:
Thus in conclusion it can be stated that design of the lift movement logic circuit is successfully implemented as all the operations of the lift is according to the truth table for Successful operation. This Successful operation is realized from the ON state of Successful LED in the logic circuit. The method sum of product and then K-MAP technique is used here to build the logic circuit. A slightly different approach of providing only permitted states of C and D through two 3 to 8 decoders can be used to make the same operation of circuit, however in that case the number of primary gates will be larger and thus the circuit is in-efficient from the point of view of cost of the circuit. The circuit can further be integrated to count the number of successful and unsuccessful operation and locking the circuit operation after a certain number of Unsuccessful operations. This can be realized by mainly a counter and other necessary gates, but due to complexity and size of circuit this advance design is not implemented here. Thus the design of the circuit is appropriate based on the stated specific operations of the lift.
Introduction
Increased use of technology in healthcare has brought massive positive change in the health industry. This positive change has not only benefited the patients but also the professionals. Patients are able to access best diagnostic tools, cutting-edge treatments, reduced treatment procedures which results in less pain and quicker recovery. Patients can consult specialists, targeted treatments and the availability of intuitive mobile applications. The advancement of technology has improved the life of the patient in general. (Mettler, 2016)
Specialists have benefited the easier execution of their duties. Introduction of technology in healthcare has eliminated a lot of paperwork. For example in record keeping is now easier using mobile applications to collect patient data. Through online consultation, the business owner has benefited since they can offer services to many patients all over the world. (Kohli and Tan, 2016)
However, technology has also a negative impact on healthcare. Some of these negatives are reduced-impersonal treatment. These intuitive mobile applications are as good as the person who programmed them. For this reason, they do not give an equal quality of service as a personnel specialist in many cases. Some technologies have negative effects such as radiations. Invasion of electronic medical privacy record is another negative effect that we cannot ignore. Since the patients’ data is electronically recorded and stored, it is more venerable to the hacker and other unauthorized personnel. (Martínez-Pérez, et al., 2015)
In this report, we shall discuss the various technological innovation and their impact to healthcare, the privacy, and security of data in healthcare, various technological issues in healthcare and the appropriate measure that can be taken.
Case study: The impact of technology in the healthcare industry
Charity Healthcare Centre is a growing hospital that has various departments. Due to the increased number of patients visiting this healthcare, the management wishes to invest in technology to couple with this situation. The management wishes to know the impact of this innovation. The management needs to know how various medical technologies will affect its operations. They need to know how they can apply the technology and maintain security and the privacy of patients’ data. The management also needs to know the issues that may arise, and how to handle them. As an IT consultant, you are asked to prepare a report addressing the above areas of interest.
Issues raised by IT in the healthcare industry and recommendations
Technology Glitches
The developer of medical technology has to test and correct all the bugs before the innovation can be put into full use. For example, a professional has been experiencing hardware and software problems in Google Glass. (Chang, et al., 2016) These issues have to be solved before the professionals can fully rely on this technology in everyday use. In the google glass technology, the physicians have also experienced an issue with the camera’s battery life and the camera pointing in the wrong direction.
In order to solve these problems, developers should improve the camera’s battery life, which will increase the efficiency of Google Glass. These cameras should be developed in a way that they are flexible to rotate around in order to solve the problem of facing the wrong direction. (Chang, et al., 2016)
Privacy issues
Maintaining the patient’s privacy is a big concern in the medical industry. Professional are worried the increased use of technology will undermine the patient’s privacy. For example, when physicians are uploading the surgical data onto the internet using Google Glass may allow unauthorized viewing. (Zhang, et al., 2015)
In order to solve this issue, physicians need to let their patients known that they will be using Google Glass to film and get permission to adhere their right to privacy.
Multitasking and distractions
Some of the professionals are concerned that some physician may misuse the technology. Some physicians are attempted to serve the internet rather than giving the patients full attention they deserve.
This technological advancement is distractive and physicians must choose to use them responsibly in order to get maximum out of them.
Student # 2
Case study: The impact of information technology on surgical facility
Due to its huge innovation strength data technology infiltrates not solely administrative ranges of surgical work, however surgical handicraft itself. Thus nowadays operations may be planned and simulated at the computer. Digitized findings may be called up throughout the operation. Robots are moving instruments and are able to take over outlined elements of an intervention severally. However, the various current developments on laptop assisted Surgery are raising questions concerning the effectiveness. Information technology earned a great importance for medical documentation and performance-oriented billing within the past years. The conversion to the system of diagnoses connected teams is not conceivable without economical electronic documentation and writing. Engineering and flexibility to hospital-internal advancement can become a crucial quality criterion of hospital data systems. Because of the increasing condensation of workload and the immanent shortage of personnel surgical coaching is attaining a brand new meaning for the physician himself and the hospital carrier.
