Introduction
LinkedIn is a social networking site utilized for business community. The objective of the site is to ensure members to engage and create networks of individuals the know and trust professionally. The LinkedIn registered user interface profile, enhances skills, employment history and academic profiles with professional network news feed and reduced number of customized modules. Membership is free for the new members. Unlike other social platforms LinkedIn ensures connections to have a prior relationship. The social platform was founded and launched in May 2003 by Reid Hoffman a former employee of PayPal. In the current digital LinkedIn has garnered over 300 million members in over 200 countries.
History of LinkedIn
LinkedIn is a business oriented platform that connects users through job opportunities being posted on the website. The company was founded in 2002 by a former employee of PayPal Red Hoffman where it was officially launched in May 5the 2003.it is one if the oldest mainstreams social platform that connects professionals with consumers in the job market. in 2004 he company added the ability to upload address book such that one would invite colleagues to the platform and made connection with American Expresses to offer promotion in service for the clients. In the following year LinkedIn introduced the addition of jobs descriptions where it garnered more users. In addition it launched the public profiles . in the same year it recorded its first profit. In 2008 it extended ist boundaries beyond the US region. With over 400 million users currently LinkedIn is a platform that has transformed over the years. It is also linked to other several platforms such as SlideShare, Connected and CardMuch with several other apps.
LinkedIn data breach
LinkedIn experienced a cyber-attack in 2012where over 100 million accounts were compromised. The passwords and emails were hacked and the third party intruder sold the data online. Since LinkedIn is a social media platform of over 300 million users globally any threat risks the private and professional details being exposed. The site was breached by the exposure of hashed passwords of about 117 million accounts in a span of several years by Russian cybercryminals. The data was decoded quickly and provided in the social platform illustrating that LinkedIn technique of storing passwords was cryptographically insecure (FRANCESCHI-BICCHERAL, 2016).
Securing data issues have existed over several years. Securing passwords in plaintext poses an immediate and uncontrollable risk in case of an attack. A data breach is of great disaster if the encryption keys are secured on the same database servers as the data being secured. Majority of websites prefer the technique of hashed passwords. LinkedIn like other web services utilizes the hashed passwords. The organization sends consumer information through a SHA-1 hash function. However LinkedIn organization projected that the breach was done by the SQL injection attack which was reported by some several media agencies. Despite the speculation LinkedIn company confirmed the attack the following day (GOLDMAN, 2012). Speculations stated that the exposed passwords were about 6.5 million passwords but in the year 2016 the full report was exposed online of account of over 110 million user passwords were breached. The source of the breach was compromised through the hash functions to expose the password plaintexts.
Cryptography of hashing the passwords
Hashing passwords technique is achieved through password input of a reasonable length and provision of a fixed length output resembling a random string. SHA-1, the actual technique utilized by LinkedIn, was illustrated in the early 1990s by the company. the technique is utilized to code up to 264 bit input through a 160 bit data digest. The technique failed to be implemented in the LinkedIn website through inclusion of Salt (various numbers unique to each consumer) and alternatively securing hashed passwords direct to the database. The SHA-1 functions repetitively padding the message and disseminating it to 512-bit blocks and channeling it via a sequence of logical functions. In addition the data van be accessed in an official Secure Hash publication. Although it provides an illusion of security by SHA-1, the LinkedIn technique of securing passwords was critical and insecure. The system was vulnerable to rainbow table attacks by utilizing the unsalted hash functions (LinkedIn Revisited, 2016).
Rainbow tables
A rainbow table attack collects an already tabled list of passwords to the data designs known as hash chains. The calculations of these hashes have already been pre-determined. Rainbow tables utilized the reduction functions where individual hashes are mapped back to the plaintexts. This provides a time memory tradeoff, which involves the sacrificial of time on memory cost. By the application of alternating series of hashes and reducing the functions the intruder was able to tabulate chains of hashes and plaintexts.
Pi hash (P) Ci Red (C) Pi + 1….Pn
Only the initial and the final elements of the chain P0 and Pn are secured in the memory, thus highly reducing the storage memory needed to secure a great amount of passwords. With the lack of salt function the attacker was able to apply reduction and hashing function up to the endpoint on the chain and retrieve the initial plaintext and the linked hash chain till the user password was achieved. The vulnerability easy due to the fact of weak choice of passwords by the end user. Through the data leaked by the attacker it was noticed that most users used the combination of “123456” as their passwords (KRAWCZYK, 2010).
