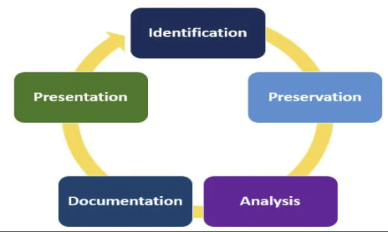
Introduction.
In this report outlines two processes of the 5 steps of digital forensic investigation. The two steps to be discussed in this report includes preservation and analysis.
Preservations
Digital forensic preservation is the vital second stage because it secures evidence validity through court standards. Accurate preservation of all laptop data at the University of Sunderland’s Cyber Crimes Unit (CCU) will protect the investigation against charges of evidence tampering of missing person.
Digital evidence preservation involves making precise duplicates of evidence while ensuring no modifications occur to original storage devices(Guttman et al.,2021).The ACPO Good Practice Guide for Digital Evidence establishes that any court-dependent data storage media should not change actions performed by investigators(Karagiannis and Vergidis,2021). Therefore, with all established standards, all collected exhibits must inform the collector of the evidence required to avoid tampering during preservation, transportation, and analysis.
The basic method in hard drive preservation requires making an exact copy, known as a forensic image, of the entire original storage device(Kirmani and Banday,2024).Forensic investigators can study data duplicates from a duplicate image file without harming original evidence sources. Three popular tools for forensic image creation include FTK Imager, EnCase, and dd (which functions in Unix/Linux systems).
Figure 2: Showing an image of the FTK imager.
Hashing functions as a vital mechanism that serves the preservation process. Data through cryptographic hash functions creates distinct values, which MD5 or SHA-256 functions generate for specific data collections(Sinha and Prayesi,2025). A hash value calculation occurs before and after imaging so analysts can confirm that the data remains untouched. The consistency of hash values determines if evidence contents have suffered tampering and remained intact. The preservation of evidence relies on hashing since it preserves data integrity(Prasanna and Premananda,2021).
Law enforcement agencies use SHA-256 algorithms to create distinctive files and drive fingerprints, which can verify that analysis or imaging processes have not introduced changes. Modifying a single bit or any other type in the data results in a different hash value, indicating data tampering(Reddy et al.,2021).An investigation process for verification allows digital evidence to remain authentic while being court-admissible, thus establishing trust throughout forensic examinations.
A detailed chain of custody system requires strict implementation because it serves as a documentation and tracking mechanism. The evidence-handling record has to include information about stakeholders, their activities, and the time of transfer activities when evidence moves from one person to another(Patil et al.,2021). The log function serves to establish evidence integrity, which becomes pivotal court evidence to verify the evidence’s authenticity.
Digital forensic research now focuses heavily on automation and automated preservation techniques with specific applications in cloud systems (Malik et al.,2024). Under traditional circumstances, the acquisition of physical access continues to hold primary importance for events like laptop seizures. The maintenance of evidence integrity depends heavily on write-blocking methods, which use hardware and cinderblock any write operations on storage media (Jarrett and Choo,2021).
Digital evidence needs preservation because it establishes authenticity while maintaining its integrity, ensuring legal admission. Forensic investigators will follow established methodologies from the EC-Council and ACPO, enabling them to proceed with the analysis steps based on valid evidence.
3.0 Analysis
Digital forensic analysts use the analysis phase to study preserved data to find meaningful details that assist the investigation. The CCU forensic analysts must analyze the computer hard drive image to find information regarding the lost person’s whereabouts while checking for their recent activities and past communication records.
The EC-Council explains that forensic analysis requires a verified forensic image to be examined through specialized tools in a controlled environment(Selim and Ali,2024).Analysis of the forensic image guarantees the preservation of unmodified original evidence. Digital evidence examination relies heavily on Autopsy X-Way forensics and Access Data FTK as standard forensic analysis tools. The steps of analysis applied the following steps.
Data triage: Analysis starts with data triage, where analysts prioritize files and directories showing potentially relevant data. Investigators mainly target documents and emails, internet browsing histories, and communication program activities during their analysis(Malach et al.,2025).Finding major data includes keyword searching and timeline analysis, well-known analytical tools.
Keyword searching: Specific keywords serve as search terms to examine files and unallocated space during investigations.
Time Analysis: The subsequent step uses timeline analysis to create a sequence of user actions. Timings from file system events and software system logs allow investigators to follow chronological patterns that expose important behaviors during pre-incident activities.
Artifact recovery: Autopsy provides recovery among different data sources.This enables cybersecurity practitioners to access and review user-deleted items and records stored throughout applications, such as live chat logs, web browsing activity, and user authentication events(Bhattacharya,2023). The automated reconstruction process can be accomplished using Autopsy with FTK as a supporting tool.