Ambulatory Surgery Center is a non-profitable surgical facility located in UK. This organization wishes to improve its surgical services offered to the patients. In order to achieve its objectives, it has decided to introduce new technology in its operations. As an IT expert, you have been asked to give recommendation on the impact of these technologies.
Issues and Recommendation
Although technology is rapidly changing the healthcare industry, there a number of issues that need to be concerned with before venturing to use of technology. The following are some of the issues and the possible solution.
Security and privacy
Security and privacy on patient’s data is a major concern when using technology in healthcare. When data is electronically stored, there is a high risk of hacker attacks. This problem can be prevented by applying various security measures, for example, using anti-virus software in systems and uses of strong passwords. (Martínez-Pérez, et al., 2015)
Technology misuse
Some specialist misuses the technology, for example, the use of social media instead of serving patients. This issue can be solved by ensuring that the specialist is self-disciplined enough not to misuse the technology.
Patient involvement
Patients should be well informed about technology that are to be used to treat him/her. Patients should be alerted on various side effects of various technology. For example, some technology such as CT scan causes a headache. Patient’s consent is required before any operation is performed on him/her.
Conclusion
As technology transforms the healthcare industry, security and data privacy on patient’s data is of at most importance. As much as the big data technology becomes more prominent, healthcare is reluctant to share massive data for centralized data processing. It is recommendable that every healthcare industry to be well informed on various technologies before they introduce them. Patients should also be informed about any technology that is to be used in his/her treatment. With this, the right to privacy of a patient can adhere.
Student # 3
Executive summary
This paper is prepared to address the impacts of technology in the healthcare industry. Security and privacy of patient’s data is a concern is this industry. This paper discusses various ways to ensure the security and privacy of data in the healthcare industry. Various technology has a different impact on healthcare. This report discusses various technologies and the impact they have in the healthcare industry.
This report also has discussed into details the issues that how raised due to the use of technology in healthcare. This report has also provided some recommendations on how to solve these issues.
Case Study: Impact of information technology in medical research
Health care is changing into a more and more data-intensive field as doctors and researchers generate gigabytes of medical data on patients and their diseases. Whereas a patient visiting the doctor twenty years ago could have solely generated some information, basic data like weight, vital sign, and symptoms. A medical encounter nowadays could leave an extended path of digital information from the utilization of high-definition medical imaging to implantable or wearable medical devices like heart monitors. Additionally, as doctors and hospitals transition away from paper medical records, this information is increasingly being collected and made accessible in an electronic format.
The availability of huge information sets of digital medical data has made potential the utilization of informatics to enhance health care and medical analysis. Usually noted as “in silico” analysis, informatics offers a brand new pathway for medical discovery and investigation. Informatics focuses on developing new and higher ways in which of using technology to process data. You are asked to investigate on impact of technology in research and make recommendation on the report.
Issues and Recommendation
Although could computing technology has many benefits in the healthcare industry, security and privacy is a major concern. The following measures are taken to ensure the security and privacy of the patient’s data maintained.
Privacy and security on data in healthcare
The patient’s data is stored in various data centers with different levels of security. It is a requirement that every healthcare industry to have a HIPAA certificate. Although many healthcare is certified, it does not mean that the patient’s data is safe. The HIPAA focus on making sure that the security procedure and policies are met and not the implementation of security measures. (Martínez-Pérez, et al., 2015)
Traditional security measures cannot be applied directly to inherent and diverse data sets. With the increased health cloud solutions, measures of securing this massive distributed SaaS solutions have become complex with the data format and data source. Hence big data governance is prior to exposing this health data to analytics.
Data governance
Data governance is a set of practices that ensures the formal management of data in healthcare. These sets of processes help to ensure data privacy, usability and integrity of data in an organization. Data governance has a lot of benefits in healthcare. For example, it offers great transparency to activity that relies on data. The company can be able to make better decisions. It also provides a well-outlined process on how data is to be stored, backed up, archived and protected against hackers and thieves. (Wang, et al., 2018)
In order for Charity Healthcare to ensure data security and privacy, the management needs to come with well-defined data governance.