The utility of salt elevates the simulation cost needed for a strong rainbow table. For instance the entry 123456 utilizes hash function of the similar value. However, addition of 2-bit salt at the initial point of the password the intruder is left with the 2 2 values leading to the length of the has chains in a rainbow table.
[image source: google]
Possible solution for Rainbow attack
The choice of Linked in password protection was relatively less secure apart from the storage of plaintext. However the storage of passwords in cryptography technique is the most significant method and a complex task for an administrator frequently utilizing the non-cryptographically security structure and hash functions. Logically the cryptographic hash functions should cater for the cost of simulating the hash passwords and make sure that the cost aligns with the microprocessors (CAPE-55, 2015).
In the history of cryptography UNIX cryptography function was first achieved in 1970s to secure about four passwords per second utilizing the hash function on a specific hardware.in the last two decades the utility had risen to 200,000 crypt processes per second. By the utilization of the GPU-driven parallel simulation, the intruders had the ability to hack the SHA-1 hashes per second. This underrates the requirement of cryptographic hash functions which must be able to resist the brute-force attacks. In order to achieve the security of passwords, the hashing functions should make sure the simulation cost of password hashing is increased such that a third party trying to breach the site sees it as a time consuming process.
Solution by LinkedIn
LinkedIn immediately responded by the introduction of salted and hashed the consumers passwords. In addition the company stated that the protection tools will extend to email and dual factor authentication. The two factor authentication provides a secure and easy to implement, cost effective strategy with a Google Authenticator. It is implemented through an existing servers and the present authentication back-end in order to add a two factor authentication. In utility the user is needed to input a 2-factor characters to authenticate the credentials.
From another dimension LinkedIn would have utilized several possible solutions. In this section the possible measures LinkedIn would have implemented to secure the privacy of passwords.
Key derivation Functions
A key Derivation Functions involves a non-random source of password and evaluates a cryptographically secure hidden key from the input. Several systems of data security utilize the Key Derivation Function in place of the hashed functions. The Key Derivation Functions Provides an output key that is unique from a random string of the similar length and will retrieve it from dissemination of corresponding strings. Many KDFs are created from the password input and only a single usage of K as the core PRF (pseudorandom Function) to provide most cryptographic secure PRFs.
On the other hand Key Derivations Key in its single unit is not a secure method to secure inputs and as a results cannot resist a brutal-force attack. The KDF creations utilized for such password hashing will provide a higher cost needed to simulate a password hash. In implementation it involeve the Bcrypt and Scrypt combination to achieve through a technique knowns as Key Stretching. It refers to the utilization of Key Derivations Functions that needs 2k cryptographic process per any hash simulation despite the length of the input. For instance, a A-bit input will need 2k+a processes in any system.
Scrypt
A Scrypt illustrates a same criteria of Bcrypt by utilizing the adoption cost technique to mitigate brute-force attack. Basically a Bcrypt can be influenced by a brue-force attack utilizing a parallel peripheral devices. An improved semiconductor technology will ensure the third party to reinforce several circuits at minimal cost. Hardware such as GPU is designed for a repeated task in password hacking due to the huge amount of circuits ensuring a simulation of expensive inputs to be hashed. Several password hashing processes can be evaluated ever second, therefore minimizing the performance to adapt Bcrypt technique. In this method Scrypt ensures the resist on parallel brute-force attacks by providing time-memory tradeoff costly on both phases.
It ensures the sufficient memory needed to hash the inputs and increase sequentially to the amount of simulations. Scrypt increased memory needs is because of the activities of sumulating and storing in he large number of bits chains utilizing the PRFs. This needs allocation of huge amount of memory positions. The required memory and amount of simulations can be set through the parameters of N and P where the system admins ensure that the hashing cost to several passwords is hard to crack despite the hardware advancements.