Documentations of the records: Analytical activities and tools are implemented, and all recorded observations need to be properly documented by analysts. Through these procedures, the process becomes transparent, reproducible, and court-admissible. The analysis requires absolute accuracy and integrity to generate accurate finding admissible in court of laws (Huynh‐Ba,2022).
Evidence analysis demands the preservation of its original state at all times. Evidence examination requires complete written documentation about the tools, all steps performed, and recorded observations. Research documentation helps investigators recreate their work steps and gives legal proceedings greater conviction (Ali et al.,2022).
Analysis of volatile data consisting of RAM dumps and system logs proves important for supplying critical insights into whether the missing individual was active on particular programs or websites during their last usage period(Varshney et al.,2024).Metadata analysis provides vital information about file development changes, which helps detect repetitive actions that could show movement patterns.
Recent study has emphasized on artificial intelligence and machine learning apply to upgrade analytic competencies. Machine learning algorithms assist with detecting questionable patterns inside extensive data sets. The ACPO guidelines, transparency combined with well-documented processes is a requirement in addition to court-cross examination readiness(Hamid and Rahman 2024). For reliable analysis to occur, analysts need to display objectivity, which means they should interpret data unbiasedly while delivering findings that lack personal opinions.
4.0 Conclusion
The analysis of the two steps should reveal a critical data which can help in identify the exact location of the missing person. Deconstruct every possible information and ensure accurate recovery and the interpretation of the results of the exhibits. Moreover, document every aspects of the findings which will help in further investigation by the legal teams.
5.0 References
Ali, M., Ismail, A., Elgohary, H., Darwish, S. and Mesbah, S., 2022. A procedure for tracing chain of custody in digital image forensics: A paradigm based on grey hash and blockchain. Symmetry, 14(2), p.334.
Bhattacharya, S., 2023. Comparative Study of Proprietary and Open-source Software used in Recovering Volatile Data (Doctoral dissertation, University of Technology).
Guttman, B., White, D.R. and Walraven, T., 2022. Digital evidence preservation. NIST Interagency Report.
Karagiannis, C. and Vergidis, K., 2021. Digital evidence and cloud forensics: contemporary legal challenges and the power of disposal. Information, 12(5), p.181.
Kirmani, M.S. and Banday, M.T., 2024. Enhancing Reliability During Physical Memory Forensics: Strategies and Practices. SN Computer Science, 5(1), p.201.
Sinha, M.K. and Prayesi, K.P., 2025. Hash functions and message digest. In Next Generation Mechanisms for Data Encryption (pp. 47-63). CRC Press.
Prasanna, S.R. and Premananda, B.S., 2021, August. Performance analysis of md5 and sha-256 algorithms to maintain data integrity. In 2021 International Conference on Recent Trends on Electronics, Information, Communication & Technology (RTEICT) (pp. 246-250). IEEE.
Reddy, G.P., Narayana, A., Keerthan, P.K., Vineetha, B. and Honnavalli, P., 2021. Multiple hashing using SHA-256 and MD5. In Advances in Computing and Network Communications: Proceedings of CoCoNet 2020, Volume 1 (pp. 643-655). Springer Singapore.
Patil, R.Y., Patil, Y.H., Bannore, A. and Ranjanikar, M., 2024. Ensuring accountability in digital forensics with proxy re-encryption based chain of custody. International Journal of Information Technology, 16(3), pp.1841-1853.
Malik, A.W., Bhatti, D.S., Park, T.J., Ishtiaq, H.U., Ryou, J.C. and Kim, K.I., 2024. Cloud digital forensics: Beyond tools, techniques, and challenges. Sensors, 24(2), p.433.
Jarrett, A. and Choo, K.K.R., 2021. The impact of automation and artificial intelligence on digital forensics. Wiley Interdisciplinary Reviews: Forensic Science, 3(6), p.e1418.
Selim, A. and Ali, İ., 2024. The Role of Digital Forensic Analysis in Modern Investigations. Journal of Emerging Computer Technologies, 4(1), pp.1-5.
Malach, A., Wudali, P.N., Momiyama, S., Furukawa, J., Araki, T., Elovici, Y. and Shabtai, A., 2025. CyberShapley: Explanation, prioritization, and triage of cybersecurity alerts using informative graph representation. Computers & Security, 150, p.104270.
Huynh‐Ba, K., 2022. Analytical data and the documentation system. Analytical Testing for the Pharmaceutical GMP Laboratory, pp.251-315.
Huynh‐Ba, K., 2022. Analytical data and the documentation system. Analytical Testing for the Pharmaceutical GMP Laboratory, pp.251-315.
Varshney, S., Fatima, H., Dubey, P., Upadhyay, A.K. and Tyagi, S., 2024. Plug and Play Device for In-Depth RAM Data Repository. International Journal of Performability Engineering, 20(8).
Hamid, I. and Rahman, M.M., 2024. A Comprehensive Literature Review on Volatile Memory Forensics. Electronics (2079-9292), 13(15).