Real-time security analytics
Security analytics is the process of using data collection, data aggregation, and data analysis tools to monitor security threats in real time. Large and diverse data sets may be included in the detection algorithm depending on the tool is used.
On the Internet of Thing (IoT) environment, there is a challenge in implementing security in resource-constrained networks and it will continue being complex as the number of IoT increases. (Moosavi, et al., 2016)
Charity Healthcare needs to install a tool that will handle its data especially if the company wishes to introduce the cloud computing technology or the big data technology. IT experts can monitor possible risk in real time and take necessary measures before the damage take place.
Privacy-preserving analytics
Invasion of patient’s data privacy is a growing concern in the big data analytics technology. For example, data anonymization is one of the ways to protect the patient’s identity. In deriving healthcare analytics, privacy-preserving encryption techniques that allow running prediction algorithms on encrypted data is essential. (Sharma, et al., 2018)
As healthcare industries migrate to IoT, there is a need to process and analyze data in an ad-hoc decentralized way. However, performing these resource-exhausting operations while maintaining the patient’s data privacy is a challenge. (Moosavi, et al., 2016) As healthcare analytics get popular, new privacy laws are immerging to protect the patient’s data. Patient consent is required before performing any analytics on patient’s data. There is also a need to draft to outline all processes that are to be performed on the patient’s data.
References
Chang, J.Y.C., Tsui, L.Y., Yeung, K.S.K., Yip, S.W.Y. and Leung, G.K.K., 2016. Surgical vision: Google Glass and surgery. Surgical innovation, 23(4), pp.422-426.
Moosavi, S.R., Gia, T.N., Nigussie, E., Rahmani, A.M., Virtanen, S., Tenhunen, H. and Isoaho, J., 2016. End-to-end security scheme for mobility enabled healthcare Internet of Things. Future Generation Computer Systems, 64, pp.108-124.
Pineda, A.L., Moran, M.F.R., Aguilar, C.A., Valle, S.M.F., Rosales, R.A., Bhatt, A.S., Sheth, S.N. and Bustamante, C.D., 2018. Data mining of digitized health records in a resource-constrained setting reveals that timely immunophenotyping is associated with improved breast cancer outcomes. bioRxiv, p.198721.
Sharma, S., Chen, K. and Sheth, A., 2018. Toward practical privacy-preserving analytics for iot and cloud-based healthcare systems. IEEE Internet Computing, 22(2), pp.42-51.
Wang, Y., Kung, L. and Byrd, T.A., 2018. Big data analytics: Understanding its capabilities and potential benefits for healthcare organizations. Technological Forecasting and Social Change, 126, pp.3-13.
Zhang, K., Yang, K., Liang, X., Su, Z., Shen, X. and Luo, H.H., 2015. Security and privacy for mobile healthcare networks: from a quality of protection perspective. IEEE Wireless Communications, 22(4), pp.104-112.
Mettler, M., 2016, September. Blockchain technology in healthcare: The revolution starts here. In 2016 IEEE 18th International Conference on e-Health Networking, Applications and Services (Healthcom) (pp. 1-3). IEEE.
Martínez-Pérez, B., De La Torre-Díez, I. and López-Coronado, M., 2015. Privacy and security in mobile health apps: a review and recommendations. Journal of medical systems, 39(1), p.181.
Database Fundamentals
Introduction
The report is explaining the database system of International Parcel Service (IPS). The logical design and physical design both are explained in the report. The report is showing the database report, database form and all developed queries. The logical design is developed by the ER diagram and physical design is implemented into the MS Access database.
ER Diagram
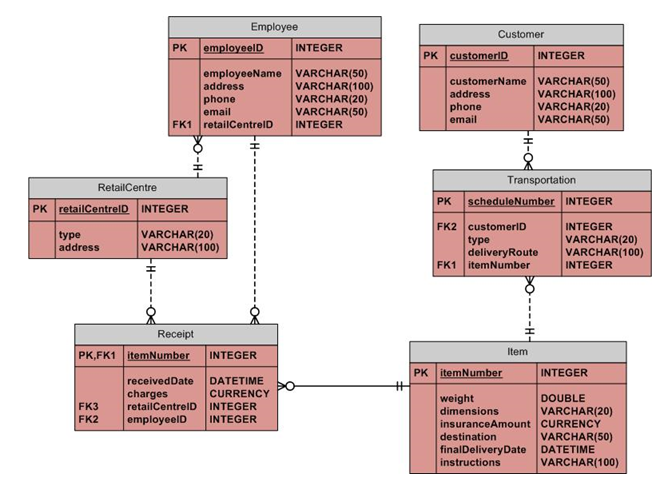
The ER diagram is showing the database in pictorial form. Each entity and its attributes are being shown in the report. The ER diagram is made in the crow’s foot notation. The tables in the ER diagram are in the third normalized form.