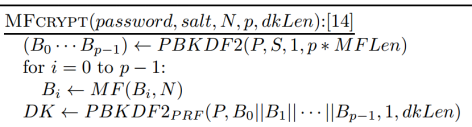
[image source: google]
Bcrypt
Bcrypt is a Key Derivations Function that is adaptive and one would recommend this technique in the storage of passwords for security of data. This king of technique is able to withstand the brute-force attack through provision of resistance and ensure administrators to uniquely identify the sequential internal operations needed for the inpu hash evaluation. The causes the simulation cost of hashing an input therefore ensuring brute-force intrusion hard to crack. Blowfish lays a foundation for the Bcrypt encryption of 64-bit block cipher designed as a 16-round Feistel Network.
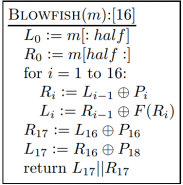
Blowfish structure [image source: Net]
However the minimized round Blowfish poses a vulnerability, a standardized Blowfish block cipher is deemed to be secure. It utilizes the Eksblowfish which considers the consumers cost of simulation as a parameter.
EksBlowfish [image source: Google]
Bcrypt is structured to offer resistance to brute-force intrusion despite the increased speed of the current microprocessors. Therefore it ensures that the administrators elevate the operations to substitute the single input hashes which takes time for simulation.
Collision techniques
Collisions happens when two sets of data is stores in the same location. For this reasons the collision can be mitigated through selection of a different locations which is known as collision resolution. This is recommended in LinkedIn organization to avoid the situation of computational of the passwords. During collision resolution methods algorithms and data designs are utilized to offer two hash keys which are the open addressing and chaining.
Chaining offers two sets of strategies that is the separate and coalesced chaining. Separate chaining refers to the insertion required to position the exact slot and appending to any end point of the list. Coalesced hashing involves a scheme of collision mitigation which is mix part of the separate chaining and open address in a hash platform. it offers a better effort in order to avoid the influence of primary and secondary clustering.
Open addressing
This strategy is utilized to stock up the data straight in the internal array. The technique is based of the probing method. It involves the Linear probing, Quadratic probing and double hashing. The main tradeoff in the strategies is the linear probing which has a better cache efficiency and is responsive to the clustering. Double probing is less efficient and has no clustering while quadratic probing are linked in between the two techniques.
Linear probing
This is a technique one can recommend for the resolution of hash functions by seeking the hash table for a secure location. The efficiency is more critical to the passwords in comparison of other techniques such as double hashing. The data is stored in the next available space in the hash table in the linear probing where rationale is made that the hash table is already to capacity. It is done through searching an empty slot from the initial point of collision. The limitation of this kind is the primary clustering where blocks of information may form a collision.
Quadratic Probing
Its limitation is the complex location of the unfilled slots due to the secondary clustering where elements offer collision.
Double Hashing
This technique involves the idea of application of a second hash function key in a collision. The needs of the technique is that it should ever calculate to zero, and should ensure the slots can be probed.
Two-method chaining
This technique utilizes the two techniques of chained hashing. The Key is entered in a unit two hash tables. It is a scheme that utilizes two separate uniform hash functions f and g to insert another key x keys to a hash table having n chains. The two factor chaining criteria us used to structure effective open addressing hashing method.
Conclusion
The utilization of cryptography security of passwords still is a critical for the data security. Password hashing becomes the last resort in securing consumer data in case of a data breach as the case of 2012 LinkedIn data breach. the utilization of unsalted hash functions provided a platform for the third party intrusion and exposure of over 110 million usernames and passwords. The utility of hash functions such as the SHA-1 is vulnerable and its no longer secure to use in sites due to the vulnerability to rainbow table and brutal-force intrusion. The second options such as the Bcrypt and Scrypt utilizing the combined salts and is relatively safe to enhance security of data and hacking the methods is expensive and time consuming.
Reference
ALABACHI, A. A. (2013). Security analysis of blowfish algorithm . Informatics and Application, Second International Conference .
CAPE-55. (2015). Rainbow Table Password Cracking.
FRANCESCHI-BICCHERAL, L. (2016). Another Day, Another Hack:117 Million LinkedIn Emails And Passwords.
GOLDMAN, D. (2012). More than 6 million LinkedIn passwords stolen.
GOSNEY, J. (2012). Password Cracking HPC .
GOSNEY, J. (2016). How LinkedIn passwords Sloppiness hurts us all.
KRAWCZYK, H. (2010). Cryptographic Extraction and Key Derivation. The HKDF Scheme. International Association of Cryptologic Research.
LinkedIn Revisited. (2016). Full 2012 Hash Dump Analysis.