Relational Schema inThird Normal Form Relations
TabCustomer (FlcustomerID, FlCustomerName, Fladdress, Flphone, Flemail)
Primary Key FlCustomerID
TabItem (FlitemNumber, Flweight, Fldimensions, FlinsuranceAmount, Fldestination, FlfinalDeliveryDate, Flinstructions)
Primary Key FlitemNumber
TabRetailCentre (FlretailCentreID, Fltype, Fladdress)
Primary Key FlretailCentreID
TabEmployee (FlemployeeID, FlemployeeName, Fladdress, Flphone, Flemail, FlretailCentreID)
Primary Key FlemployeeID
FlretailCentreID references Tabretail_Centre (FlretailCentreID)
TabReceipt (FlitemNumber, FlreceivedDate, Flcharges, FlretailCentreID, FlemployeeID)
Primary Key FlitemNumber
FlretailCentreID references Tabretail_Centre (FlretailCentreID)
FlemployeeID references TabEmployee (FlemployeeID)
FlitemNumber references TabItem (FlitemNumber)
TabTransportation (FlscheduleNumber, FlcustomerID, Fltype, FldeliveryRoute, FlitemNumber)
Primary Key FlscheduleNumber
FlcustomerID references TabCustomer (FlcustomerID)
FlitemNumber references TabItem (FlitemNumber)
Functional Dependency in Retail Centre Table/ Dependency Diagram
Type à RetailCentreID
Address à RetailCentreID
- The table has no repeated group.
- All fields depend upon the primary key only. The primary key is single primary key. So, there is no partial dependency in the table.
- There is no transitive dependency because all fields depend upon the primary key only.
The table is satisfying all the above mentioned rules of third normalization. Therefore, the retail table is in third normal form.
All the tables are satisfying the same normalization rule in the database.
There is not any partial or transitive dependency in the above table. All tables are following the same third normalization rules.
(Guru99 2016)
Database Implementation
(Access Programmers n.d.)
Item Form
Queries
Query 1
SELECT * FROM TabEmployee WHERE RetailCentreID=1001;
Query 2
SELECT RetailCentreID, Count(employeeID) AS NumberOfEmployees FROM TabEmployee GROUP BY RetailCentreID;
Query 3
SELECT TabEmployee.retailCentreID, TabRetailCentre.address, TabEmployee.employeeID, TabEmployee.employeeName, TabEmployee.address, TabEmployee.phone, TabEmployee.email FROM TabRetailCentre INNER JOIN TabEmployee ON TabRetailCentre.retailCentreID=TabEmployee.retailCentreID;
Report
The report is based upon the query 3 as shown below-
Conclusion
The report is fulfilling all the requirements of the IPS database system which is developed in MS Access database. MS Access database is the complete package in itself because it gives the features to make queries, forms and reports. The report is the complete justification of all the tasks completed for the IPS database system.
References
Guru99 (2016). Learn Database Normalization with the help of a case study. Online. Available: http://www.guru99.com/database-normalization.html. [Accessed: 22-May-2019]
Access Programmers (n.d.). Normalizing the Table Design. Online. Available: https://www.access-programmers.com/normalizing-the-table-design.aspx. [Accessed: 22-May-2019]
Data Structures and Algorithms
Introduction
For a program to have executed successfully and having met all the properties it should have executed with the minimum space in the memory and with the least time possible. That is what is referred as an effective and efficient algorithm. The ones that require a lot of space and time for execution are said to be less effective in data structures.
The library system Analysis
A library system or Library Management System (LMS) is a planning system for a library and is used to track items owned from the library, orders made, borrowers and borrowed items from the library, bills paid and all management pertaining the library. For the system to work appropriately, several variables must be identified so as to store some known or unknown quantities of data. These quantities of information are referred to as values and they are assigned with a symbolic name. Some of the variables that are going to be used in the making of the library system include;
- Short
- Int
- Long
- Float
- Double
The following involves the variables that are essential in the storage of data that is going to
be used in the execution of the library system software. These variables are useful in holding the critical information of key components of the library system. These variables are essential since they are going to assist in writing a flexible program that is going to hold data temporarily until it’s time for execution.
A key is a unique identification used to identify items in the library inventory. The keys should be unique and different from others for appropriate identification. The keys that are going to be used in the design of the LMS include:
- B123 for books search
- D123 for DVD’s search
- J123 for journal search
- O123 other related library material
The keys used are ranges and the ones listed are the starting limit for each category. Each category will be listed from the initial key as listed. From this unique key identifiers, all operations are able to be conducted on the inventory with ease.
Range refers to the upper and lower limits for possible variable values. The values for the
Variables should not exceed the range so as to avoid the values to be out of range hence not considered obsolete.
The range that are going to be used include;
- the upper limit
- lower limit
The upper limit will provide the maximum limit a value can reach and exceeding that value will make the value outmoded. The lower limit will provide the threshold to which the values of the variables that must reach in order to be considered significant values.
The operation the Library should be able to hold at least 1500 different course books, 1200 journals, 500 DVD’s or any other storage devices so as to fully and efficiently serve it users. This library system is developed for Kent Institute and since there are not many users the above number of items of the library should be adequate for the normal working of the library.
Operations conducted by Library System
The operations conducted by the library should include the normal functioning of the library and some additional features since the process has been automated (Taieb, F. 2017, 23) The normal operations include;
- A book or any other library material should be added to the library with a unique identification number and the shelf to where it is place properly indicated and put with proper categorization.
- issuing of books and other library related tools to the authorized users of the library. The users should be legible and should not be having other withheld library materials.
- The Library Management System should provide a search method for the users to check for what they might be looking for in the library. The search should be effective and provide the users comprehensive information about the items searched for.
- The system should keep track of the items given out from the library. Their issuing and return date should be properly indicated and a means to remind the user of the deadline should be put into place. This will reduce the overstaying of items by an individual having a wanted library item.
- The library system should facilitate other administrative activities such as data processing and inventory processing.
Algorithms required
For the library operations to be performed effectively, there are some algorithms that must be put in place in the Library system. These algorithms are the ones responsible for smooth working and automation of library processes and operations. The algorithms that are going to be put into place include;
- Sorting algorithm
- Searching algorithm
- Inserting algorithm
- Deleting algorithm
- Merging algorithm
The first algorithm is the sorting algorithm. What this algorithm solely does is put the essentials of a list in an order. By order it means that the order must be sensible. The list must be ordered either numerically, ascending, descending order or any other method that makes values to be acquired with ease.
Without sorting, the process of acquiring something from a myriad of the rest will be a cumbersome job. Though sorting also is process, it is preferable since after sorting items can be acquired with simplicity. The best specific sort algorithm is the quick sort algorithm. The time complexity for quick sort is O(log n) in the best case scenario and O(n^2) for average case. Average case is considered the best performance for most inputs hence considered the fastest algorithm. In this library case, a sorting algorithm is very important in acquiring an item from it. Taking an instance of searching a book from an unsorted library, getting it would be a very tiring process (Byrne, B. 2013, 67). A sorting algorithm is going to assist in the arranging of books in the shelf for easy accessing and retrieval. Whichever the method the algorithm would have sorted the books, it will be easier accessing it compared to going through all the books to get the one an individual want.
Sorting will have reduced the process of looking for a book in the library or any other material. But the search algorithm is important in getting the information of the precise location of a book or any other item. A search algorithm is any algorithm that solves the searching problem. The algorithm uses the information provided to give out the exact location of the object looked for. The best specific search algorithm is the binary search algorithm. This algorithm works in a way that it divides a list in two halves. The search list must be sorted first for the search effective. The search compares the element searched for with the element at the middle of the list. This process divides until the element searched for is found. The binary search is effective because it has a time complexity of O(log(n)) for each search of a list. In this library case, the information must be first fed into the computer regarding the information of the items. If the item exists, the algorithm points out the location and if it is not available, the algorithm saves the time for the seeker in going through the shelves. This makes the algorithm be important in use in the library system.
Inserting algorithm adds a new record to list. The algorithm is very important to the library system. Items in the library are continually added for studies use. A method of adding the information to the system must be put in place to enable the other algorithm of sorting and searching to access it and ease the process of using the library. The algorithm will ease the process of recording information about an item and integrate the items information with the other.
Deleting information is an inevitable process since when information becomes invaluable, it has no value to the user and hence its flooding of data to the memory of the computer is not necessary. Deleting algorithm removes an item from the inventory and hence when a user looks for it, they are going to be told directly that the item was removed from the inventory. The algorithm is important in the library system since it is going to save on space memory by removing data of items that are not required in the library.
Merging algorithm is an additional algorithm that is essential in the working of the library system. What this algorithm essentially does is combine items from the same sorted list. If a librarian finds there are some items that need to be merged in case of a request by a user, the algorithm will come in handy in such scenarios. Items requested by a class or course from different categories can be merged and lent out from the library hence ease the process of combining the items together (Toso, R. 2015, 18).
For another university with the increased number of users as per the data provided, the system would not be effective since it was designed for a smaller institution. With the increased number of users, the system would require a complex system with more over an increased sized library which can hold a large number of library items for the gargantuan number of users. This will mean that the library will have more librarians and more inventory. The library system should have a larger database to hold the inventory information and borrower’s details. The system requirements should be different from the previous system since the new system must have faster software and effective hardware. The speed for the machine should be able to execute information fast since the system will be serving a large number of users.
Conclusion
In conclusion, data structures assist in the organization of data in the memory of a computer for faster access. Algorithms play a great role in realizing the operations run by a system. For this case, the realization of the library system was made by the use of several algorithms that are mainly used in data structures. Library system automates operations in the library that require a lot of manpower to perform. Large institutions require complex systems for operations of their activities. More space and computer speed with specific type of hardware are required for complete realization of tasks.
References
Michalewicz, Z., (2013) Genetic algorithms+ data structures= evolution programs. Springer Science & Business Media.
Zhang, M., Zhu, J., Zou, Y., Yan, H., Hao, D. and Liu, C., (2015) March. Educational evaluation in the PKU SPOC course data structures and algorithms. In Proceedings of the Second (2015) ACM Conference on Learning@ Scale (pp. 237-240). ACM.
Taieb, F., Stevens, B.H. and Coughlin, R.E. (2017) Urban ananlysis for branch library system planning. Greenwood publishing company (1972).
Byrne, B.M. (2013) Structural equation modeling with LISREL, PRELIS, and SIMPLIS: Basic concepts, applications, and programming. Psychology Press.
Toso, R.F. and Resende, M.G. (2015) A C++ application programming interface for biased random-key genetic algorithms. Optimization Methods and Software, 30(1), pp.81-93.
Zhang, X., Tian, Y., Cheng, R. and Jin, Y. (2014) An efficient approach to nondominated sorting for evolutionary multiobjective optimization. IEEE Transactions on Evolutionary Computation, 19(2), pp.201-213.
Business Development
I have seen through my experience and have heard from many that management skills and knowledge is necessary in today’s world. Due to the impact that Globalization had on the world and our lives, having management skills and learning will enable one to have an impressive working career (Ganiron 2014). Management courses are generally designed in such a way that students and professionals both can learn from them (Heagney 2016). All companies, be it small, medium or large, need managers to keep their business running smoothly. The trend of entrepreneurship has emerged in recent years (Burns 2016). People now are more interested in running their own business rather than working for other companies. Companies like Google Inc. too, encourages entrepreneurship among their employees (Drucker 2014). Considering these aspects I had decided that after the completion of my school I will join a management course that will enable me to develop skills that are needed for entrepreneurship and managing projects. Having decided that, I took admission in such a course that focused on developing skills that will enable me for entrepreneurship, intrapreneurship and project management in general. During the tenure of the course, I learnt many topics and aspects, many of my existing skills were honed and some skills that we will need in my career were instilled within me. The whole course was divided into several units and the present unit is about skills and attributes needed for project management for business development.
The present unit that is being discussed here is about the tasks as well as the decisions that surface during the life of an entrepreneur. Through this lesson it seemed to me that students like me will develop capabilities that will help us in managing projects in different organizations as well as a self-employed individual. The lesson mainly gives us the ability to align the process of project development to the main views and values of the organization so that a sustainable project management can be carried out. When the lessons started, I was introduced with the basic concepts and ideas about project management and entrepreneurship. I was then introduced with the different approaches to project management that aims to handle the initial stages of project or idea development (Kerzner and Kerzner 2017). The idea of lean startups where companies invest smaller sum of money at the initial stages to see if the venture is a success or not as well as ideas about Business Model Canvas which enables an entrepreneur to determine the key aspects of the company, like, the suppliers, resources, key channels, key activities, cost structure of the company and determine if undertaking a new business venture is viable or not, were introduced (Mason and Brown 2014). The aspects that are social driven for a manager like teamwork, leadership and managing stakeholders, were also introduced in the course. In the later part of the units I learned about the process of project plan development. The key skills that I learnt throughout the lessons were teamwork, problem solving, communication, critical thinking, analysis and independent work. Throughout the process I was continuously encouraged to think outside the box and hone the skills that have already been attributed to me.
From the learning module, I gathered many theoretical and practical knowledge and skills. Moreover, I acquired some characteristics that changed my viewpoints about many aspects regarding the smooth operation of organizational management and project management. Organizations may face several problems in its life cycle. There could be shortages or resources, there could be a lack of fund, suppliers and key stakeholders might create problems (Kloppenborg 2014). In an enterprise, the role of a project manager may be played by three personnel, the Entrepreneur, the Intrapreneur and the manager. The difference between them is slim but significant. An entrepreneur, as I gathered, is a person who takes the sole risk while handling a project as it is upon him that the success or failure of the project as well as the company depends. An Intrapreneur on the other hand is the risk taker but not the sole risk taker in the whole project. He is working as an employee of the company but is responsible for the planning and execution of the product. If the product fails he will also suffer some loss. Google Inc. encourages this kind of entrepreneurship where people work for the organization, give new ideas and develop the. People who give the idea have a small share in the income that the project or product will generate thus binding that person with the project and making them interested in the project. A manager on the other hand is only an employee. While managing a project he has nothing at stake and no risk has been taken by him. If the project fails, he still goes home with his salary at the end of the month. In case of most small and medium enterprises, the sources and funding is limited, thus the idea of entrepreneurship and intrapreneurship has become extremely popular.
The part one of the unit gave me clear views about the fundamental ideas of Project management and entrepreneurship (Mason and Brown 2014). I learned that project management is mainly concerned with initiating a project plan, planning all the steps that will lead to the successful completion of the project, execute the project according to the plan, controlling the outcome, evaluating the results and finally closing the project within the time constraint given. It is the job of an entrepreneur to execute the whole project in a timely manner (Drucker 2014). A successful entrepreneur is well aware of the risks that the project posits and work around that to achieve maximum result (Zahra and George 2017). This is the first learning that we received during our course. In the second part of the course, I learned about different business models and plan execution methods. The lean start up business model gave me the knowledge of the ways to develop and execute a plan that has limited budget and resources. While working in companies that are highly innovative and goal oriented, this skill is extremely necessary (Blank 2013). Even in case of setting up my own business as I intend to do, this skill will help me start a business even if there is a small amount of fund available for the start-up. The learning of Business Model Canvas is especially helpful in creating the initial plan for a project execution (Meredith, Mantel and Shafer 2017). The model gives a clear view about all the important aspects that need consideration before a project execution plan is created. It gives a comprehensive picture of the key partners and suppliers that the organization have, the key activities that are required to deliver the intended, the key resources that are available in the organization, the proposed deliverable as per the organizational values, customer segments, the costing it will incur and the profit that it will generate (Crawford 2014). With this tool I, as an entrepreneur will be able to analyze the current situation of the business, the potential risks and threats posed by the new project and the possible outcome that I might hope depending on those facts. If I am working for any company, they will be able to use my skill to determine whether the proposed project is worth taking or not (Martin, McNally and Kay 2013). The two project management methods that I learned were Minimum Viable Product and Agile Project Management. The Minimum Viable Product is development of products that have just enough features that will satisfy the customers at the initial stage (Serrador and Pinto 2015). In Agile Project Management execution, first a trial or beta version is introduced to the market that is called the Minimum Viable Product (Conforto et al. 2014). The use and feedback from the customer is analyzed to determine the necessary changes that has to be made. Finally, a new and revised product is introduced that contain all the features that will make the product a success. This management process is good for long term projects and where the funding is limited. The organization does not need to invest a lot of money to create a product that may or may not work (Joyce and Paquin 2016). The organization saves time and money and the workers save labor. Learning about teamwork and leadership increased understanding within me. During the course my leadership qualities increased as did my team work. Project plan development gave me practical knowledge about the actual work. Learning about the different steps that I would have to follow to create a successful project plan gave me confidence that I will be able to plan a project successfully in future (Kerr, Nanda and Rhodes-Kropf 2014). In the course tenure many exercises were given that required teamwork, leadership and planning.
At the time, when I joined the course, I was feeling hopeful as well as apprehension because I was not sure about the outcome of the course. As the course went on, and I learned those things that will help me in future career prospect, I started to feel happy. I grew more confident and assertive in my approach. I developed leadership qualities and felt surer of the decisions that I took. Due to team work activities I learned different perspectives and how to handle conflict in a team. Now with the completion of the course, I have strong faith in myself and I truly believe that I will be able to take up entrepreneurial work easily. The expectations that I had from the coursework were fulfilled completely. Every aspect and outcome that the coursework described were completed.
The decision of learning project management and entrepreneurship is did not come suddenly to me. I wanted to achieve some skills and qualities that will help me in my future. After much discussion with people and deliberation I felt that this course will suit me best. From the beginning I have thought about running my own organization someday. For that I needed entrepreneurial skills. Other skills that I needed were leadership capabilities and understanding the team dynamics. All of these I learned through the course. There are other skills that are needed to successfully run a business. Skills like decision making, problem solving, analyzing any situation, communication and tackling problems that come suddenly. The negotiation skills that I acquired is extremely helpful and was one of the goals that I had in mind when I first started this course. Negotiation is a procedure that we go through every day. In organizations too, regular negotiations take place. During the execution of any project, the organization negotiate with the suppliers, the investors and try to find a common ground that will enable all of them to work together towards the execution of the process. In the project planning lessons we were taught about risk management. It is extremely related to organizations as well as our everyday life. Another skill that I wanted to learn was better leadership. I have always felt that better leadership can change scenarios that otherwise seem impossible to handle.
During the conduct of the course, many of my expectations were reshaped. When I started, I was expecting a comprehensive course where I will receive broad overview of the concerned topics. As I continued with the course I realized that that was not what the course was about. The course offered a detailed and in-depth knowledge about the topics as well as practical scenarios and activities that enabled me to relate the theory with real incidents. Now that I have learnt that the expectations that I had about the course has changed. Now, I believe that it will create a true entrepreneur out of me.
As conclusion, I
can say that this course has instigated a genuine drive to learn more about
Entrepreneurship and Project Management. I intend to take an advanced course to
learn about them in more detail. Learning more about the topic will give
credibility to me and also the organization I am working with.
References
Blank, S., 2013. Why the lean start-up changes everything. Harvard business review, 91(5), pp.63-72.
Burns, P., 2016. Entrepreneurship and small business. Palgrave Macmillan Limited.
Conforto, E.C., Salum, F., Amaral, D.C., Da Silva, S.L. and De Almeida, L.F.M., 2014. Can agile project management be adopted by industries other than software development?. Project Management Journal, 45(3), pp.21-34.
Crawford, J.K., 2014. Project management maturity model. Auerbach Publications.
Drucker, P., 2014. Innovation and entrepreneurship. Routledge.
Ganiron Jr, T.U., 2014. The impact of higher level thinking on students’ achievement toward project management course. International Journal of u-and e-Service, Science and Technology, 7(3), pp.217-226.
Heagney, J., 2016. Fundamentals of project management. Amacom.
Joyce, A. and Paquin, R.L., 2016. The triple layered business model canvas: A tool to design more sustainable business models. Journal of Cleaner Production, 135, pp.1474-1486.
Kerr, W.R., Nanda, R. and Rhodes-Kropf, M., 2014. Entrepreneurship as experimentation. Journal of Economic Perspectives, 28(3), pp.25-48.
Kerzner, H. and Kerzner, H.R., 2017. Project management: a systems approach to planning, scheduling, and controlling. John Wiley & Sons.
Kloppenborg, T., 2014. Contemporary project management. Nelson Education.
Martin, B.C., McNally, J.J. and Kay, M.J., 2013. Examining the formation of human capital in entrepreneurship: A meta-analysis of entrepreneurship education outcomes. Journal of Business Venturing, 28(2), pp.211-224.
Mason, C. and Brown, R., 2014. Entrepreneurial ecosystems and growth oriented entrepreneurship. Final Report to OECD, Paris, 30(1), pp.77-102.
Meredith, J.R., Mantel Jr, S.J. and Shafer, S.M., 2017. Project management: a managerial approach. John Wiley & Sons.
Rasmussen, E.S. and Tanev, S., 2015. The emergence of the lean global startup as a new type of firm. Technology Innovation Management Review, 5(11).
Serrador, P. and Pinto, J.K., 2015. Does Agile work?—A quantitative analysis of agile project success. International Journal of Project Management, 33(5), pp.1040-1051.
Zahra, S.A. and George, G., 2017. International entrepreneurship: the current status of the field and future research agenda. Strategic entrepreneurship: Creating a new mindset, pp.253-288.